Illumio Recognized in Two Gartner® Hype Cycle™ Reports
Cyber threats are changing quickly – and cybersecurity technologies must keep up. But traditional prevention and detection technologies aren’t enough to stand up against today’s ever-changing threats.
As a result of these challenges, security teams are turning to Zero Trust security strategies.
According to Gartner, “Zero Trust is becoming a requirement in data center design, and microsegmentation is a practical way to accomplish this.”
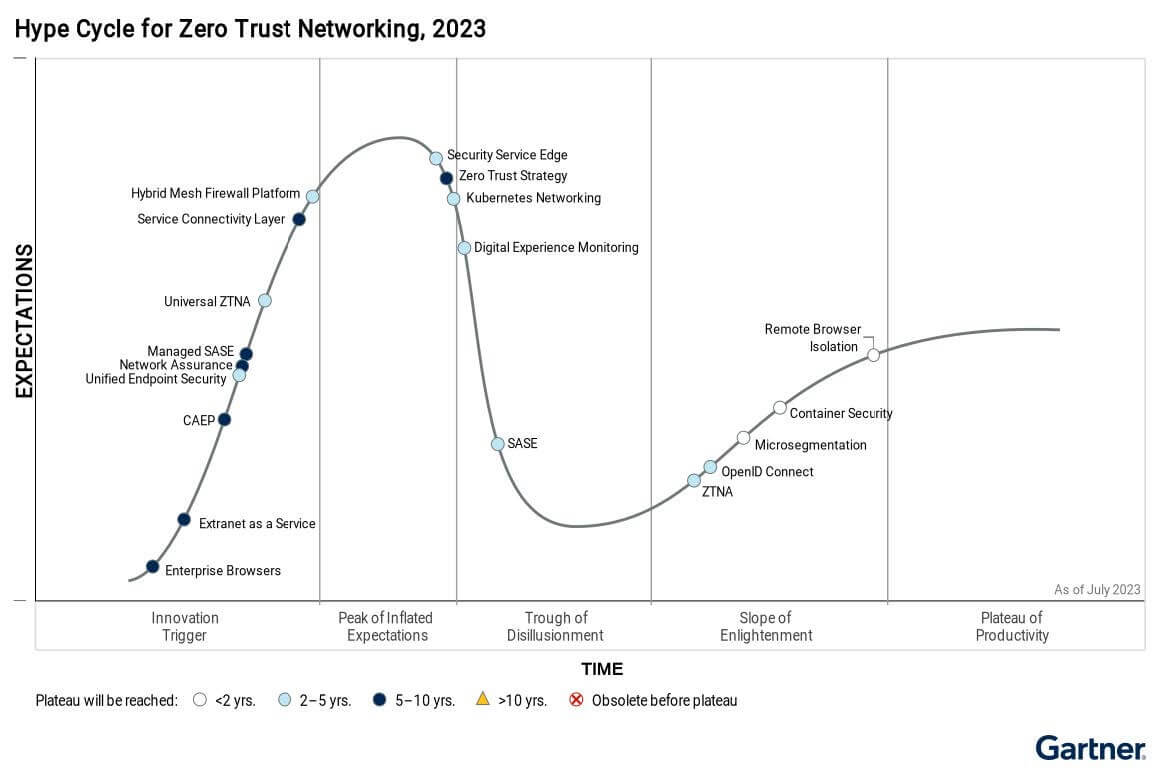
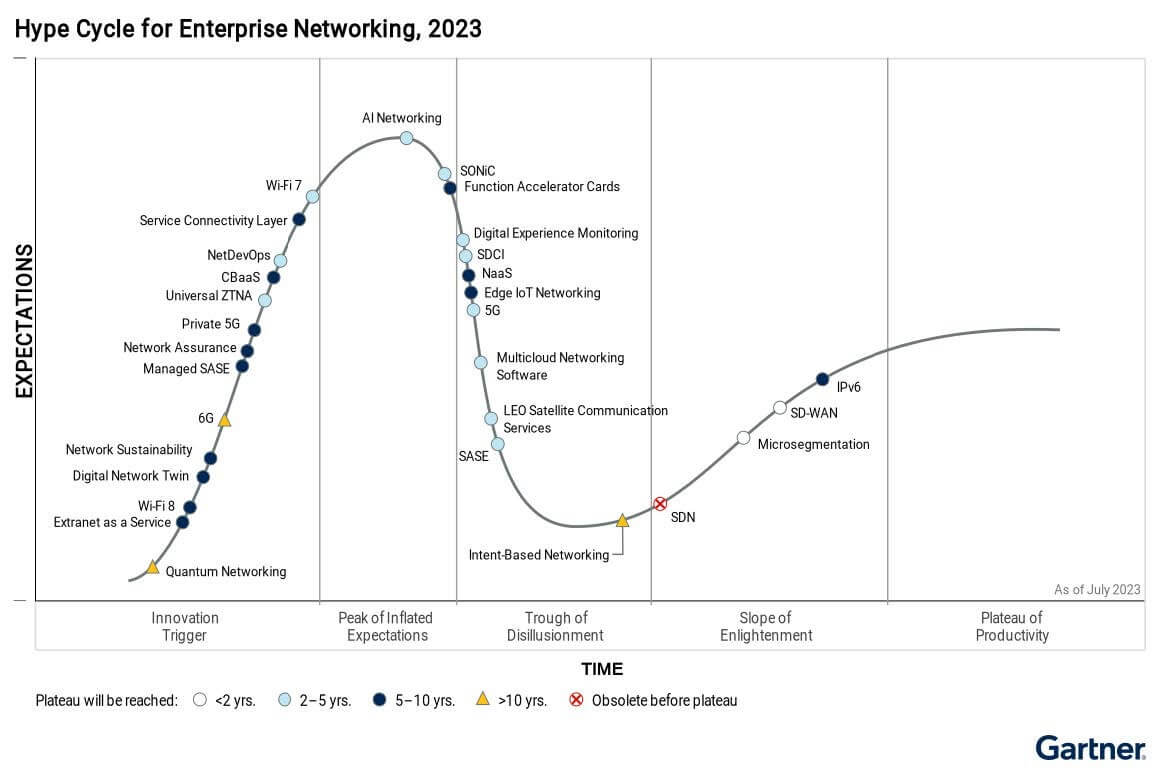
In both the Hype Cycle for Enterprise Networking, 2023 and the Hype Cycle for Zero Trust Networking, 2023 reports, Gartner recognized microsegmentation, also called Zero Trust Segmentation, as a:
- High-benefit technology
- Expected to achieve mainstream adoption within the next two years
- On the Gartner Hype Cycle Slope of Enlightenment to offer real-world adoption and benefits
Read the full Hype Cycle for Zero Trust Networking, 2023 report.
Gartner recognized Illumio as a Sample Vendor for microsegmentation in both reports.
Why we believe Gartner recommends Zero Trust Segmentation to stop the spread of breaches
At its core, Zero Trust Segmentation (ZTS) goes beyond the limitations of traditional network segmentation to stop the spread of ransomware and breaches.
According to Gartner, “As servers are being virtualized, containerized, or moved to infrastructure as a service (IaaS), existing safeguards such as traditional firewalls, intrusion prevention solutions, and antivirus software struggle to follow the fast pace of deployment for new assets.”
The changes brought by rapid digital transformation have left organizations vulnerable to attackers who can easily and quickly get past traditional detection and prevention tools. Without ZTS, breaches can enter the network and then immediately move laterally, causing widespread – and often catastrophic – cyber incidents.
This is especially true as organizations scale their networks. Gartner notes: “The increasingly dynamic nature of data center workloads makes traditional network-centric segmentation strategies difficult to manage at scale, if not impossible to apply.”
With ZTS, organizations can secure large, complex, and growing environments by building granular and adaptable access policies. A key part of this is visibility – Gartner recommends platforms that offer visibility into all communication and traffic between workloads and devices across the entire hybrid attack surface.
“Some microsegmentation products provide rich application communication mapping and visualization, allowing data center teams to identify which communication paths are valid and secure,” Gartner says.
Ultimately, ZTS helps build a security posture that is more responsive to today's dynamic threat environment.
As Gartner explains, “Once a system is breached, attackers move laterally (including in ransomware attacks), which can cause serious damage. Microsegmentation seeks to limit the propagation of such attacks. It can greatly reduce the initial attack surface as well.”
Why choose Illumio for Zero Trust Segmentation
Gartner sees organizations taking an increased interest in visibility and granular segmentation for east-west traffic between applications, servers, and services.
With Illumio ZTS, you can quickly and easily:
- See risk: See risk by visualizing all communication and traffic, both known and unknown, between workflows, devices, and the internet.
- Set policy: With every change, automatically set granular segmentation policies to control unnecessary and unwanted communications.
- Stop the spread: Automatically isolate compromised systems and high-value assets in minutes to proactively stop the spread of a breach or reactively during an active attack.
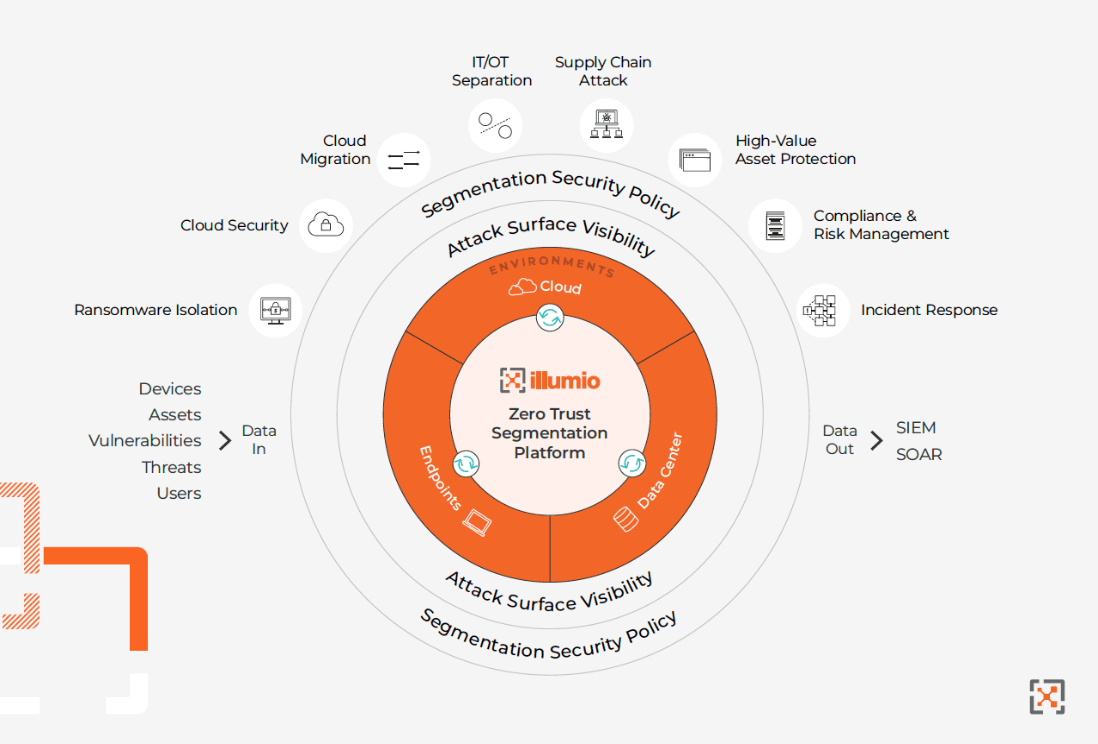
In just a few hours, security teams can use Illumio’s real-time application dependency map to see traffic between workloads and devices across the entire hybrid attack surface. Illumio's agnostic approach to the underlying network infrastructure ensures an elevated level of visibility, a feature that we believe aligns with the “rich application communication mapping” Gartner recommends to pair with ZTS implementations.
Leveraging insight from the application dependency map, organizations can proactively identify and secure potentially hazardous or outdated pathways and ports. This strategic isolation of critical assets forms a robust defense mechanism against the lateral movement intrinsic to breach and ransomware. We feel it also aligns with the Gartner report’s user recommendation to “target the most critical assets and segment them first.” Within this framework, Illumio allows you to set basic security policies that can be progressively scaled to granular levels whenever needed.
Scaling segmentation policies is streamlined by Illumio's Policy Generator which alleviates the complexities often associated with this task. Through automated recommendations of optimized segmentation policies tailored to diverse workload scenarios, including containers, virtual machines, and bare metal systems, the Policy Generator simplifies what was once a resource-intensive process.
Importantly, Illumio ZTS pivots from traditional reliance on IP addresses or network locations to a more intuitive label-based system. This aligns with Gartner's recommendation to “use the identities of applications, workloads, and services – either via logical tags, labels, fingerprints or stronger identity mechanisms.” Illumio’s policies will follow workloads wherever they go across different hybrid and multi-cloud environments.
Read the full Hype Cycle for Zero Trust Networking, 2023 report.
Want to learn more about Illumio ZTS?
- Learn why Gartner named Illumio as a Representative Vendor in its 2023 Market Guide for Microsegmentation.
- Get the key findings from Bishop Fox’s emulated attacks that prove how the Illumio ZTS Platform helps stop cyberattacks 4 times faster than detection and response alone.
- Read the Forrester Total Economic Impact study of Illumio ZTS to see how Illumio customers realize a 111% ROI and $10.2M in total benefits.
Gartner Disclaimer: Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally, and HYPE CYCLE and MAGIC QUADRANT are registered trademarks of Gartner, Inc. and/or its affiliates and are used herein with permission. All rights reserved.
* This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from Illumio.
.png)

.webp)



.webp)