Integrating Visibility and Rule Creation for Efficient Workload Security
Workload security has two broad requirements: visibility and enforcement. Organizations need to be able to see what's going on between workloads across the entire hybrid cloud fabric, then take that information to determine what types of traffic should and shouldn't be permitted between workloads. These capabilities are essential to accurately defining a workload-to-workload policy model for Zero Trust Segmentation.
With the latest release of Illumio Core, we provide a streamlined workflow for visibility and rule creation using Illumio Explorer — making it far easier to create a scalable and automated workload policy model.
What is Explorer?
The Explorer feature allows authorized users to search a historical traffic and events database to see:
- The impact of policies and rules on application groups and workloads
- Workload-to-workload traffic that’s allowed, blocked and potentially blocked
Because Illumio's policy model is independent of the underlying network and cloud fabric constructs, Explorer displays all workloads across your entire IT infrastructure. Labels are applied to workloads to describe functionality, such as a "database" workload, and make it easy to group workloads based on business functions. Explorer shows exactly what traffic is active between all workloads across all functions.
For example, in a brownfield environment, new IP addresses will often appear and change dynamically, which Explorer displays dynamically. As workloads are added, deleted or changed, these events will be visible in Explorer along with the active flows between workloads.
Now, users can select flows and define rules for those flows from the same view within Explorer.
How to create rules directly within Explorer
A streamlined workflow is necessary to achieve an efficient operational model. Jumping back and forth between visibility workflows and rule creation workflows is time-consuming and increases the possibility of human error. The weakest link in any security model is a human typing on a keyboard — the fewer opportunities for human error, the better the chance of success in defining the correct policy model.
In addition to security architects defining policies, your workload security tool should be able to automatically determine the scope and existing rulesets to which any new rule can be added. If this isn’t possible, security administrators should be able to modify the scope and create any new rule as needed, directly from within the workload visibility workflow.
With our latest release of Illumio Core, all these tasks can be achieved from within Explorer, eliminating the need to perform each in a different workflow. From within the Draft mode in Explorer, all connections are aggregated by labels in the “Label-Based Connections” view, as shown here:

From this Explorer view, a security administrator can select specific connections and either add them to existing scopes or create new ones. A new button has been added to the Explorer Draft mode, “Allow Selected Connections," which enables the Illumio Policy Compute Engine (PCE) to recommend scopes to which selected connections can be added:

If a security administrator doesn't want to use any of the suggested scopes, they can add rules to the ruleset and modify them as needed:
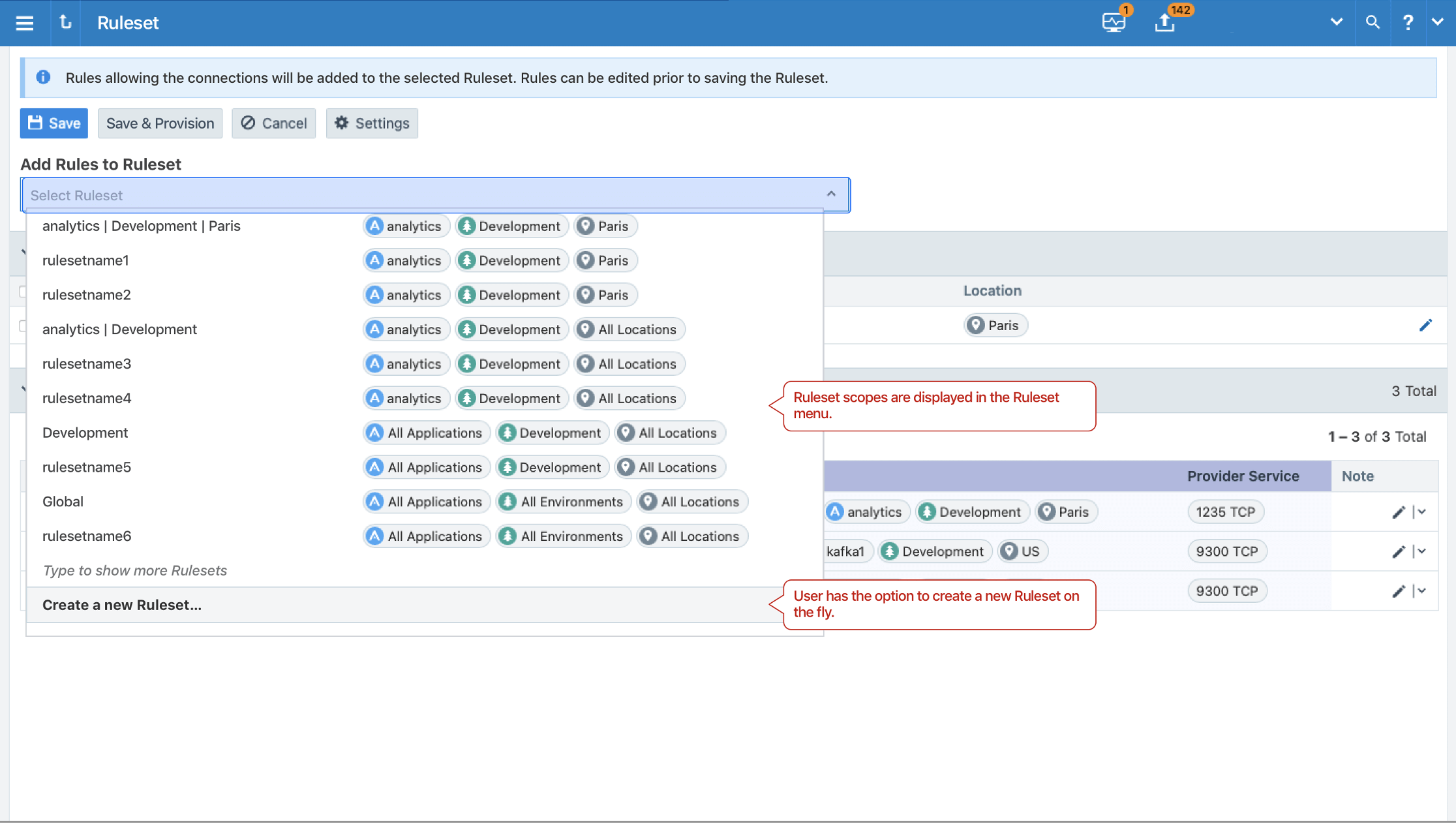
Once the rules are accepted or modified and saved, they're displayed in the main Explorer window:

Two workflows, one view: safer, streamlined workload security
Workload traffic patterns are difficult to discover using tools that reside within the network or cloud fabric. For consistent protection wherever workloads live, whether in the cloud or on-premises, you need a solution that implements visibility and security directly at the workload level.
Illumio's latest innovation in Explorer is an example of our commitment to optimizing user experience and making workload security more efficient and scalable.
Combining visibility and rule creation workflows greatly simplifies the operational tasks of discovering and controlling workload policies, reduces the possibility of human error, and ultimately saves teams time.
To learn more:
- Contact us for a demo of Illumio Core and the Explorer updates.
- Read how Hi-Temp Insulation benefits from Explorer capabilities.
.png)


