How to Secure Against the New TCP Port 135 Security Vulnerability
As a security expert, do you ever feel like you're in a lifelong, never-ending string of popping quarters into a Whac-a-Mole carnival game? (You know the one, it's usually alongside the other annoyingly loud game called Skeeball.)
Each time a mole pops its head out, you only have a split second to take out all of your aggressions from life on it before it sulks back into its hole, only to pop up again 3 seconds later.
Dealing with every new security vulnerability oftentimes feels the same way.
I vividly remember from my youth the unique strategy my buddy Chuck would take with whac-a-mole. He would simply sit on the game, never letting any of the moles escape their hole. As a result, Chuck would beat my score every time!
Hmmm‚ as a security person, that analogy seems rather pertinent, doesn't it?
New TCP port 135 vulnerability allows remote commands
This came to mind as I was reading about a new security exploit featured by Bleeping Computer involving one of our favorite suspects: PsExec, the Windows program that allows for remote execution and file sharing.
Some folks over at the security validation firm, Pentera, published an article showing how they were able to develop a novel way to exploit TCP port 135 to execute remote commands.
TCP 135 historically acts as a "sidecar" to SMB on port 445 used by file-sharing systems on Windows. What makes Pentera's findings unique is that they were able to just utilize TCP 135 on its own to perform remote execution.
And so while many companies already have policies in place against 445, now TCP 135 should be considered equally important to isolate.
How to stop playing hackers' games by deploying Zero Trust strategies
A lifelong game of whac-a-mole against breaches and ransomware is tedious, ultimately ineffective, and will eventually cost you way more money than necessary. (And it isn't worth that giant stuffed panda at the carnival in the first place!)
Stop reacting to whatever new exploit gets built next week. Get on board with Chuck's strategy of sitting on the whac-a-mole game: Block every port everywhere that doesn't need to be open!
Breaches will occur, no matter how fast you swing that hammer. Deploy a Zero Trust strategy by only permitting ports and protocols as needed, between all systems.
Close security vulnerabilities with Illumio Zero Trust Segmentation
Breaches and ransomware use lateral movement to spread through a network.
The Illumio Zero Trust Segmentation Platform offers a few ways for your organization to stop this from happening.
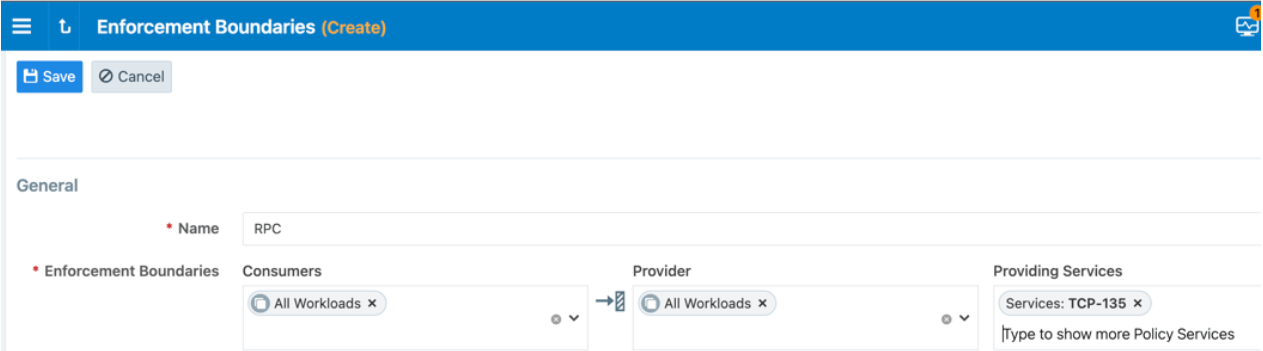
Enforcement Boundaries
With Illumio Enforcement Boundaries, you can stop lateral movement by deploying a network-wide policy that can limit communication on ports like TCP 135 by denying it between user's machines.
You can literally have this policy written with five clicks, and then push this out to your Illumio-managed systems network-wide. (Or, for the folks here who are more of auditory learners, that's Click, Click, Click, Click, Click to you).
Granular security policies
You could also be a bit more granular by writing policy to limit these ports to a select few administrator systems.
That's one of the advantages of a solution like Illumio - we make it easy to narrowly define exactly who should talk to who and select the exact ports and protocols needed.
And Illumio can achieve this across your organization with Zero Trust Segmentation solutions for your data center, your end users, and even your cloud-native assets.
No deep packet inspection needed
If you want to win at whac-a-mole, do you really need to take courses on arcade game electronics or learn a programming language? Of course not - you just need to have the right strategy.
This is another benefit of Zero Trust Segmentation: You don't have to understand the mind of the cybercriminal or take the time for Layer 7 DPI to secure against the spread of breaches.
Zero Trust Segmentation allows you to quickly put Zero Trust security best practices in place and prevent breaches from spreading throughout your infrastructure.
Use Zero Trust Segmentation to be ready for what comes next
It seems like my friend Chuck had a more effective solution: Use a proactive strategy that prepares you for whatever comes up next. (It helped him walk away with hundreds of tickets and then get a sugar high from the Pixy Stix, but that's a story for another day.)
Tomorrow will bring with it a new exploit like this RPC variety. And it will also bring a phone call from your CISO asking you if your network is vulnerable to some new TCP port that you never even knew was running on your servers.
Spend your weekends at the carnival instead. Implement Zero Trust Segmentation.
Want to learn more about how to secure against the new TCP Port 135 vulnerability?
- Learn how Hongkong Electric Company ensures 99.999% reliability with Illumio.
- Read why Gartner recommends Illumio Zero Trust Segmentation for workload and network security.
- Get in-depth guidance on implementing ZTS in our guide, How to Build Your Microsegmentation Strategy in 5 Steps.
.png)
_(2).webp)

