3 Steps to Start Your Healthcare Organization’s Zero Trust Journey
Every year I attend the HIMSS conference, the busiest cybersecurity sessions are always anything to do with Zero Trust for healthcare professionals — and I expect HIMSS 2024 to be no different. The healthcare industry has embraced the concept of Zero Trust faster and deeper than almost any other sector. While Executive Order 14028 has driven government agencies in the direction of Zero Trust, it’s Zero Trust for healthcare that has led the charge.
In this blog post, I’ll detail how healthcare providers can implement a Zero Trust strategy aligned with CISA’s Zero Trust Maturity Model (ZTMM) and the foundational role Illumio Zero Trust Segmentation plays in any Zero Trust architecture.
What is Zero Trust for healthcare?
Zero Trust provides a simple framework to improve cyber resilience. In fact, ESG research has shown that it also reduces security spending and the overall cost of a breach.
The problem is that the definition of Zero Trust has changed over time, making it difficult to know exactly what it is. Zero Trust was originally introduced in 2010 by John Kindervag in his Forrester Research report No More Chewy Centers: The Zero Trust Model of Information Security. However, for many years, the meaning of Zero Trust has been hijacked by security vendors’ marketing departments. This made it difficult for people to work out what they should be doing as they were bombarded by too many contradictory messages. The good news is that most of those marketing departments are now obsessed by AI and things are much simpler.
In support of Executive Order 14028, the National Institute for Science and Technology (NIST) released a Zero Trust Architecture (NIST SP 800-207) that defined aspects of Zero Trust and what it is as “an evolving set of cybersecurity paradigms that move defences from static, network-based perimeters to focus on users, assets, and resources.”
How to start your healthcare organization’s Zero Trust journey
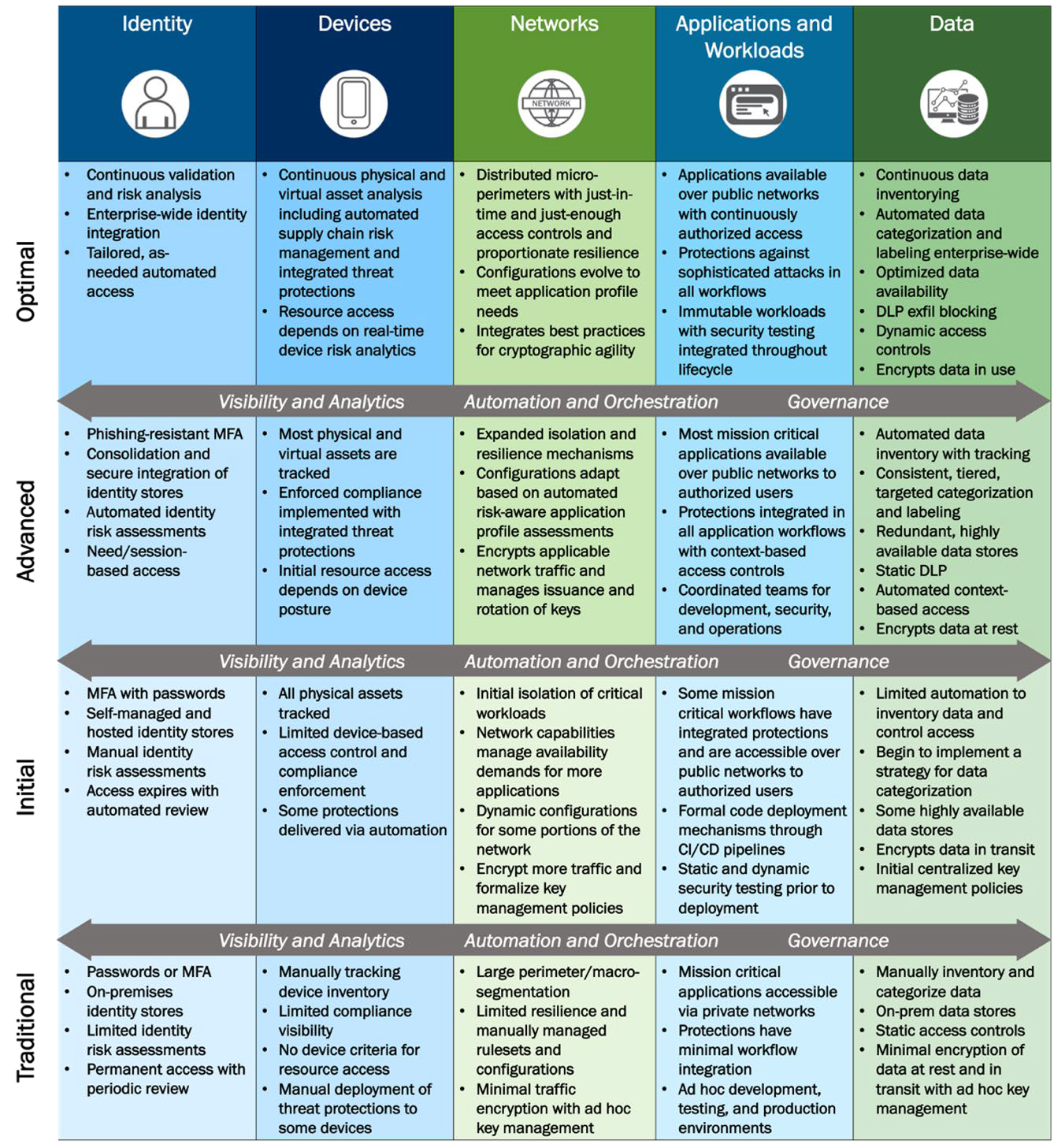
With a clearer picture of what Zero Trust is, the next step is to understand how to achieve it. The good news is that the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has created a Zero Trust Maturity Model (ZTMM) that provides:
- A guide to map your organization’s current status against the five Zero Trust pillar
- A roadmap on how to increasingly optimize your Zero Trust architecture
Too many organizations deploy Zero Trust Network Access (ZTNA) tools as a VPN replacement and then declare Zero Trust complete. The reality is that achieving the Optimal level in all five pillars of CISA’s ZTMM can be a long journey — and extends far beyond ZTNA.
By using the ZTMM, you can plot your organization’s course on its Zero Trust for healthcare journey and ensure it’s protected along the way.
1. Identify what you need to protect
CISA advises to make decisions about Zero Trust implementations based on factors like risk, mission, federal and regulatory requirements, and operating constraints. Identifying risk will guide whether your organization must go broad and step up each level across all 5 pillars together or go deep on one or more pillars.
For instance, if you have an EHR system like Epic, you may decide that ringfencing that environment is the highest priority.
2. Understand your organization’s status on each ZTMM pillar
The maturity model takes the five pillars of Zero Trust and defines four levels of maturity, from Traditional which is the current status quo to Optimal which is the highest level of achievement. After understanding what you want to secure, the next step is to understand the current status for each pillar of the ZTMM.
3. Begin working on priority pillars
Every provider will have different priorities for working toward each pillar’s Optimal level. This will depend on security gaps, budget, staffing availability, or compliance requirements. It’s also important to consider that some pillars are more difficult and expensive to achieve while others are simpler.
Despite differing priorities, Networks is a key pillar into which every organization should be taking a deeper look. This pillar is not about switches and routers but the overall concept of the network and the traffic that flows across it. Applying network segmentation would traditionally involve static VLANs or complex firewall rules, but the CISA ZTMM encourage a more dynamic and flexible approach that provides finer granularity.
CISA has provided further details on each implementation level of the Network pillar, including segmentation, traffic management, and resilience:

More Zero Trust resources for healthcare providers
The UK National Health Service (NHS) has issued guidance on network segmentation where they advise on how to segment five key diagnostic pillars:
_logo.svg.webp)
- Genomics
- Imaging
- Pathology
- Endoscopy
- Physiological measurement
Though much of the NHS’s recommendations for segmentation fall into the lowest Traditional level of CISA’s ZTMM, the NHS does highlight network segmentation as a foundational part of Zero Trust strategy. Their guide states that Zero Trust security “abolishes the concept of a trusted network within an organisation's corporate perimeter and advocates creating micro perimeters of control around critical assets and enforcing strict access controls, network segmentation and identity management.” This definition of segmentation maps neatly to the Optimal level of CISA’s ZTMM.
Build attack tolerance with Illumio Zero Trust Segmentation
Healthcare organizations are turning to Illumio Zero Trust Segmentation (ZTS) for a simple, cost-effective approach to achieving the Optimal level of network segmentation without complex network engineering or static firewall rules.
With Illumio ZTS, your organization can:
- Become attack-tolerant: Gain end-to-end visibility of all communication between workloads and devices across the entire hybrid attack surface. See where security gaps lie and close unnecessary connections.
- Plan for an attack: Automatically set granular yet flexible policy controls that stop the spread of cyberthreats, enhance cyber resilience for critical systems, and proactively prepare your organization for the next inevitable attack.
- Adapt in real time: Reactively isolate compromised systems during an active attack to stop lateral movement and maintain operations. As your IT environment evolves, scale visibility and security policy dynamically to ensure business agility and resilience.
- Meet compliance requirements: Leverage visibility and microsegmentation to assess risk, prove compliance, and secure sensitive data and critical resources.
Read our guide on Illumio ZTS for healthcare providers, and learn more about the 3 ways ZTS solves healthcare security challenges:
Contact us today to learn how Illumio can help your organization stop the spread of breaches and ransomware attacks.
.png)
.webp)




