Demystifying Containers: What’s a Service Mesh and How Do You Secure It?
Gartner® predicts “by 2029, more than 95% of global organizations will be running containerized applications in production, which is a significant increase from less than 50% in 2023.”*
Containers are a major technology in environments today, and usage is growing exponentially. But this technology also has its own terminology – namespace, pod, CNI plugins, service mesh, among many others – and can be daunting to organizations who are not familiar with it.
With such prevalent use, it’s important organizations understand the technology. In this blog post, we’ll demystify some of the surrounding technology. Specifically, we will break down what a service mesh is and why it’s valuable to containers deployments.

What is a service mesh?
Let’s start with the basics. When we say a service mesh, what do we mean?
A service mesh is a crucial infrastructure layer. It manages communication between services within a distributed application which runs on multiple systems at the same time. A service mesh overlays on top of an existing containers deployment that manages communication between services or microservices.
As applications scale and the number of microservices increase, it becomes challenging to monitor their performance. A service mesh helps with this challenge.
When looking for a service mesh, there are many options available in the market. Here are just a few of the most common you may see:
- Istio
- Linkerd
- Consul Connect
How does a service mesh work?
A service mesh works by inserting a sidecar – a secondary container that runs alongside the main application container within the same pod. This exists independently of the runtime it supports. These sidecars are all connected in the mesh. Once it is deployed, it helps link all the pods together and looks something like the image below.
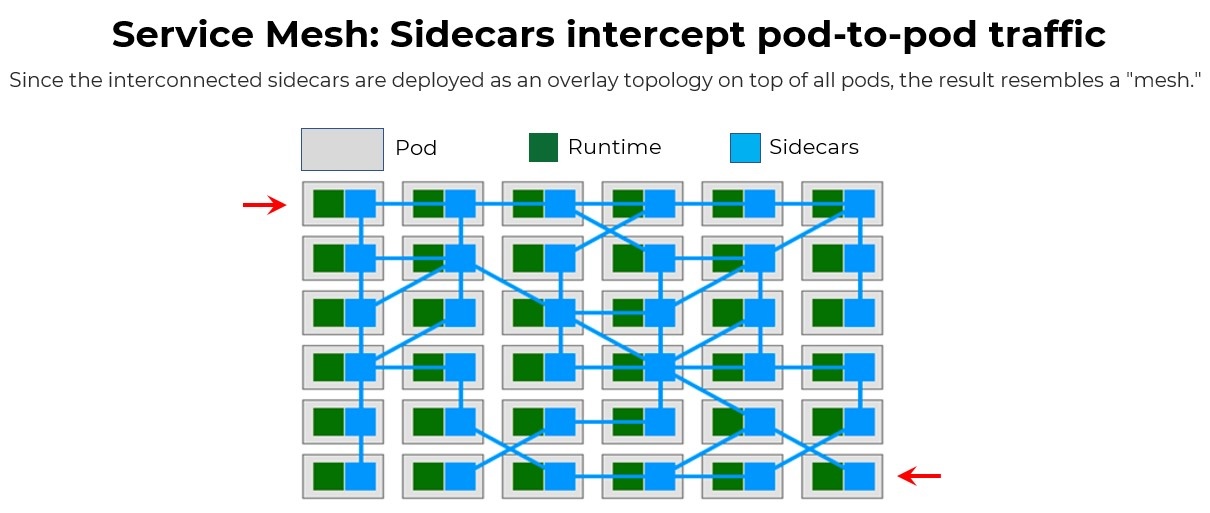
Why use a service mesh?
A service mesh provides key features to help manage a containers deployment. One of the main benefits is how it helps applications communicate.
By managing communications, the service mesh ensures the application it’s supporting can function correctly. It accomplishes this through the following features:
- Service discovery: Discover other services and route requests through the mesh accordingly.
- Load balancing: Distribute traffic evenly across instances of a service.
- Security: Authenticate and authorize access and encrypt data.
- Observability: Collect metrics, logs, and traces for monitoring.
- Traffic control: Use sidecars to get fine-grained control over routing and retries.
What are the cybersecurity risks of a service mesh?
Service meshes are important to help your cloud deployments run smoothly. But they can be a cybersecurity vulnerability. Here’s why:
- Complexity: One of the key benefits of a security mesh is that it adds extra layers of communication and control. This complexity can also add confusion for security teams leading to more security gaps. This makes it easier for attackers to find and exploit weak spots.
- Configuration mistakes: Setting up a service mesh correctly can be tricky. If it's not done right, it can create openings for cyberattacks.
- Limited scope: A service mesh is only for containers, leaving out the rest of the hybrid, multi-cloud system. If any part of this system isn’t protected, it can be an entry point for attackers to spread through the network.
- New technology: Service meshes are relatively new, so there might be unknown vulnerabilities that haven't been discovered yet. Even when they are discovered, it can take time for vendors to build a fix and for your team to implement it.
Protect your service mesh with Illumio Zero Trust Segmentation
Now that we understand what a service mesh is and why it matters, let’s talk about how you can protect it.
When considering your options, it’s critical to not only think in terms of your containers deployment and its underlying technology, but also how this expands out to your hybrid environment.
How can you ensure your entire hybrid multi-cloud is protected from cyberattacks without silos? How do you control lateral movement?
With Illumio’s Zero Trust Segmentation Platform you can:
- Consistently manage security policy: Deploy a mesh to encrypt traffic between pods inside a containers cluster. Then, use Illumio to enforce all traffic in and out of the cluster.
- Prevent lateral movement between clusters: Illumio protects the underlying host and broader hybrid environment. This ensures consistent security policy from the data center to the cloud and containers.
- Proactively protect against attackers: An attacker can bypass the sidecar proxy and send traffic outside of the service mesh. With Illumio, you can stop this by preventing attackers from getting to other workloads.
Contact us to learn how the Illumio Zero Trust Segmentation Platform can help you secure against the next potential cloud attack.
*Gartner, Chandrasekaran, A., & Katsurashima, W. (24 C.E., January 22). A CTO’s Guide to Containers and Kubernetes: Top 10 FAQs. Gartner.com. https://www.gartner.com/en/documents/5128231. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
.png)


_(2).webp)


.webp)