NAME:WRECK Takeaways — How Micro-Segmentation Can Help with Visibility and Containment
The NAME:WRECK collection of vulnerabilities enable attackers to remotely compromise critical servers and IoT devices, even those behind perimeter firewalls, by exploiting flaws in their handling Domain Name System (DNS) responses. Hundreds of millions of devices globally – including healthcare technology, smart devices and industrial equipment – could potentially be compromised using NAME:WRECK.
Recently published research by Forescout and JSOF details this collection of vulnerabilities that leverage DNS response parsing. These defects are found in the TCP/IP stacks in a number of operating systems and could lead to remote code execution or denial of service on the target system. In order to exploit these vulnerabilities, an attacker needs to be able to reply to a valid DNS query – by inserting themselves as a man in the middle between the vulnerable client and the DNS server – with a response whose payload is formatted to trigger the weakness. Platforms shown to be vulnerable include FreeBSD, which is prevalent across data centres, and Nucleus and NetX, which are both extensively used as operating systems in IoT and OT devices. The full write-up on NAME:WRECK can be found here.
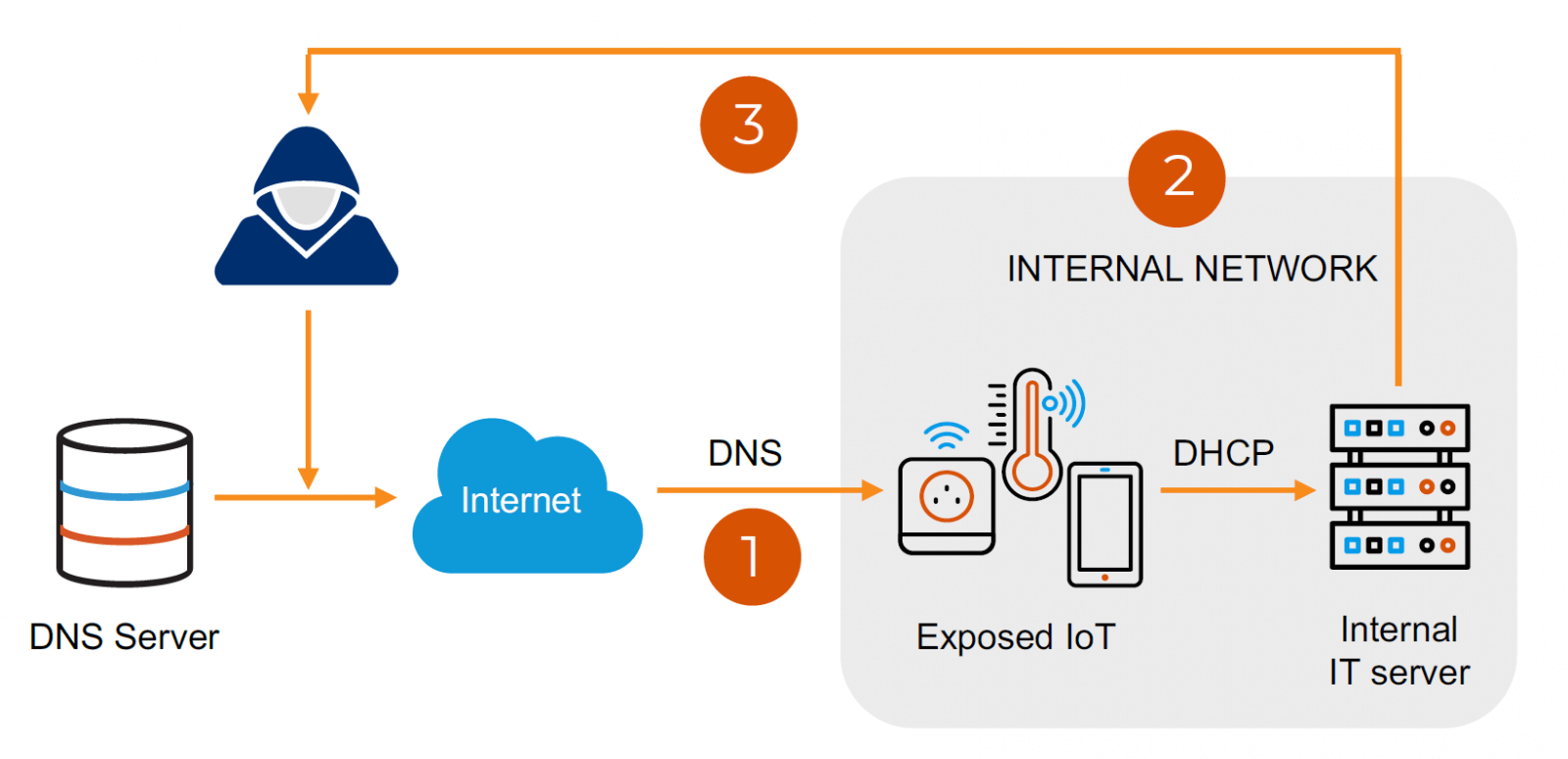
Given that initial compromise depends on the attacker having network access to the target device and post-compromise lateral movement necessitates onward pervasive network access being present, visibility and micro-segmentation provide capabilities that could support both detection and mitigation of a possible attack.
The starting point for both is an accurate asset inventory of devices in the environment that is running the impacted platforms. This may be straightforward for servers in a data centre but more challenging for IoT or OT devices that are dotted across campuses: if this information is less than perfect, knowing where in the network they are deployed (even at the subnet level, if not specific IP) is a good starting place.
Visibility
Because an attacker would need to perform a MITM (man in the middle) in order to inject the malicious DNS response, identifying the rogue connection may be challenging. However, the following could provide some insight:
- Attempted DNS connections to unrecognised or unexpected DNS servers.
- Unusually high volumes of activity to a specific DNS server.
- DNS responses with large payloads.
Potential post-compromise lateral movement could be detected via the following:
- Target estate (FreeBSD, NetX, Nucleus) connectivity to internal devices they do not normally connect to.
- New internet connection attempts from the target estate.
- New large data transfers from/to the target estate.
Containment
Organisations can leverage micro-segmentation to reduce the potential attack surface and inhibit lateral movement:
- Limit devices to only be able to access authorised DNS servers (both internal and external).
- Restrict access to/from devices so that rules only permit flows necessary for business operations, thereby preventing unrestricted access to the network.
- Prevent device access to the internet or restrict access to specific domains only.
Illumio customers can leverage Illumio Core’s unparalleled visibility to enable this monitoring and build appropriate segmentation policies. Reach out to your Illumio account team to learn how.
.png)


