A Hacker Shares 3 Reasons Why Zero Trust Segmentation is His Worst Nightmare
With the number of breaches and ransomware attacks growing exponentially, it seems like threat actors are fearless in their aim to steal data, halt operations, and cause chaos.
Many security teams are asking: What can we do to thwart ever-evolving attacks?
To answer that question, Christer Swartz, Solutions Marketing Director at Illumio, sat down with Paul Dant, Senior Systems Engineer at Illumio and former hacker, to learn what tactics threat actors like Dant keep in their hacking toolkit and the three ways Zero Trust Segmentation (ZTS) quickly makes those tactics ineffective.
Get a quick intro to Paul's start as a hacker in this clip:
Watch the full webinar here.
1. Zero Trust Segmentation stops lateral movement
As a hacker, Dant carried out countless different attacks. While each new hack was distinct from the last — from thwarting a space shuttle launch to pirating unreleased Hollywood blockbuster IPs — they all shared some key traits in the way Paul was able to gain access and wreak havoc. Critical among these was how he moved laterally without restriction through his targets’ networks.
“The basic idea behind lateral movement is that the adversary is trying to move through your environment,” he said. “That's a pretty scary thing when all of this activity is happening under our noses, undetected.”
Dant explained that threat actors use the time they can move through the network undetected to their advantage. They identify target assets and then plan, coordinate, and stage the impact phase. This is why malware can be in your system for days, months, and even years before the attack happens.
ZTS stops attackers from moving laterally once they breach the network perimeter. The breach is contained at its source and is locked out from the rest of the network.
As Swartz explained, “Once a breach happens, you want to be able to not trust anything once a single workload is infected. All the surrounding workloads do not trust that workload, and that one breach is not able to spread laterally.”
2. Zero Trust Segmentation reduces vulnerabilities
Dant’s attack tactic of choice (and of many other hackers) was the Living Off the Land method using legitimate system tools to hide their activities inside a network.
“When we think about the native capabilities of our operating systems, underlying technology, virtual machines, orchestration of containers like Kubernetes — all of these capabilities empower us as users, but they also empower the attackers. Attackers can use those things against us,” he explained.
These native systems and tools can include:
- PowerShell for downloading malicious payloads
- Crypto APIs for encrypting data
- Scheduled tasks for automated actions
- Misuse of high-privilege service accounts
- Manipulating the registry and file system
The best way to reduce the risk of attackers using these tactics? Zero Trust Segmentation.
“There's very little reason for workloads to be talking to each other,” Swartz said. “Laptops shouldn't be talking to each other. Virtual machines shouldn't be talking to all other virtual machines. Cloud resources shouldn't be talking to other cloud resources.”
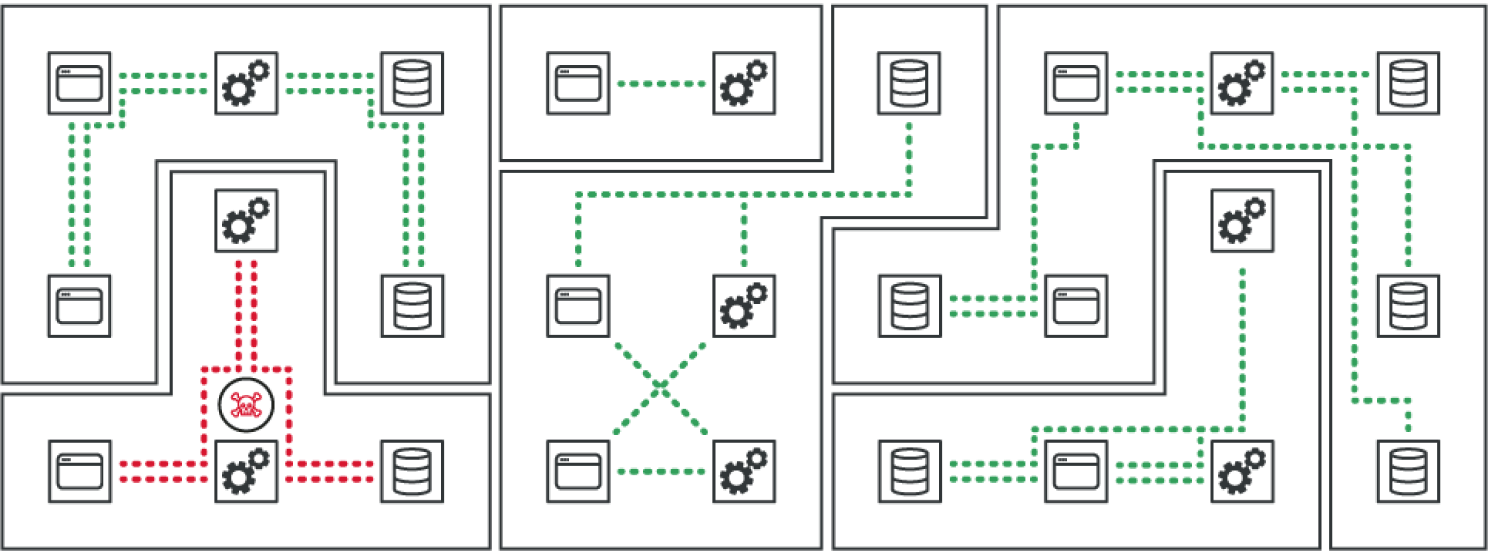
ZTS helps you see the entire attack surface and pinpoint unnecessary connectivity between resources. Then, security teams can quickly prioritize and close these open connections. This stops attackers from taking advantage of often-unlimited access to resources once they’re inside the network.
According to Swartz, “We can block all of that without understanding what that workload is being affected by. We want to be able to assume that something has hit it. We're going to let it die, but we're going to stop the spread.”
3. Zero Trust Segmentation ensures cyber resilience
In today’s threat landscape, breaches are inevitable — and Dant confirmed that threat actors are always planning the next attack. Organizations will never be able to predict the next attack they might face because they’re always changing and evolving.
“It's very difficult to determine if something is legitimate or malicious. There’s not always enough context to know,” Dant noted.
Instead of relying solely on security tools that prevent and detect breaches, he recommends organizations focus on breach containment. This strategy doesn’t require tools to know, understand, or recognize a threat in order to stop it from accessing critical resources and data.
“Nobody can claim to understand 100 percent of what hackers are trying to do,” Swartz pointed out. “But we do know that they all want to move. They're only going to move by a certain limited number of ways through open ports, and that's what we can control.”
ZTS stops all malware from spreading without having to understand the malware’s intent. This removes the issue of ever-evolving attack tactics from the cybersecurity equation, allowing security teams to focus on the solution rather than the problem.
Most importantly, ZTS ensures organizations suffer the least possible impact from inevitable breaches by building cyber resilience.
“Zero Trust Segmentation keeps you safe and gives you a high level of confidence that even if one workload is breached, production is not impacted, and that one workload won’t bring down the entire environment,” Swartz said.
Ready to get started with Zero Trust Segmentation at your organization? Contact us today for a free demo and consultation.
.png)




.webp)
