Pair ZTNA + ZTS For End-to-End Zero Trust
As the cybersecurity landscape has shifted to accommodate the rise of remote work, it's clear that a multi-faceted approach to security is essential. Organizations are turning to Zero Trust security strategies to secure their increasingly complex networks and distributed workforce as the best way to bolster cyber resilience.
Two technologies that are foundational to any Zero Trust strategy are Zero Trust Network Access (ZTNA) and Zero Trust Segmentation (ZTS).
While ZTNA provides controls access, a foundational layer of Zero Trust security, its focus is primarily on north/south traffic. This is where Zero Trust Segmentation becomes critical, addressing the overreliance on access control with extensive traffic visibility and precise east/west lateral movement control.
Keep reading to learn why your network has security gaps if you aren’t pairing ZTNA + ZTS.
ZTNA leaves security gaps
According to Gartner, ZTNA creates an access boundary around applications based on identity- and context. Before access is permitted, the solution’s trust broker verifies identity, context, and policy adherence. This stops lateral movement in the network and reduces the attack surface.
Unfortunately, many organizations are overrelying on ZTNA’s north/south access control, falling back on the outdated idea that cyberattacks can be prevented from entering the network perimeter completely.
But in today’s threat landscape, breaches are inevitable — security for only north/south traffic overlooks the risk of lateral movement within a network when a breach does happen. This is where ZTS, particularly at the endpoint, becomes indispensable.
Endpoints require ZTS
End users are a prime target for threat actors because they can be tricked into performing actions through social engineering, phishing, or device tempering. Traditional endpoint security solutions claim to stop breaches, but the reality is that devices still get breached. According to ESG research, 76 percent of organizations experienced a ransomware attack in the past 2 years.
Once an attack breaches an endpoint device, attackers can move freely to other endpoints or through the rest of the network, looking for your most critical assets and data. Without ZTS in place, this can happen for days, weeks, even months without detection or remediation.
ZTS prevents lateral movement – if the ports aren’t open, attacks can’t spread.
ZTNA + ZTS: A more comprehensive approach to Zero Trust security
It’s critical that organizations pair their north/south ZTNA solution with ZTS’s east/west protection. By managing and limiting east/west traffic, ZTS addresses the gaps that ZTNA solutions can leave open.
ZTNA secures access to the perimeter and limits access, while ZTS strengthens internal network defenses, addressing both external and internal threats for a multi-layered Zero Trust security posture.
Choose Illumio ZTS to pair with your ZTNA solution
Illumio Endpoint extends ZTS to end-user devices and can easily integrate with your exiting ZTNA solution. Watch a demo here.
See endpoint traffic
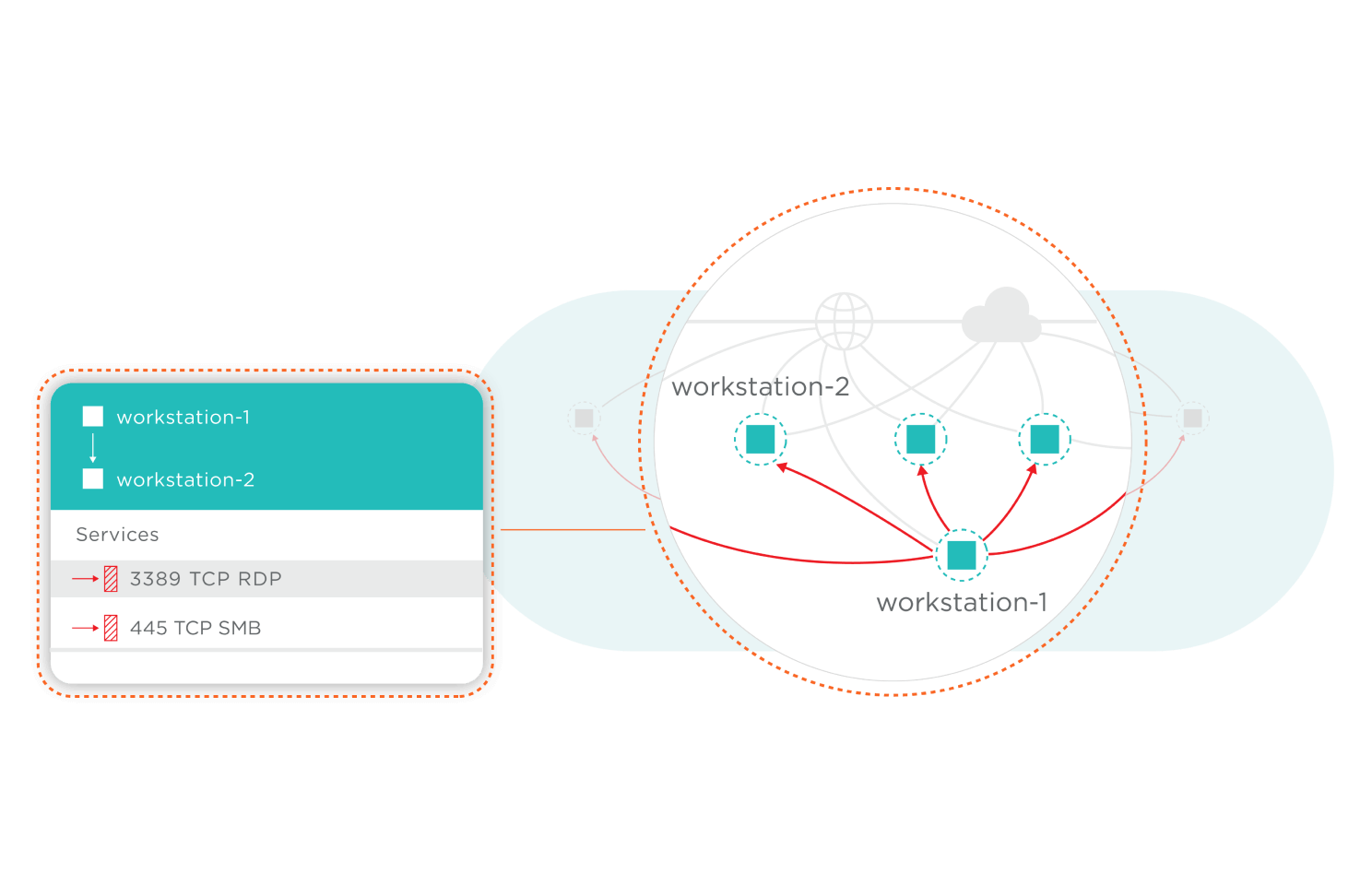
Illumio Endpoint goes beyond traditional network visibility by providing visibility into endpoint traffic, not just for devices in the corporate environment but also for remote devices.
Visibility is crucial for monitoring not just endpoint-to-server interactions, but also the often-overlooked endpoint-to-endpoint communications. Such comprehensive visibility enables organizations to identify and mitigate risks associated with lateral movement within the network.

Control endpoint-to-endpoint traffic
Controlling the traffic between endpoints is vital in a world where one wrong click from a user can be the start of a major breach by allowing an attacker to move laterally across the network. Illumio Endpoint enables organizations to define and enforce policies based on labels to granularly control what communication is allowed, ensuring that only necessary, traffic is permitted.
Secure endpoint-to-data center connectivity
When an attack inevitably breaches end-user devices, its goal will be to spread through the rest of the network, including to your cloud and data center environments. Illumio Endpoint in combination with Illumio Core and Illumio CloudSecure stops lateral movement and ensures your organization is resilient against attacks.

Share policy labels with your ZTNA solution
Illumio Endpoint’s policy model is a label-based system, which means that the rules you write don't require the use of an IP address or subnet like traditional firewall solutions. You control the range of your policy by using labels. You can share this context with your ZTNA solution, allowing you to easily build rules and understand traffic between the two solutions.
Curious to learn more? Test drive Illumio Endpoint with our hands-on, self-paced lab.
.png)





