Little-Known Features of Illumio Core: SOAR Platforms Integrations
In this series, Illumio security experts highlight the lesser known (but no less powerful) features of Illumio Core.
Breaches and ransomware attacks are evolving quickly — faster than many traditional prevention and detection technologies can react.
Malware can spread in seconds, far quicker than any human can respond. It's a truism of the cybersecurity industry that the weakest link in any security architecture is between the keyboard and the chair. The solution to automated malware propagation needs to be an equally automated security response.
Through Illumio Core’s integration with third-party SOAR platforms, you can be confident that new and unknown malware will be automatically isolated and contained.
Why breach containment matters now
All malware shares one thing in common: they like to move.
The first breached workload is rarely the intended target. It’s used as a “foot in the door” of your network to gather information. With this insight, the malware and its control system exchange command-and-control traffic. Ultimately, the control system instructs the malware on how to propagate through the network.
The bad news? All of this happens in a matter of seconds.
Breaches and ransomware attacks are unavoidable, and your traditional prevention and detection tools aren’t enough to stop today’s attacks. Organizations of every size, geography, and industry must prioritize breach containment strategies in addition to their prevention and detection tools. This ensures the next breach doesn’t become a catastrophic event that halts operations, exposes sensitive data, and diminishes the trust of your customers, stakeholders, and employees.
Modern cybersecurity is defined by moving from breach prevention to breach survival. Stopping breach propagation must be as strong of a priority as preventing a breach from happening.
Proactively prepare for breaches with Illumio
Unfortunately, no breach prevention solution will ever be 100 percent effective; a breach will happen. Once that inevitable breach occurs, Illumio stops it from spreading to neighboring hosts by proactively disabling open ports on all hosts.
Most hosts and their workloads don’t need to establish connections between each other. Rather, they usually only need to connect to a small set of common resources or make outbound connections. For example, it’s rare that all workloads deployed in a data center or cloud environment need to connect directly to each other.
To mitigate the risk unnecessarily open ports can cause, Illumio can enforce workloads in one of two ways:
- Selective enforcement: Specific ports are blocked, and all other traffic is allowed.
- Full enforcement: Specific ports are blocked, and all other traffic is denied.
Selective enforcement can be used when you know what traffic you don’t want to allow between workloads, such as RDP and SSH. However, malware is constantly evolving and finding new ports to use. Because of this, it’s best to use full enforcement as it’s much more effective at blocking the spread of malware. In full enforcement, Illumio will disable all ports on all workloads at any scale, and then allow open ports by exception as required.
The result will look like the example of full enforcement below. In the left-side image, workloads are prevented from communicating (red arrows) because default-open ports have been disabled by Illumio. On the right-side image, Illumio has enabled exceptions (green arrows) to only allow traffic between specific application groups over specific ports:
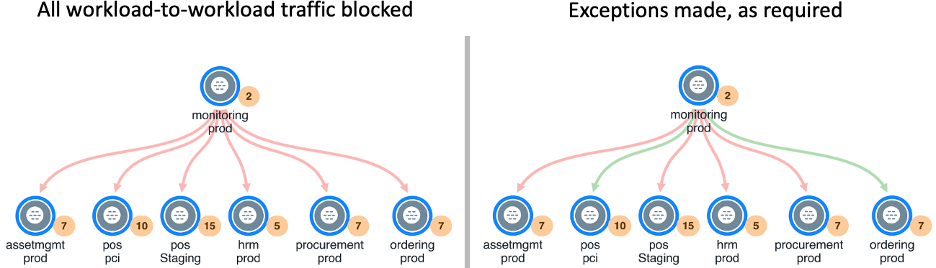
In full enforcement with Illumio, infected hosts won’t allow malware to travel very far because only a handful of ports are open — something that’s true regardless of how new or complex the malware is. This causes the blast radius of an attack to shrink significantly, turning what could've been a catastrophic breach into a small security incident that doesn’t impact operations or require outsized remediation costs.
Automate policy changes with Illumio’s SOAR integrations
If one thing is true in cybersecurity, it’s that things change — constantly. Today’s threat landscape and the complexity of today’s networks means security measures can’t stay static. Organizations must have a way to update enforcement policies in real time.
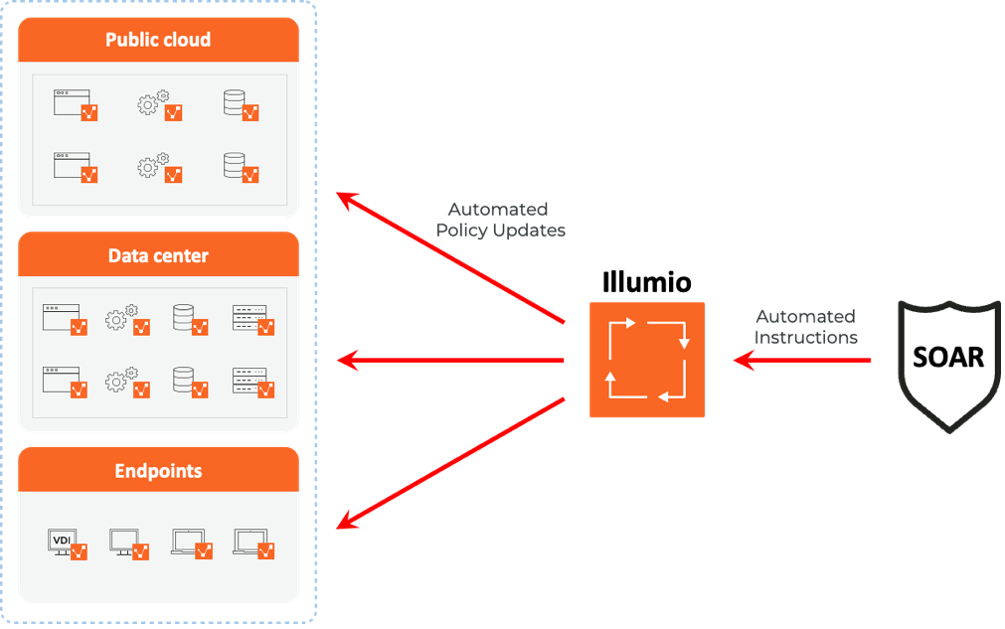
Illumio enables fully automated, real-time changes to its security policies via integrations with SOAR (Security Orchestration, Automation, and Response) platforms.
It’s important to note that SOAR platforms are different from SIEM (Security Information and Event Management) platforms. Illumio can forward logs to a SIEM platform such as Splunk to analyze logged events on workloads managed by Illumio, looking for red flags. But if it finds any, the SIEM has no way of sending commands back to Illumio to close at-risk ports. This capability is enabled via a SOAR platform.
Illumio integrates with three third-party SOAR systems: Splunk SOAR, IBM QRadar SOAR, and Palo Alto Networks Cortex XSOAR. Illumio + SOAR integrations deliver fast defense-in-depth through these steps:
- The SOAR platforms monitor the threat landscape, looking for new, previously unknown zero-day malware that is using specific ports to spread.
- If the SOAR platform sees that new malware is using a new port to spread, it will immediately and automatically send API calls to Illumio’s PCE engine via a plugin on each vendor’s Marketplace. This tells Illumio to close the ports on all managed workloads.
- Illumio will automatically close the zero-day malware’s targeted ports. This will proactively protect workloads from the malware even if it hasn’t arrived yet. This is enabled immediately, without needing any reliance on human intervention.
Illumio Zero Trust Segmentation: Respond to cyberattacks faster
In addition to complete visibility and granular microsegmentation, the Illumio Zero Trust Segmentation (ZTS) Platform provides reliable, scalable, and fully automated response to ever-evolving cybersecurity threats.
Malware wants to spread — and Illumio, in conjunction with SOAR platforms, can automatically close ports, stopping malware from spreading through a fully automated workflow. With the next breach or ransomware attack always right around the corner, Illumio helps your organization ensure that breaches can’t spread through the rest of the network or escalate into a business-impacting crisis.
To learn more about Illumio ZTS, contact us today for a free consultation and demo.
.png)





