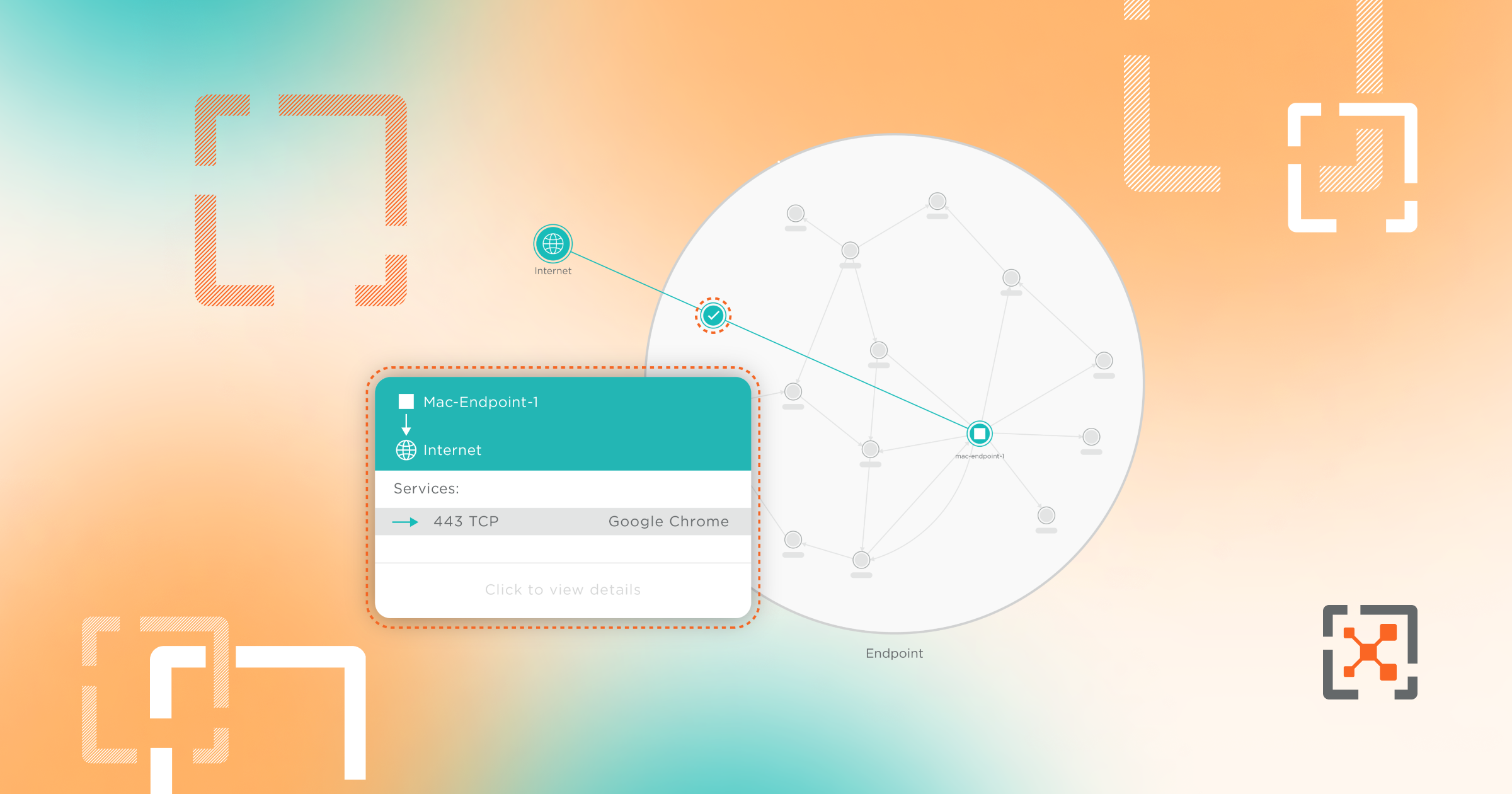
Endpoint
Protect your network from ransomware threats with Illumio's advanced microsegmentation for your endpoints.
.svg)
Related blog posts

The Hidden Flaw in Data Center Security: Endpoint Connectivity
Learn how to stop lateral movement between endpoints and the data center with the Illumio Zero Trust Segmentation Platform.
Your Endpoints Are Talking Behind Your Back
Learn why endpoint security tools aren't always securing against lateral movement and how Illumio Endpoint can help fill the gap.

Why Are We Accepting Blind Spots in Endpoint Traffic Visibility?
Learn how to achieve centralized, end-to-end endpoint visibility with Illumio Endpoint.

When EDR Fails: The Importance of Containment in Endpoint Security
EDR vendors need to adopt Zero Trust Segmentation in order to reduce cybersecurity dwell time and bridge the trust gap definition.

Assume Breach with Zero Trust Endpoint Security
Learn why traditional approaches to endpoint security aren't enough and how Illumio Endpoint can complement your existing detection tools.

3 Best Practices for Implementing Illumio Endpoint
Get three simple but effective steps required to secure your endpoints with Illumio.

Illumio Endpoint Demo: Getting Quick Endpoint Segmentation ROI
Watch this Illumio Endpoint demo to learn how endpoint segmentation with Illumio offers quick ROI.

From Servers to Endpoints: The Benefits of Extending ZTS to Your Most Vulnerable Devices
From Servers to Endpoints: The Benefits of Extending ZTS to Your Most Vulnerable Devices

How to Increase Cybersecurity ROI: Combine ZTS and EDR
Learn how combining ZTS and EDR helps you better protect against advanced threats and mitigate the risk of delayed detection.

Why ZTNA Leaves Security Gaps — And How ZTS Fills Them
Although ZTNA has proven to have many advantages, it's not a bulletproof solution for your network. Combining ZTNA and micro segmentation is more effective.

Why Hackers Love Endpoints — and How to Stop Their Spread with Illumio Endpoint
Traditional security leaves endpoints wide open to hackers. Learn how to proactively prepare for breaches with Illumio Endpoint.

Better Endpoint Protection with CrowdStrike and Illumio Edge
Illumio Edge, our Zero Trust endpoint solution, is now available via Illumio, as well as in the CrowdStrike Store, activated via the CrowdStrike Falcon agent.
Related resources








Illumio Endpoint Explainer Video
Watch the video to learn how Illumio Endpoint delivers unparalleled visibility and proactive breach containment for your endpoints.








Benefits of Combining ZTS and EDR
Stop ransomware attacks nearly 4 times faster than detection and response capabilities alone.








Illumio Endpoint: Best Practices Demo
Dive into the most common use cases that can be rolled out in minutes with Illumio Endpoint, delivering Zero Trust Segmentation for end-user devices.








Better Together: Illumio Endpoint and EDR
Combine Illumio Endpoint breach containment and your endpoint detection and response (EDR) solution for full endpoint security.







Illumio Endpoint Overview
Illumio Endpoint brings Zero Trust Segmentation to your endpoint devices to stop the spread of inevitable cyberattacks.








Illumio Endpoint Demo
See how Illumio Endpoint stops lateral movement and eliminates the risk that your end-user devices pose to your network.
Assume Breach.
Minimize Impact.
Increase Resilience.
Ready to learn more about Zero Trust Segmentation?
