Cyber Resilience, CISA’s Strategic Plan, and Zero Trust Segmentation Proof
Cyberattacks are growing more frequent and sophisticated everyday – why aren’t cybersecurity strategies keeping up?
This month’s news coverage focused on solutions to this ever-growing problem: the 2023-2025 CISA Strategic Plan, Zero Trust security strategies, and the efficacy of Zero Trust Segmentation.
Risk reduction and resilience: Cybersecurity’s new north star
With the 2023-2025 CISA Strategic Plan released this month, Illumio’s Andrew Rubin, CEO and co-founder, addressed the importance of the document in the context of today’s threat landscape in his Fortune article, The U.S. is overdue for a dramatic shift in its cybersecurity strategy–but change is finally coming.
According to Rubin, “We’re still hemorrhaging losses to ransomware. It’s clear that the way we’re approaching cyber is wrong–and it’s on all of us.”
He outlines some key ransomware statistics that showcase the implications of the way we currently approach security:
- 649 U.S. critical infrastructure entities were hit with ransomware attacks, according to the FBI.
- Almost 90 percent of all U.S. critical infrastructure sectors were hit by a successful ransomware attack in 2021, according to the FBI’s Internet Crime Complaint Center (IC3).
- More than 76 percent of organizations have been attacked by ransomware, and 66 percent have experienced at least one software supply chain attack in the past two years alone.
- The world will spend nearly $170 billion on cybersecurity in 2022, with nearly $20 billion of that will be spent by the U.S. Federal Government.
Despite the ongoing wake-up calls to cybersecurity leadership in the form of incessant ransomware attacks, Rubin believes “we’re moving much too slowly in a threat landscape that changes faster each day.”
The 2023-2025 CISA Strategic Plan is so important because it acknowledges what we’re getting wrong with security but also “outlines a new path forward: one predicated on resilience,” he explained.
“This is an evident and deliberate shift away from the traditional security approaches of keeping attacks out (prevention) and detecting them quickly when they break through the perimeter,” he said. “The traditional security models that we’ve relied on for decades aren’t designed to solve the problems posed by a hyperconnected, digital-first landscape.”
It's inevitable that today’s ransomware and other malware attacks will breach the perimeter and evade detection. Organizations must be ready to meet agile attackers with equally dynamic security strategies. This is what Rubin defines as “the era of breach containment and resilience.”
“Organizations are focusing on isolating and minimizing breaches to reduce the impact and recover much more quickly. We are focusing on enhancing visibility across networks, workloads, endpoints, and critical infrastructure since you can’t defend what you cannot see. Risk reduction and resilience are finally serving as the north star for cybersecurity,” he said.
Rubin sees CISA’s new plan as evidence that the security industry, as well as public and private sector security leadership, are pivoting to meet new realities posed by ever-evolving ransomware and other cyberattacks. He reiterated this view in his comment for the Bloomberg Law article, Nation-Backed Cyberattacks Escalate Push to Bolster Data Shields.
“We all talk about public-private partnership as the whole key to cybersecurity,” Rubin told Bloomberg Law. “The government has to work with private industry, private industry has to work with the government, and I think we’re probably in a better place on that than we’ve ever been. CISA is doing a great job of embedding itself in that conversation, especially recently.”
CISA’s Strategic Plan shows federal shift to resilience-based cybersecurity
Gary Barlet, Illumio’s federal field CTO, also discussed the 2023-2025 CISA Strategic Plan with Grace Dille in MeriTalk’s article, CISA Sets Strategic Plan for 2023-2025, Eyes Unity of Efforts.

The plan is CISA’s first, comprehensive strategic plan of its kind since the agency was established in 2018. Dille outlined the plan's four main goals:
- Ensure defense and resilience of cyberspace.
- Reduce cyber risk and strengthen the resilience of U.S. critical infrastructure.
- Strengthen “whole-of-nation operational collaboration and information sharing” between government and the private sector.
- Unify the agency internally by breaking down organizational silos, growing the value of the agency’s services, and increasing stakeholder satisfaction.
Illumio’s Barlet applauded CISA’s goal to unify the agency. But he also emphasized that the goals will be difficult to achieve without continuous funding and sufficient resources.
“CISA’s goal of agency unification will strengthen information and resource sharing, but without a clear outline of funding priorities, cyberattackers will always be steps ahead while the government runs with weights on its ankles,” Barlet said.
Despite these challenges, Barlet remains positive about the direction of federal cybersecurity as reflected in CISA’s new plan.
“CISA is still a new agency and issuing this strategic plan signposts its commitment to driving change in a huge way,” he said. “I’m excited to see the federal government begin to shift to a resilience-based cybersecurity strategy.”
Zero Trust Segmentation is foundational for true Zero Trust
CISA’s goals for Cyber Resilience are achieved with a Zero Trust security approach. And foundational to Zero Trust is implementing microsegmentation, also called Zero Trust Segmentation.
In fact, security analyst firm ESG found that 81 percent of surveyed security leaders consider Zero Trust Segmentation key to any successful Zero Trust initiative, including Cyber Resilience.
In the VentureBeat article, Why Getting Microsegmentation Right is Key to Zero Trust, Louis Columbus explained how Zero Trust Segmentation works as part of a Zero Trust strategy. He also featured Zero Trust Segmentation insights from a recent webinar with PJ Kirner, Illumio’s CTO and co-founder, and Forrester senior analyst David Holmes, in his piece.
According to Columbus, Zero Trust has become a significant priority for security and business leaders who need a better security strategy than constant “firefights” with ransomware and other cyberattacks. Columbus says that an “assume breach” mindset is driving Zero Trust planning, including the implementation of security controls like Zero Trust Segmentation.
“Traditional network segmentation techniques are failing to keep up with the dynamic nature of cloud and data center workloads, leaving tech stacks vulnerable to cyberattacks,” explains Columbus. “More adaptive approaches to application segmentation are needed to shut down lateral movement across a network.”
But implementing Zero Trust Segmentation can be a challenge. In their recent webinar, The Time for Microsegmentation is Now, Kirner and Holmes offered three key pieces of advice to organizations starting their Zero Trust journey.
1. Start small, create basic policies first, and resist over-segmenting a network.
As Holmes explained, “You may want to enforce controls around, say, a non-critical service first, so you can get a feel for what’s the workflow like. If you did get some part of the policy wrong, you can learn how to handle that before you push it out across the whole org.”
2. Target the most critical assets and segments as they plan to implement Zero Trust Segmentation.
Kirner said Illumio has learned that matching the microsegmentation style that covers both the location of workloads and the type of environment is an essential step during planning.
3. Don’t base segmentation policies on IP addresses.
This is due to the way microservices container architectures are increasing the amount of east-west traffic in data centers.
Instead, Holmes and Kirner advised that organizations’ goal should be defining and implementing a more adaptive Zero Trust Segmentation approach that can continuously flex to an organization’s needs.
To achieve Cyber Resilience, security leaders point to Zero Trust and implementing Zero Trust Segmentation.
“Getting microsegmentation right is the cornerstone of a successful Zero Trust framework,” said Columbus. “Having an adaptive microsegmentation architecture that can flex and change as a business grows and adds new business units or divisions can keep a company more competitive while reducing the risk of a breach.”
Get more Zero Trust insight from Kirner and Holmes in this webinar Q&A.
Bishop Fox: Zero Trust Segmentation stops attackers in less than 10 minutes
A recent ransomware attack emulation performed by Bishop Fox found that Zero Trust Segmentation is a proven strategy for fighting ransomware, especially when combined with endpoint detection and response (EDR) services.
Nancy Liu detailed the emulation’s findings article in her article for SDxCentral, Ransomware Attack Emulation Unveils Effectiveness of Zero-Trust Segmentation.
According to Liu, Bishop Fox’s emulation mapped to the MITRE ATT&CK framework and was based on real threat actors’ tactics, techniques, and procedures (TTPs).
Liu reports Bishop Fox’s key findings, also summarized in the chart below:
- In the scenario with no security protection, the attacker breached all hosts within 2.5 hours in a network without any protection, and all 26 TTPs available to the hacker were executed.
- In the scenario using only EDR, the attacker breached the network in 38 minutes, and 12 of the 13 TTPs available to them were executed
- But in the scenario with both EDR and Illumio Zero Trust Segmentation, the attacker was stopped in only 10 minutes, and 6 of the 8 TTPs available to the hacker were executed.
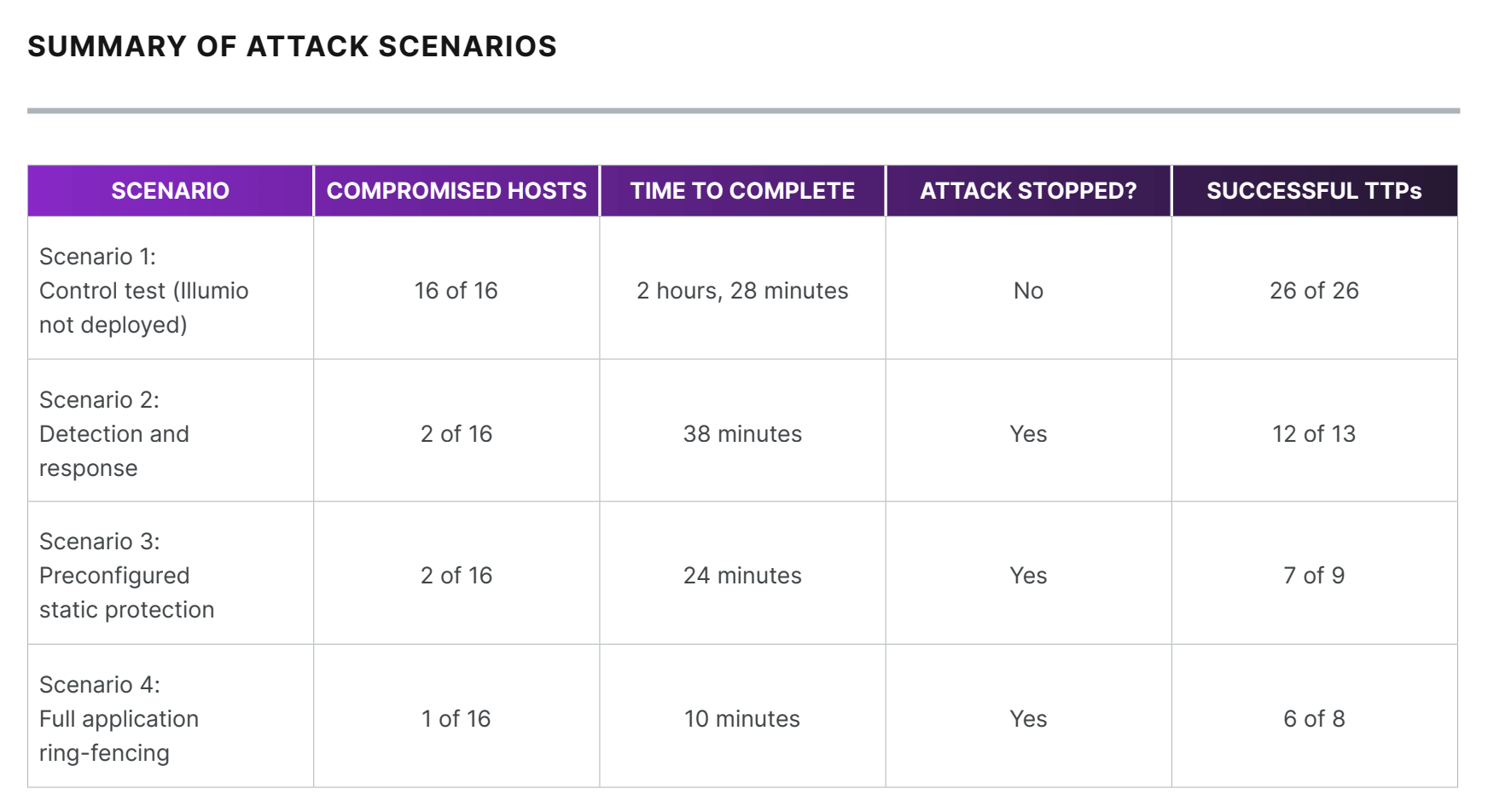
Liu spoke to Trevin Edgeworth, red team practice director at Bishop Fox, for insight into Bishop Fox’s findings. While the amount of time it takes to stop a hacker is important, Edgeworth also points to the ability to limit the amount of TTPs a bad actor can use.
“I would say the measure of the amount of TTPs they’re able to actually get through is a great metric. But the numbers should also not be discounted in that [test]. This was two hours of activities that we were able to reduce to 10 minutes,” Edgeworth said.
As Liu explains, Zero Trust is often described as a “philosophy, an approach, or a security strategy.” But Bishop Fox’s emulation shows that specific Zero Trust controls like Zero Trust Segmentation have real-world, metrics-driven evidence.
Learn more about the Illumio Zero Trust Segmentation Platform:
- Download our in-depth guide on how to achieve Zero Trust Segmentation with Illumio.
- See why Forrester has named Illumio a Leader in both Zero Trust and microsegmentation.
- Learn how HK Electric ensures its impeccable supply reliability of 99.999% by deploying Illumio Zero Trust Segmentation.
- Contact us to find out how Illumio can help strengthen your defenses against cybersecurity threats.
.png)

.webp)
.webp)