What to Expect When Starting Out With Microsegmentation
According to Gartner, “By 2026, 60% of enterprises working toward zero trust architecture will use more than one deployment form of microsegmentation, which is up from less than 5% in 2023.”
Microsegmentation is foundational to zero trust. You can’t achieve zero trust without it.
In fact, John Kindervag, the creator of Zero Trust, addressed the connection between zero trust and segmentation in the second report ever written on the topic, Build Security Into Your Network’s DNA: The Zero Trust Network Architecture. In the report, he said, “New ways of segmenting networks must be created because all future networks need to be segmented by default.”
If you’re building a zero trust architecture, microsegmentation should be a crucial part of your plan. Here are the 10 things you can expect to do when starting out with microsegmentation.
1. Get visibility into all workload traffic across every environment
The first — and one of the most important — steps of building microsegmentation is being able to know what’s going on across all segments in your network. How do you see all traffic between all workloads across your cloud, endpoint, and data center environments? It’s crucial to be able to achieve this level of visibility at any scale without an overly complex workflow.
You can try to use different visibility tools for different segments across your network. But using multiple tools will create a fragmented view. This can make it challenging to understand behavior across all segments everywhere.
Instead, find a solution that can discover traffic across all segments and display it in one view. For example, Illumio can help you see who is talking to who over what ports so that you can discover all dependencies.
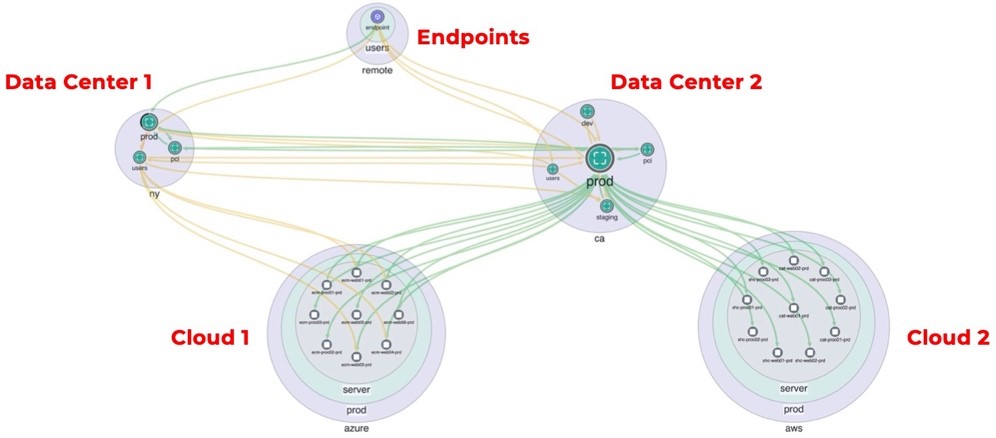
With this information, you can find the “open doors” in your network, decide which traffic is required, and then deny all other traffic by default.
2. Understand how apps are communicating
Most people agree that Zero Trust is a good idea, but how can you understand what traffic is required before deciding what to protect? It’s not always easy to see what apps are running across your network and what ports they need to use.
With a solution like Illumio, you can discover what applications are running on all workloads and what ports they’re using. This provides a comprehensive inventory of all applications and their dependencies in your network so you can decide how to enforce segmentation policy.
3. Lock down your most critical, highest-risk resources
Not all entry points into your network are under your direct control. While a data center for a campus network might have strong controls in place, resources in the cloud or partners’ third-party access are often less secure.
Many threats start from these less-secure environments because they’re often left open due to human error. Any of these access points can be an attacker’s first step in the door, allowing threats to move across your network to your high-value assets.
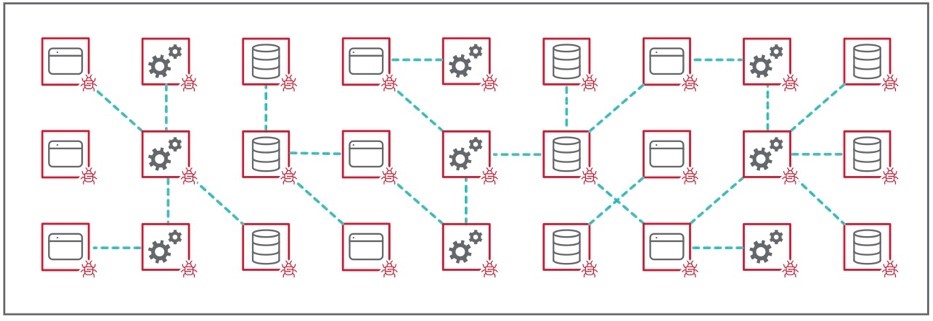
That’s where a microsegmentation solution like Illumio can help you secure these vulnerable parts of your network. No matter where a breach happens, microsegmentation will block it from reaching critical resources that you’ve segmented. The breach will be isolated to the other side of that segment so it can’t cause further damage.
4. Label workloads by business functions, not network addresses
In today’s modern networks, workloads are deployed across a hybrid, multi-cloud architecture. This makes network addresses ephemeral. A workload’s network address can change dynamically depending on the underlying hosting environment.
That’s why you should label workloads using human-readable labels rather than traditional IP addresses. With a microsegmentation solution like Illumio Zero Trust Segmentation, you can identify workloads by their business function or ownership — such as their role, application, environment, location, operating system, or business unit — which is a lot more informative their using an IP address.
Illumio’s labelling tools can:
- Change workload labels as dynamically
- Import labels from existing labeling structures, such as a configuration management database (CMDB)
- Recommend labels based on applications and traffic it discovers across managed environments

By using human-readable labels, you get a metadata-driven solution for seeing how segments between workloads are enforced that is fully decoupled from network address.
5. Decide on an agent and agentless approach
When building microsegmentation, it's important to understand when an agent or agentless approach works best. Some solutions like Illumio give you a choice between using agents or not so that you can get visibility and segmentation across all workloads in every environment.
Agent approach
The Illumio virtual enforcement node (VEN) agent collects telemetry about application use on and between workloads. This allows you to control access to segments directly at the workload.
Agentless approach
Illumio can also discover and enforce the use of segments without an agent.
This is crucial in environments that can’t support agents, like IoT devices in the manufacturing or healthcare industries. It’s also key in environments that can’t use agents because of compliance requirements.
- In a data center: Illumio can secure network switches that are deployed in front of devices that can't support agents. Illumio will collect network telemetry from the switches and convert label-based policy into access lists for the switches to use.
- In the cloud: Illumio can collect application and network behavior without an agent. It’ll convert the label-based policy and apply it to existing network enforcement points already in the cloud.
6. Start with a denylist model, then move to an allowlist model
A common challenge teams run into when building microsegmentation is that they know the ports they want to deny, but they don’t fully understand all the ports they need to allow for applications.
Ransomware commonly uses ports such as Remote Desktop Protocol (RDP) and Server Message Block (SMB) to move across segments between workloads. But we know that these ports rarely need to be open between workloads.
That’s why it’s best practice to start with a denylist model. Block only the ports you know shouldn’t be open and allow all others. Then, when you have a full understanding of what ports applications need, you can switch to an allowlist model. Keep only the required ports open and block all others.
This approach allows you to begin building microsegmentation by ransomware today and tightening policy when you’re ready.
7. Model policy before it’s deployed
Cybersecurity has long relied on a deploy-and-pray approach. Security teams create a policy model and modify it until it looks correct. Then, when it’s deployed, they pray the phone doesn’t ring from broken application dependencies.
That’s why it’s best to test your policy before it's fully deployed. With Illumio, you can create policy and then put it into monitoring mode. This will highlight any issues the policy could create once it’s deployed so you can fix them before they interrupt operations.
Modeling ensures your policy can be deployed safely without the risk of inadvertently breaking application dependencies.
8. Extend consistent segmentation across the hybrid multi-cloud
If you use a solution that can only build segmentation in the data center, then you’re unlikely to get consistent security in other environments like the cloud. Segmentation should never be dependent on a single environment. This will result in a siloed approach to segmentation which will only leave vulnerabilities and make it harder to stop and contain breaches.
Instead, microsegmentation needs to follow the workload as it migrates across environments. This ensures that segmentation doesn’t break as workloads are hosting in different environments.
With Illumio, you can build consistent segmentation policy across your cloud, endpoint, and data center environments. This allows workloads to migrate between environments with one consistent microsegmentation model that works the same across the entire architecture.
9. Automate security changes without relying on human decisions
Malware spreads faster than any human can type on a keyboard. It’s crucial to have a microsegmentation solution that can automate policy changes as fast as a breach can spread.
Using Illumio’s rich library of APIs, you can integrate Illumio with your SOAR solution. The SOAR tool will discover open ports that malware is using to spread through the network. Then, the tool will send Illumio an API call to immediately shut down at-risk ports.
All of this happens without relying on human intervention.
10. Prove security is in compliance
Quantifying risk can be challenging, since securing applications and segments can involve many moving parts. During an audit, it’s not always easy to get a clear picture of existing risk and how it’s lowered after security policy is applied. It’s important to use tools that show this before and after comparison.
With Illumio’s Vulnerability Maps, you can quantify risk with a score that combines risks discovered by Illumio and external scanners. The tool will then recommend modified policy that will reduce risk.
This allows auditors to get a clear before-and-after score for an environment’s exposure risk, eliminating your team’s compliance guesswork.
Ready to learn more about Illumio ZTS? Contact us today for a free consultation and demo.
.png)



.webp)
.webp)
