5 Reasons Why CNAPPs Are Limiting Your Cloud Security

Cloud applications have become the lifeblood of organizations, especially in the past few years of rapid digital transformation. These applications, running in the cloud in physical and virtual servers, containers, and serverless computing, offer unprecedented agility and scalability.
But they also bring new security challenges. Many organizations have turned to cloud native application protection platforms (CNAPPs) to bolster their defenses. While CNAPPs may be built specifically for the cloud, they can only take your security so far.
Your CNAPP tools might be limiting your cloud security. Learn why Zero Trust Segmentation is essential for a comprehensive cloud security strategy.
You should be paying attention to cloud security now
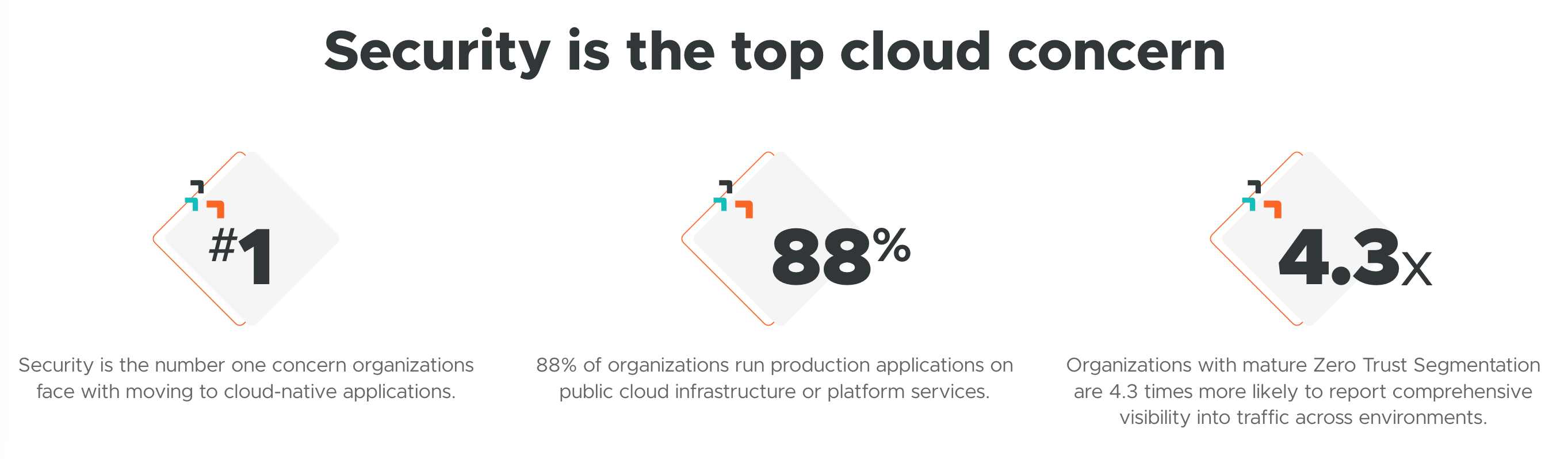
More organizations want to operate in the cloud than ever before to protect profitability and business continuity. In fact, Vanson Bourne research in the Cloud Security Index 2023 found that 100 percent of organizations surveyed are using the cloud, and 98 percent are currently holding sensitive data in the cloud.
Despite excitement about the possibilities of the cloud, threat actors are taking advantage of lax cloud security. Of all the data breaches suffered over the past year, Vanson Bourne found that 47 percent originated in the cloud, highlighting the cloud as a security weak point. Even worse, organizations that suffered a cloud breach in the past year lost nearly $4.1 million on average.
This means it’s more important than ever to pay attention to the cloud security tools you’re using. Organizations deploying CNAPPs specifically may be surprised by their limitations and resulting security gaps.
Why do CNAPPs limit your cloud security?
Recognizing the unique security needs of cloud-native environments, cloud native application protection platforms (CNAPPs) have emerged to address these challenges.
Gartner defines CNAPPs as:
A unified and tightly integrated set of security and compliance capabilities designed to secure and protect cloud-native applications across development and production. CNAPPs consolidate a large number of previously siloed capabilities, including container scanning, cloud security posture management, infrastructure-as-code scanning, cloud infrastructure entitlement management, runtime cloud workload protection, and runtime vulnerability/configuration scanning.
CNAPPs seem like an obvious choice for cloud security — they’re built specifically for cloud environments, integrate with existing security platforms and development processes, and can scale as organizations migrate more workloads to the cloud.
But these features don’t make CNAPPs the best choice for cloud security. They leave security teams with significant challenges when securing the cloud.
5 limitations of CNAPPs
- Security for the cloud — only: CNAPPs focus solely on cloud application security and don’t offer comprehensive protection for applications running on other parts of the infrastructure. This leaves security gaps as workloads travel between different environments and makes it easy for attackers to move laterally through the cloud environment.
- Security siloes due to vendor lock-in: Each cloud vendor’s security tools are local to their platform. For example, an AWS security tool is unlikely to integrate with an Azure security tool. This creates security silos which can be left open to vulnerabilities and slow down restoration after a breach.
- Risky third-party integrations: Integrating with third-party services and applications is common in cloud environments — and is typically named as a top benefit of CNAPPs. However, doing so without proper segmentation and security measures may expose your cloud infrastructure to external threats.
- Not enough to meet compliance requirements: Meeting regulatory and compliance requirements often involves not only securing applications but also demonstrating control over user access and network segmentation, functionality that CNAPPs don’t offer.
- Significant learning curve: Adopting CNAPPs requires specialized knowledge of cloud technologies which may present a learning curve for traditional IT security teams.
Zero Trust Segmentation delivers comprehensive cloud security
While CNAPPs apply only to cloud environments, Zero Trust Segmentation (ZTS) secures all workloads no matter where they live in your network.
ZTS, also called microsegmentation, divides the network into smaller, granular segments, creating a series of secure zones. This means ZTS can deliver precise and flexible security across the entire hybrid attack surface, not just the cloud, by offering a unique security posture for each network segment. Each segment can be tailored with specific access controls, containing lateral movement, and limiting potential damage when breaches inevitably happen.
Starting from the Zero Trust mindset of “assume breach,” ZTS puts a priority on gaining consistent, context-based visibility everywhere, all the time. Using that foundation of visibility, it provides an iterative process to constantly improve security.
5 benefits of Zero Trust Segmentation for cloud security
ZTS addresses cloud security challenges head-on by reducing the risk of network exposure and maintaining least-privilege access across the cloud.
- Real-time visibility: Illumio’s application dependency map provides real-time visibility into traffic flow telemetry across all workloads across hybrid and multi-cloud. Gather insights with an interactive map of application deployments, resources, traffic flows, and metadata. This comprehensive visibility allows you to identify and understand potential threats, anomalous behaviors, and vulnerabilities, ensuring proactive security measures are implemented promptly.
- Flexible security policies: Illumio automatically adapts security policies in response to changes within your cloud environment. As your cloud infrastructure scales and evolves, Illumio ensures that your security measures remain effective, alleviating the burden of manual policy updates and reducing human error in the cloud.
- Microsegmentation for the cloud: Illumio's ZTS capabilities enable you to create granular security zones within your cloud infrastructure. This approach stops lateral movement within the network, contains ransomware and breaches when they inevitably happen, and minimizes the impact of breaches to ensure business continuity.
- Consistent security across clouds: As workloads move across different cloud vendors (e.g., from Azure to AWS), the security from one vendor rarely translates to the next. This creates cloud vulnerabilities and adds more work for your team. Illumio enables a consistent solution for workload segmentation across clouds, avoiding workloads being dependent on standalone, vendor-specific security solutions.
- Easy third-party app integration: Illumio offers a robust third-party partnership ecosystem to seamlessly integrate with various cloud-native services, such as AWS Security Groups and Azure Network Security Groups. This compatibility streamlines the implementation process and allows for consistent security policies across multiple cloud environments.
Get started with Zero Trust Segmentation to protect your cloud environments
The cloud is at the heart of modern business operations, but it comes with unique security challenges. By integrating Zero Trust Segmentation into your cloud security strategy, you can establish a more comprehensive and robust security posture in the cloud.
Contact us today for more information about implementing Zero Trust Segmentation in the cloud with Illumio CloudSecure.
.png)





