Bishop Fox: Testing Zero Trust Segmentations Effectiveness Against Ransomware
The race to innovate between cybersecurity and ransomware oftentimes feels like an endless game of cat and mouse. Constant work from organizations to stay better protected has often been met with frustratingly little ground gained.
Why is this? It’s a longstanding question that Paul Dant, Illumio’s Senior Director for Cybersecurity Strategy, and Trevin Edgeworth, Bishop Fox’s Red Team Practice Director, set out to answer in this month’s webinar, Enhancing Your Ransomware Defenses Through Zero Trust Segmentation.
Download a copy of Bishop Fox’s Ransomware Scenario Emulation 2022: Assessment Report to see how Zero Trust Segmentation renders attackers ineffective in less than 10 minutes.
How ransomware stays ahead of cybersecurity efforts
Dant and Edgeworth broke down exactly why ransomware always seems to be a step ahead of the cybersecurity industry’s best efforts.
“I think we have gotten better, but at the same time so have the adversaries,” said Edgeworth, a decades-long veteran of offensive cybersecurity. “The threat actors continue to evolve just as we do. You have sophisticated human-led types of attacks that are super customized to every environment.”
Another issue Edgeworth highlighted was basic security best practices: “Vince Lombardi, the legendary football coach, once held up a football and told his players, ‘This is a football.’ Lombardi motivated his players by urging them to stick to the basics. Those boring basics are what lead to successful cybersecurity.”
Finally, there’s lateral movement which is the way ransomware and breaches spread throughout a network.
“What makes it too easy [for ransomware] is that ability to move laterally, even if it involves just a single compromised system on a particular network,” said Dant. Hackers all too often leverage a single weak point in an attack surface as a gateway to make lateral movements and scour a company for its most critical assets. This allows hackers to cause the most pain and urgency.
Crafting the perfect Zero Trust Segmentation testing environment
So how do organizations better prepare for this onslaught of tools and opportunities at the hackers’ disposal?
Bishop Fox intricately constructed a methodology to test the Illumio Zero Trust Segmentation Platform against the intricacies of real-world attacks.
Edgeworth described a sort of live-fire testing environment in which Bishop Fox played the role of both sides, the attackers and the defenders.
“Since Bishop Fox was playing both the red and the blue side, we wanted to design the methodology in a way that reduced the potential for bias,” said Edgeworth. “We wanted to craft as realistic a scenario as possible and to run that scenario across a variety of different defensive configurations. This would allow us to compare and contrast how each of those environments did against a similar attack.”
The methodology called for four distinct defensive configurations, each more robust than the last:
- An untouched control scenario with no Illumio capabilities
- A detection and response model with monitor mode only
- A preconfigured static protection with a basic segmentation policy keyed towards known and common ransomware strains
- Full-on application ring fencing, including custom Illumio Zero Trust Segmentation policy with its own rules
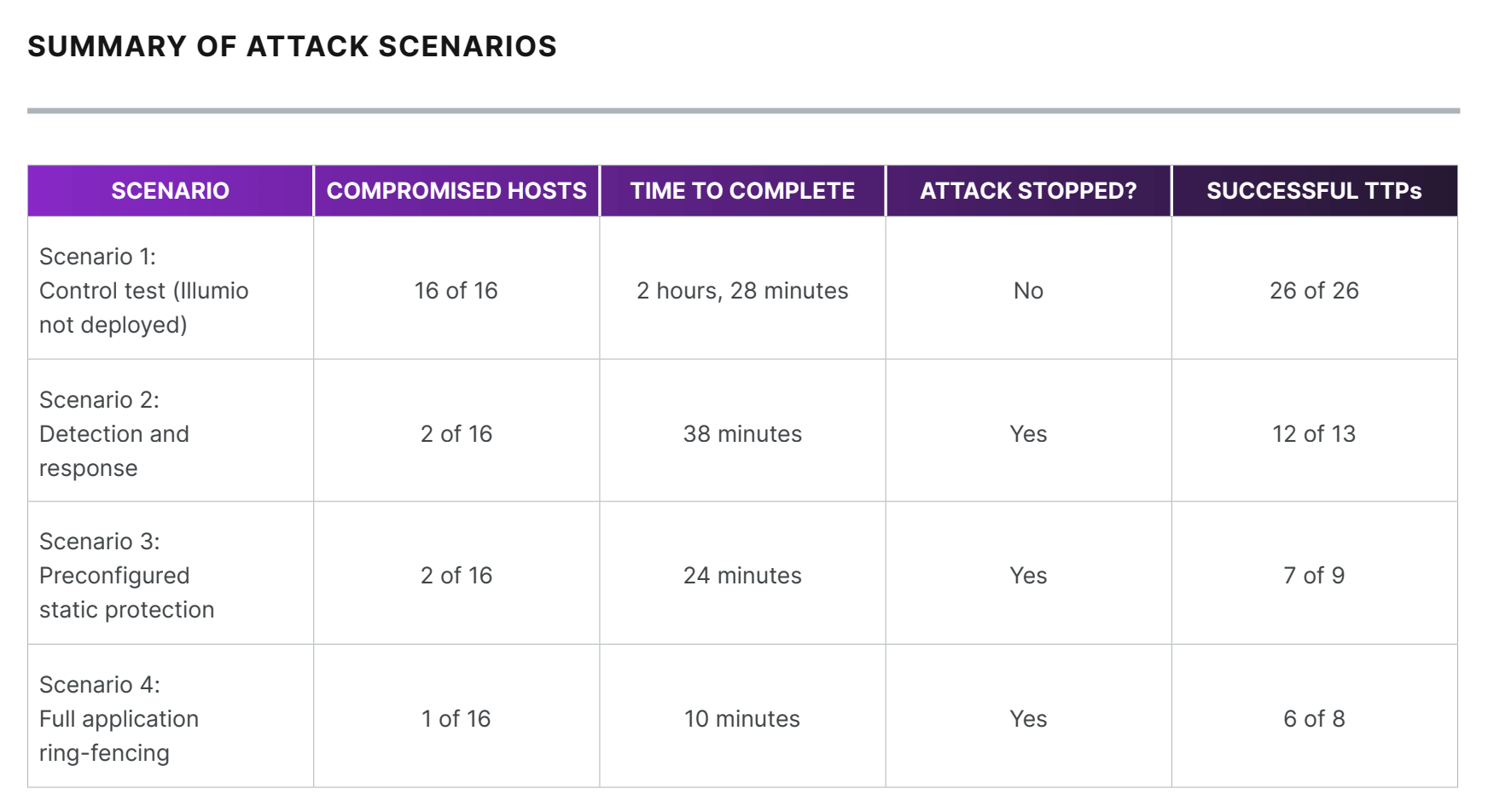
Each configuration was tested against the same attack pattern, allowing for comprehensive data to be gathered gauging each system’s effectiveness. As an ethical hacker in the past, Dant noted the test’s accuracy which mapped incredibly well to the expectations of what attackers would be throwing at organizations.
Interpreting Bishop Fox’s emulation data
After each phase had been tested, the resulting data made things crystal clear.
With each of Bishop Fox’s emulated attack, there were fewer compromised hosts, shorter times to detect and contain, and fewer successful TTPs run by the attackers.
With Illumio Core fully deployed in phase 4, the attack was snuffed out in an astonishing 10 minutes.
“There’s no better way to prove it than by actually simulating the threat in your environment and dissecting those results,” Edgeworth pointed out.
The rigor of Bishop Fox’s testing environment further legitimized Zero Trust Segmentation and the Illumio Zero Trust Segmentation Platform.
“I can very clearly see how Zero Trust Segmentation is such a valid control in preventing lateral movement,” said Dant. “Not only are we achieving a new level of visibility, but we’re also allowing an organization to feel confident that if an attacker is able to compromise some point in the network, ZTS would make it very hard for that attack to be carried out.”
Contact us to schedule a consultation and demo with our Illumio experts.
.png)


