How to Meet CISA’s Phobos Ransomware Guidance With Illumio
Recently, the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Multi-State Information Sharing and Analysis Center (MS-ISAC) released a new cybersecurity advisory aimed at informing government and critical infrastructure organizations on how to protect against Phobos ransomware.
In this blog post, learn what Phobos ransomware is, how government officials recommend preparing for Phobos, and how Illumio’s Ransomware Protection Dashboard can help achieve these recommendations.
What is Phobos ransomware?
Phobos ransomware is related to multiple ransomware variants, including Elking, Eight, Devos, Backmydata, and Faust ransomware. The Backmydata variant was used in a February 2024 attack in Romania that resulted in systems being taken offline at around 100 healthcare facilities.
The advisory shares known tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) associated with the Phobos ransomware variants observed as recently as February 2024. Phobos operates as a ransomware-as-a-service (RaaS) model and has been targeting various sectors since May 2019, including government, emergency services, healthcare, and education.
How to secure against Phobos ransomware
The advisory provides three key takeaways to mitigate Phobos ransomware activity:
- Secure RDP ports to prevent threat actors from abusing and leveraging RDP tools.
- Prioritize remediating known exploited vulnerabilities.
- Implement EDR solutions to disrupt threat actor memory allocation techniques.
The Illumio Zero Trust Segmentation Platform can help you tackle all three of these recommendations.
1. Use Illumio’s Ransomware Protection Dashboard to secure RDP ports
With just a few quick steps, your organization can make major improvements towards thwarting bad actors and preventing lateral movement within your environment. If you can prevent lateral movement, you ensure that even if attackers get in, they don’t make it very far or access mission-critical applications.
Let’s walk through the three steps to securing RDP ports using the Ransomware Protection Dashboard:
- Identify where there is RDP traffic in your environment
- Follow the recommended actions on Illumio’s Ransomware Protection Dashboard
- Measure the improvement in the ransomware protection score

Identify RDP Traffic in your environment
Illumio’s Ransomware Protection Dashboard easily tracks the highest risk services in your environment. One of these services is RDP. If it is exposed in your environment without policy controlling it, you may see it in your Top 5 Risky Services report. Alternatively, you can also head to the map to search specifically for RDP traffic.
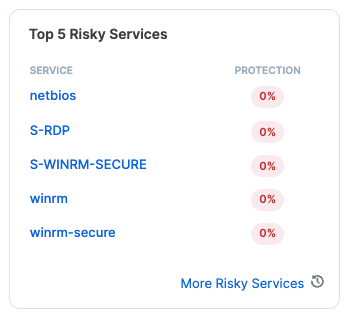
In the image above, you can see that RDP is listed in the top five risky services, but also there’s no policy in place controlling this service.
This is where you can do business analysis to understand the impact. For example, there are certain people in the organization who need the ability to use RDP. This is very useful for IT who may be helping employees not on-site to troubleshoot an issue. However, it isn’t something the average workload needs to have available.
This is where the dashboard’s recommended actions come into play.
Follow the Ransomware Protection Dashboard’s recommended actions
One of the recommended actions on the dashboard is to build a deny rule. This is an easy way to rapidly build protection as you progress along what may be a larger Zero Trust journey.
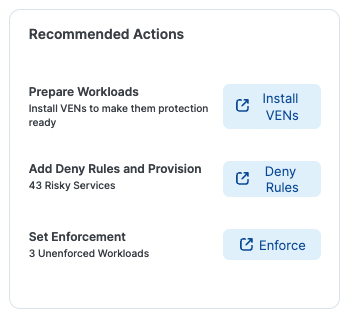
In this case, since CISA recommends to secure RDP ports, the next step is to build a deny rule to block this traffic. Exceptions can be added as needed, but generally this will be locked down. This provides proactive protection against any Phobos ransomware attacks.
When you apply deny rules with Illumio, your new policy is deployed across your organization in minutes, no matter the scale.
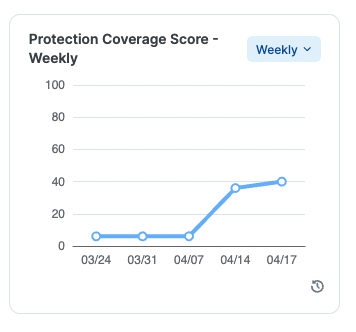
Measure security improvement in the Ransomware Protection Score
One great way to measure your progress in protecting your environment is with the dashboard’s Ransomware Protection Score. As you deploy policy and make major changes, such as blocking RDP traffic, you can see that score tick up.
Illumio not only provides your current score but also this score over time. This is a great way to measure how you are protecting your organization against ever-evolving threats.
2. Remediate known exploited vulnerabilities with Zero Trust Segmentation
Zero Trust Segmentation (ZTS) can help you reduce the impact of ransomware attacks like Phobos by seeing and addressing where vulnerabilities in your network have been exploited.
See and fix security gaps
The Illumio Map helps reveal systems or applications with excessive, unnecessary, or non-compliant communication. It can even combine this information with data from vulnerability scanners.
Using this insight, security teams can set granular, flexible segmentation policies to reduce vulnerability exposure and stop the spread of inevitable breaches. By understanding context and exposure, workloads can be secured quickly before a patch is rolled out.

Quantify risk with data-driven insights into vulnerabilities
In the face of threats like Phobos ransomware, it's crucial to not only identify but also quantify potential vulnerabilities within your network. Illumio shows network weak points so that teams can implement proactive measures precisely where most needed.
This insight arms cross-functional teams with actionable insights for addressing securing gaps, fostering data-driven decision-making and enhancing risk mitigation strategies across the entire environment.
Proactively build vulnerability defenses
Model, test, and deploy granular segmentation of high-risk assets as a compensation control, shielding critical systems when patching isn’t feasible or will introduce unacceptable operational complexity.
Awareness is key. If traffic connects to a port with a known vulnerability, the security operations center (SOC) gets alerted of the violation, including the vulnerability and severity context with data provided by Illumio.
3. Combine EDR and Zero Trust Segmentation to detect and automatically secure against lateral movement
Illumio complements EDR by reducing the attack surface with Zero Trust Segmentation policies that leave attackers little room to maneuver. Illumio fills the gap between incident and detection, agnostic from attack pattern.
Per the cybersecurity advisory, EDR is an important piece of protecting against ransomware attacks such as Phobos. But when an attack eventually does breach an endpoint, EDR has no way of preventing that breach from continuing to move laterally through your organization’s network. That’s why it’s essential to combine EDR with ZTS. When the EDR system detects a breach, ZTS can automatically shut down and quarantine any infected workloads.

Combining proactive technology like ZTS with reactive technology like EDR on every endpoint lessens the dwell time weakness while also significantly increasing response capabilities. In fact, according to testing by Bishop Fox, combining EDR with Illumio radically reduced an attacker from spreading while detecting 4 times faster.
Get in touch with us to learn how Zero Trust Segmentation can help you meet CISA’s guidance and stop ransomware attacks like Phobos today.
.png)





