How to Prepare for NIS2: What You Need to Know

Much has been written about NIS2 recently as we head towards a key milestone in its implementation. By the 18th of October 2024, member states must adopt and publish the measures necessary to comply with the NIS2 directive.
While that date may instill panic among many, it’s just the date when the individual countries need to adopt NIS2 into law and repeal NIS1 (EU 2016/1148). The timeline for compliance of individual organizations will be defined in the laws enacted by individual states. For some, this could be up to four years beyond this date.
No matter when NIS2 will enter into force, it’s time for organizations to begin preparing to comply with NIS2’s mandates for cyber resilience.
What is the difference between NIS1 and NIS2?
Many have asked why there’s a need for a version two or even a future version three of the NIS directive.
The simple answer is that things change.
The new NIS2 directive better reflects the current cybersecurity landscape. It also makes updates based on learnings from NIS1.
Since NIS1 entered into force in 2016:
- The types of organizations that are viewed as critical have changed.
- Technology has changed with an increase in automation and smart devices.
- Cybersecurity has changed where the old focus on protecting static networks has been replaced by a more agile approach.
- The adoption of Zero Trust has simplified how cybersecurity is deployed, resulting in a more secure approach at lower cost.
- The types of cyberattacks have changed with an increase in disruptive attacks and the appearance of AI-generated attacks.
The other main reason for an update to NIS1 is to improve governance. The idea in 2016 was that each state would develop its own set of regulations and the national regulator would enforce them. Unfortunately, there has been a wide disparity in how each country has implemented NIS1, and so NIS2 sets out some minimum standards for certain focus areas and provided the European Commission with greater oversight.
The final change is a reclassification of organizations and an expansion in the number and size of organizations included in the directive:
- The distinction between essential services and digital service providers is replaced by classifying organizations on their importance to the country and dividing into essential and important categories.
- Organizations with more than 50 employees and an annual turnover of more than €50m are now categorized as important.

How will NIS2 affect my organization?
NIS2 seeks to harmonize requirements across member states by setting specific rules for the frameworks members put in place. This focuses on certain cybersecurity measures, including:
- Risk analysis and information system security policies
- Incident handling
- Business continuity and crisis management
- Supply chain security
- Secure network and systems acquisition, development and maintenance, including vulnerability handling and disclosure
- Policies and procedures to assess effectiveness of measures
- Basic computer hygiene practices and cybersecurity training
- Policies and procedures regarding use of cryptography / encryption
- The use of MFA, secured comms and secured emergency comms
Member states where these measures aren’t already incorporated in national regulations will need to add these features. And organizations in these countries that don’t already implement these controls will need to adopt them.
Likely the biggest impact of NIS2 is on organizations that haven’t been previously covered by NIS1. While this sounds concerning, research by ENISA shows that the average budget for NIS implementations is for projects that last 14 to 18 months.
What can my organization do now to prepare for NIS2?
In 2016, organizations were limited in the security tools and approaches available, trapped by static technologies like traditional AV, NAC and firewalls, and limited visibility.
Even though Zero Trust was being discussed at that time, the focus was still on trying to prevent every attack by trying to detect all malware. Today, the combined threat of ransomware and AI poses new problems which the NIS2 directive will try to address.
While specific NIS2 technical requirements aren’t yet available for each member state, organizations can get started on their journey toward compliance by adopting a breach containment approach using technologies like Zero Trust Segmentation, also called microsegmentation. This modern approach assumes breaches are inevitable and, in response, ensures proactive security measures are in place.
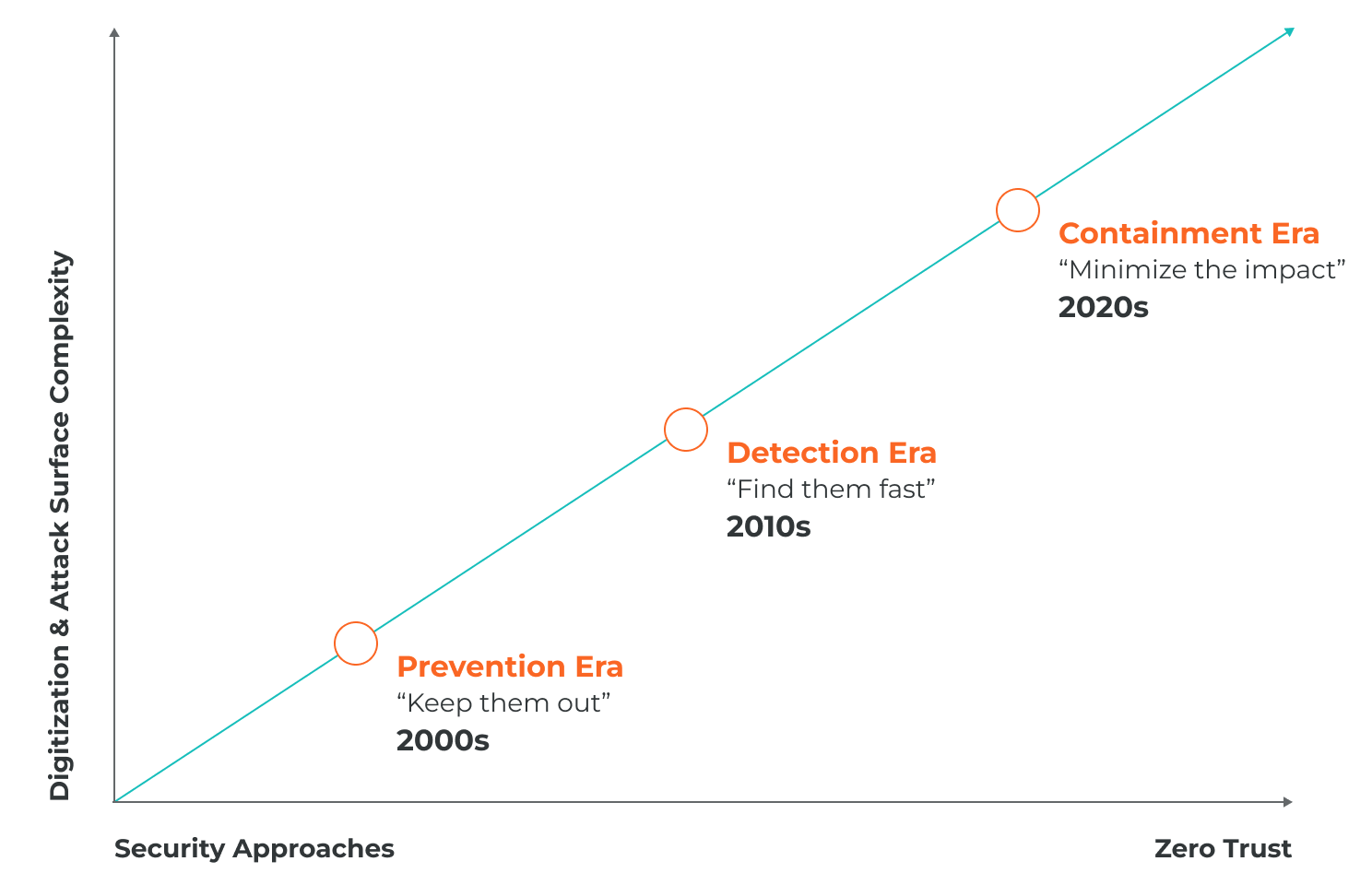
A Zero Trust breach containment strategy includes these key pillars:
- Assume breach and plan for it
- Identify all assets and resources and map interdependencies
- Protect against all vulnerabilities and exposed ports
- Respond quickly and with agility
- Restore safely without reinfection
The purpose of the NIS directive is to improve the resilience of critical infrastructure across the European Union. This means making sure that services can be maintained while under attack.
To achieve this, the focus must shift from trying to stop an attack to making sure that an attack is contained and cannot reach an organization’s business-critical resources.
How does Illumio align with NIS2 requirements?
NIS2 focuses on standardizing key cybersecurity measures, and Illumio Zero Trust Segmentation (ZTS) helps you meet the following.
1. Policies on risk analysis and information security
Application dependency mapping provides complete visibility into traffic across all workloads, including containers, IoT, and virtual machines, in a single console. This allows security teams to pinpoint network risks and create security policies that block unnecessary connections between ports.
2. Incident handling
During an active breach, Illumio can respond quickly to restrict access to critical resources, stopping the spread of an attack and fully isolating compromised systems. Post-breach, ZTS intelligently separates the infected system in real-time to allow safe restoration of data.
3. Business continuity and crisis management
Security and IT teams can use Illumio to set up protection around individual departments and systems so they can resume operations while shielded from the attack. Any attempts to reinfect can be prevented by only allowing connection with an immutable data source during breach recovery.
4. Supply chain security
Illumio allows only known and verified communication between environments. This ensures that when there's a breach in the supply chain, ZTS will stop the breach from entering and spreading into the organization's systems.
5. Security in network and information systems
Illumio extends consistent microsegmentation across all environments, from on-premises data centers to hybrid and multi-cloud environments. This ensures a breach gets stopped and contained immediately so attackers cannot move to other parts of the network.
6. Policies and procedures to assess effectiveness of measures
The Illumio Ransomware Protection Dashboard helps better prepare and protect against the threat of attack by providing insights into workload risk exposure, visibility of protected versus unprotected workloads, and a protection coverage score.
7. Basic computer hygiene practices and cybersecurity training
Illumio's end-to-end visibility of the entire attack surface provides insight into security gaps that help inform cyber hygiene and training needs. ZTS also ensures that inevitable human errors don't leave vulnerabilities for attackers to exploit.
8. Human resources security, access controls, and asset management measures
With Illumio, security teams can implement granular segmentation policies to limit access to systems, including HR resources. This means that if one part of the network gets breached, attackers can't spread to critical resources.
Get more details in Achieve NIS2 Compliance With Illumio.
NIS2: A simpler framework for securing essential services
Compared to traditional prevention and detection strategies, a breach containment approach is much simpler because organizations only need to define the few things that are allowed in the network as opposed to the thousands of things that need to be stopped. The ability of AI to find vulnerabilities and open connections makes us more susceptible to a breach but a shift in approach can help.
By focusing on protecting the resource regardless of whether it is on a server, in the cloud or an OT device saves the complexity of trying to design policy for static network-based security technologies.
Get more information about how Illumio protects essential services organizations.
Contact us today for a free demo and consultation.
.png)





.webp)