Nano-segmentation℠: What is the fuss all about?
At last week’s RSA conference, Illumio introduced nano-segmentation, our latest innovation in securing multi-tier applications running in data centers and clouds. The Illumio Adaptive Security Platform (ASP)TM now extends application segmentation from the granularity of individual workloads to processes running within the workloads.

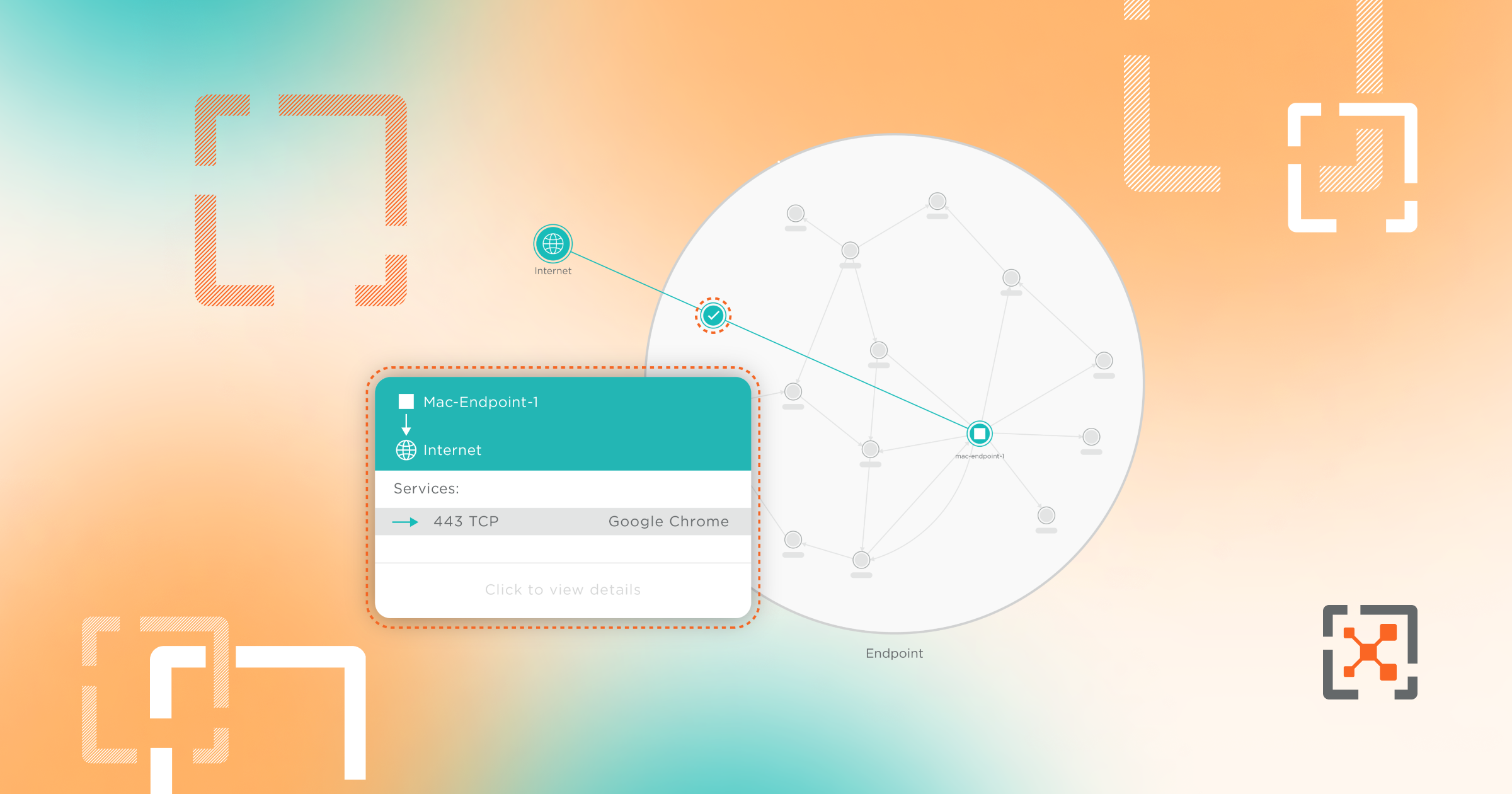
RSA attendees watching the Illumio theater presentations saw the power of nano-segmentation to dramatically reduce the enterprise exposure to threats and constrain the “blast radius” of attacks. We showed how nano-segmentation could quarantine a compromised server using a simple drag-and-drop operation—an industry first. Segmenting the data center to separate applications (dev, test, production, etc.) or to isolate applications (e.g., for PCI compliance) is necessary to handle security for dynamic computing environments distributed across data centers and clouds. But not all segmentation is created equal. Let me explain.
Not all segmentation is created equal.
Most of us are familiar with the term “micro-segmentation,” which was introduced by SDN vendors a few years ago. Micro-segmentation was promoted as a way for enterprises to isolate applications running in virtual environments. However, current solutions for micro-segmentation come with a number of strings attached: They are either tied to the hypervisor, network constructs (VLANs, subnets, security zones etc.), or other hardware (switches, routers etc.). Most solutions do not address the segmentation of applications in the cloud or applications that include bare-metal servers. The goal of security through application segmentation is well intended, but existing solutions fall short.
Enter nano-segmentation
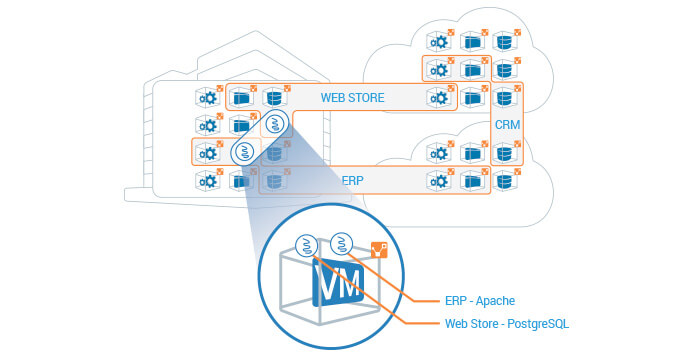
The first step to achieving the most granular segmentation for data center applications is to drive down the attack surface to individual units of computing (any VM or bare metal server) in data centers and clouds. Illumio ASP does this by dynamically programming precise inbound and outbound security rules on every single workload. This enables the platform to create an adaptive perimeter around every computing instance (in any data center or cloud), effectively creating a segment of one. When combined with the Illumio ASP dynamic, whitelisted policy model, it enables administrators to fully specify permitted workload interactions for applications without any dependencies on the network. With the latest product launch, Illumio took this a step further by enabling the segmentation of multiple applications down to processes on a single host. As an example, two instances of the Apache process on a single workload could be segmented across two different applications.
What’s with the name?
Did we indulge in a little marketing one-upmanship with a name like nano-segmentation? Far from that—it is deliberate and supported by proof points. Nano-segmentation, as the name implies, enables enterprises to segment applications to the most granular extent possible. We wanted enterprises to know that there is a way to “have their cake and eat it too”—they can segment applications across data centers and clouds while keeping security intact. More importantly, the feature enables application segmentation to be equally effective in any computing environment.
And one more thing: The term “Nano” lends credence to the Illumio tenet of network independent security. It is an acronym for “Never Again Network-Oriented.”
.png)