Operationalizing Zero Trust – Steps 2 and 3: Determine Which Zero Trust Pillar to Focus On and Specify the Exact Control
This blog series expands on ideas introduced in my March post, “Zero Trust is not hard … If you’re pragmatic”.
In that post, I outlined six steps to achieve Zero Trust. Here, I will delve more deeply into two of the six steps outlined to provide a solid framework that can be used by micro-segmentation practitioners in organisations large and small to make their projects more successful. Before I begin, here’s a visual representation of each step:
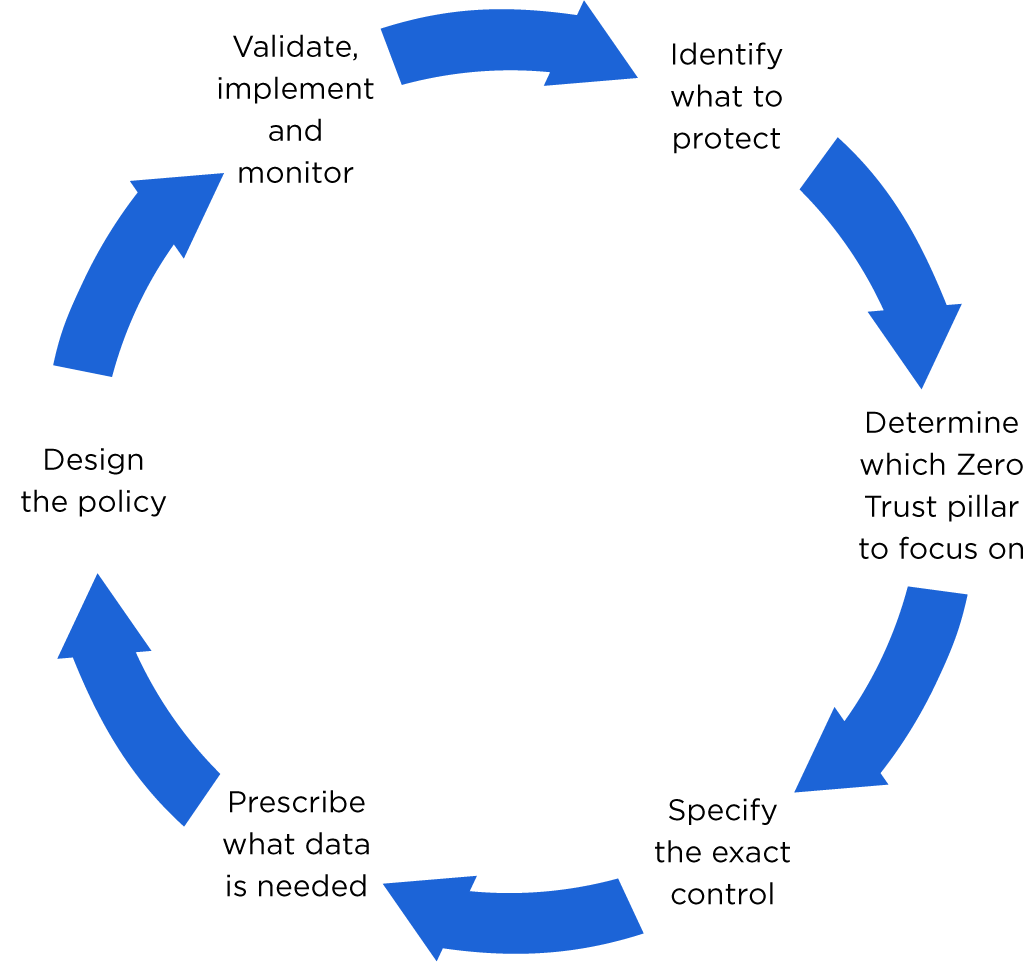
Step 2: Determine which Zero Trust pillar to focus on
In part 1 of this series, I looked at “Identifying what to protect” and recommended that to achieve your long-term goal – enterprise-wide adoption of Zero Trust – it was wise to start small, and look for candidate applications that ideally matched at least 2 out of the 3 criteria listed below:
- Have a strong driver to adopt Zero Trust security principles – i.e. a compliance or regulatory requirement, an audit finding that needs to be addressed, or a response to a breach.
- Are marked as critical applications.
- Have a willingness to be guinea pigs.
Imagine I have hunted round my organisation and have found an application that handles PCI data and, hence, needs to be compliant with PCI-DSS requirements. It also happens to have an audit finding around ‘excessive network access’, is marked as a critical component in my customer payments system, and, after much convincing, the application team has agreed to work with me in adopting a Zero Trust framework to properly secure their application. If I quickly scan back to my list of selection criteria, I can see that my chosen application ticks all 3 requirements.
So, now I move on to determining which Zero Trust Pillar to focus on in this iteration – here’s what the pillars are:

In the same way that you should take a very focused approach when identifying what applications to protect at this stage, you should apply a similar attitude when determining how to approach Zero Trust itself. Attempting to address every single pillar in one cycle would be ambitious and unrealistic – as you would likely need to implement a diverse set of controls and technologies, which would hamper the recommended objective of making relatively quick and measurable progress.
Forrester actually provide a Zero Trust Maturity Model Assessment Tool to help practitioners identify gaps in their organisation’s adoption of Zero Trust and these results can be used to identify the specific Zero Trust pillar(s) to focus on. Let’s assume you have run this assessment against my chosen application and it identifies significant gaps in the protection of workloads running the application – and specifically it highlights that they are easily accessible from across my network. This would lead you to focus this particular iteration on protecting the workloads that host your application, ensuring that you gain excellent visibility in this area.
Step 3: Specify the exact control
Workload protection encompasses many security capabilities including, but not limited to, effective securing and patching of the OS and any installed applications, host-based threat protection controls such as antivirus, EDR, file integrity monitoring, host-based firewalling, etc.
Step 2 of the Zero Trust Maturity Assessment has identified excessive network access to the application workloads as the most significant gap in Zero Trust, so I recommend focusing on host-based firewalling, or more generally micro-segmentation, as the security control to apply in order to move your application one step further forward in its Zero Trust journey.
From my own personal experience as a practitioner before joining Illumio, I know that in order to effectively implement micro-segmentation, you need excellent visibility into your application’s upstream and downstream dependencies, so that you have the right information with which to build and validate the least privilege, whitelist-based, Zero Trust policies that will protect your workloads.
So, when you focus on workload protection and the visibility and analytics associated with this, and have further clarified that you plan to only build micro-segmentation controls at this stage, you are now ready to identify the input data needed to make this vision a reality. And that’s exactly what I will focus on in the next edition of this series.
Can’t wait for my next post to learn more? Visit our page on how to operationalize your Zero Trust strategy with micro-segmentation to get the inside scoop.
.png)

.webp)
