Demystifying Ransomware Techniques Using .Net Assemblies: A Multi-Stage Attack
In part one of this series, we looked at examples of programming capabilities that can be used by ransomware in their malicious techniques. Then in part two, we also examined the fundamentals of Microsoft’s .Net software framework and associated assemblies of EXE and DLL to understand how these capabilities are made possible.
In this final part, we will combine everything that has been discussed so far into a set of staged payloads to demonstrate the fundamentals of a multi-stage payload attack.
Payload and attack setup
We begin by laying out the payloads that will be used for the attack. All the previous capabilities including new ones will be taken into account to create the staged payloads. This is to demonstrate overall how the different tactics and techniques we have seen so far can be put together as is typically the case of ransomware.
We are going to use the following payloads:
- Initial EXE application: Stager payload
- Main ransomware EXE: Stage-1 payload
- 2nd main ransomware DLL: Stage-2 payload
The use of multiple payloads to accomplish different tasks in this attack example constitutes a multi-stage attack. Looking back at the previous series on malware payloads and beacons, part two discussed types of malicious payloads in more detail. There, I explained the difference between a stager versus staged payload types. In summary, a stager is an often smaller initial executable application that can act as the downloader, dropper, and/or payload for a more capable and often bigger main payload file known as the stage. The purpose of the stager payload is to set up the main stage. In this attack example, using payload staging as described above, the different payloads will have the various tasks as follows:
Stager EXE payload will do the following:
- Evasion techniques
- Downloads two ‘text’ files to disk. These files are in fact an EXE and DLL.
- Launch the 2nd EXE file
- The stager then exits
- The running 2nd EXE (stage-1) loads the DLL (stage-2)
Stage-1 EXE and Stage-2 DLL payloads then perform the following malicious ransomware actions:
- Evasion techniques
- Discovery
- Process manipulation
- Drives and files enumeration
- Encryption of files
Stager: Initial payload executable (EXE)
The attack begins with our initial payload, the stager delivered to the victim machine. Often this is via social engineering techniques like phishing. Once the initial payload is delivered and run, it will begin executing the malicious set of instructions.
Evasion
It will first wait a specified time without performing any actions. This is an evasion technique designed to outlast virtual machine threat analysis. After this, it will download a well-known executable from the Internet such as a notepad app. This is a decoy and another evasion tactic to avoid detection.
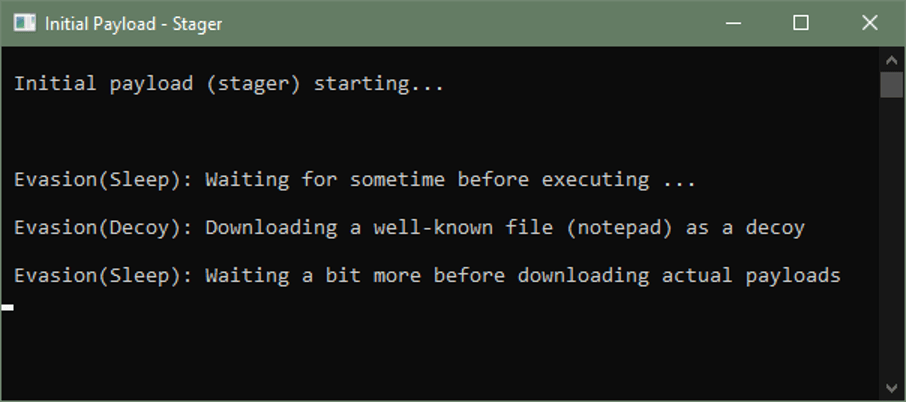
Other techniques can include checking for mouse clicks or checking document directories for evidence of files associated with normal use of a computer system as opposed to a sandbox virtual machine used for threat analysis.
Downloader, dropper, and loader
Once these initial evasion actions have been executed, the stager (initial) payload will again execute a third sleep action. It will wait again for a specified time before continuing the next set of instructions which will be to download the stage payload files. These files are remotely hosted by the attacker as shown below.
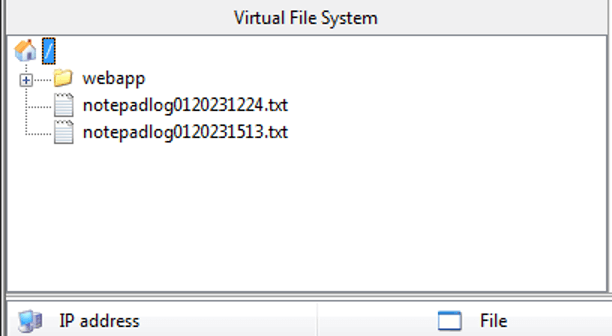
The stager then proceeds to download two text files “notepadlog0120231224.txt” and “notepadlog0120231513.txt.” This next phase is shown in red text in the example below.
Notice that the download links for the payload files are actually obfuscated using base64 encoding which was discussed as the fourth technique in the first part of this series.
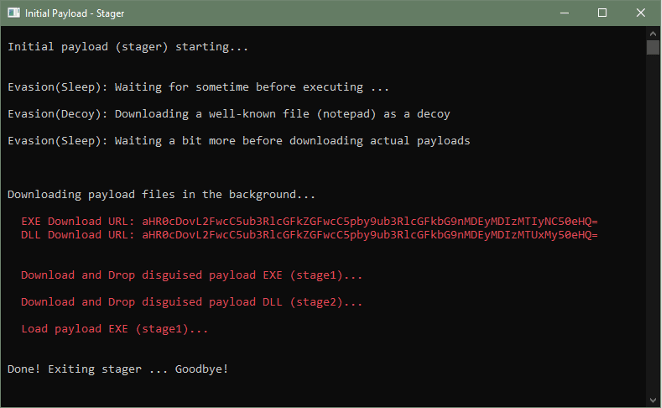
The initial payload converts the base64 internally on the fly to the original download links.
The two downloaded text files are actually an executable (EXE) and dynamic link library (DLL) respectively, disguised as text files. These are the stage-1 and stage-2 payloads for this multi-stage ransomware attack example. Upon successful downloads, these files are renamed to their original types.
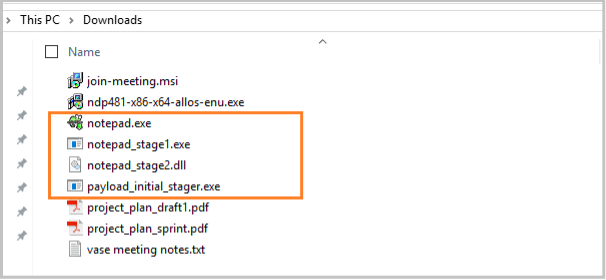
The stager payload then launches the stage-1 executable payload to begin the actual ransomware attack. The stager has now completed its purpose and exits once the stage-1 payload is loaded into memory and starts running. So, as discussed in the first technique in first part of this series, this initial stage payload is the downloader and dropper for the stage-1 EXE and stage-2 DLL payload and the loader only for the stage-1 payload. The DLL payload will be loaded as a stage-2 payload by the now running stage-1 EXE payload hence a multi-stage payload attack.
Stage-1 executable (EXE)
Once execution has been passed to the stage-1 executable, it will first sleep for a specified amount of time as shown below.
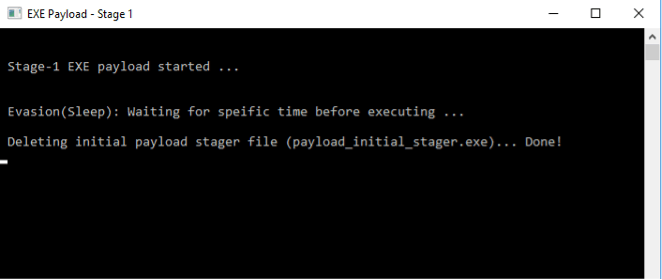
It will then delete the stager payload file “payload_initial_stager.exe” from the filesystem as a means of removing any evidence. In the example below, the file has been deleted and is no longer in the directory.
The stage-1 payload is now ready to execute its set of actions to continue the rest of the attack.
Discovery
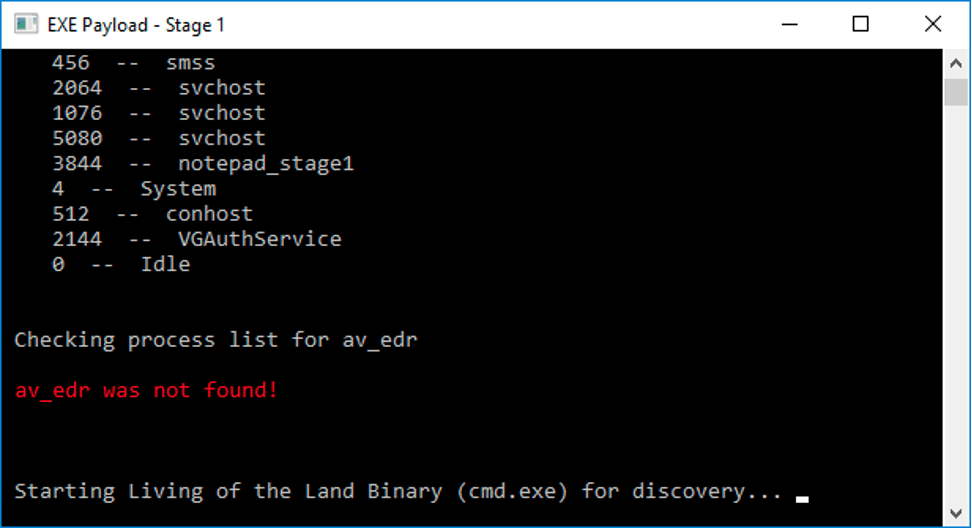
Next, it will perform some discovery techniques on the infected system. These discovery techniques allow a threat actor to understand a bit more about the infected system. Discovery helps the threat operator to make certain crucial operational security considerations to ensue overall success of the attack. In this example, the stage-1 payload performs a process list check. Some processes that might be of interest will be Endpoint Detection and Response (EDR), anti-virus (AV) or virtual machine processes. These help to understand the probability of the payload being detected.
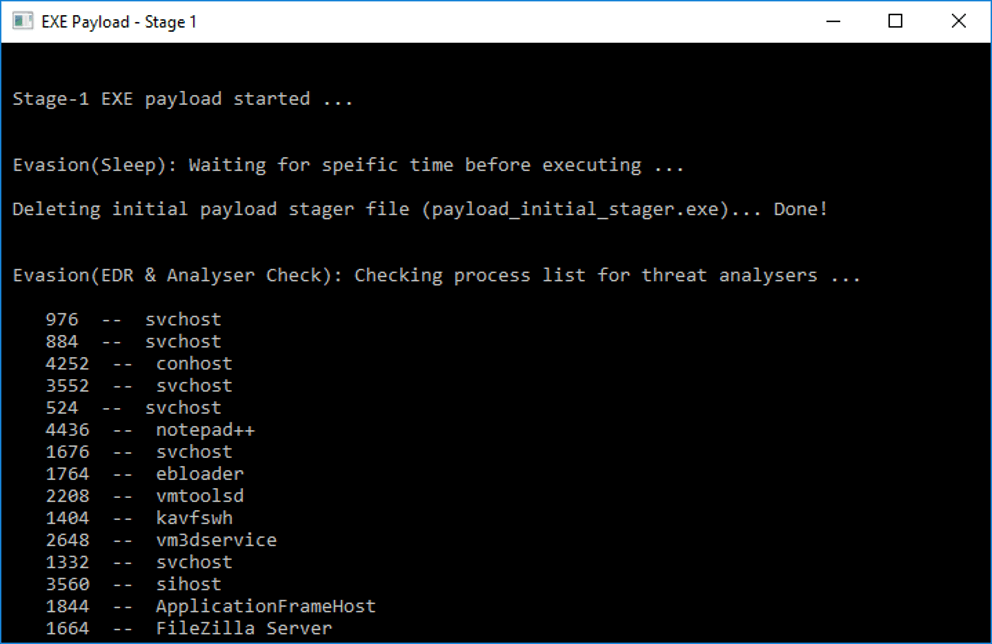
Based on the results of the discovery information, a threat actor can make some important operational security decisions. For example, if a well-known EDR process is found on the system or the payload detects virtual machine processes, then the payload can be instructed to exit to avoid detection.
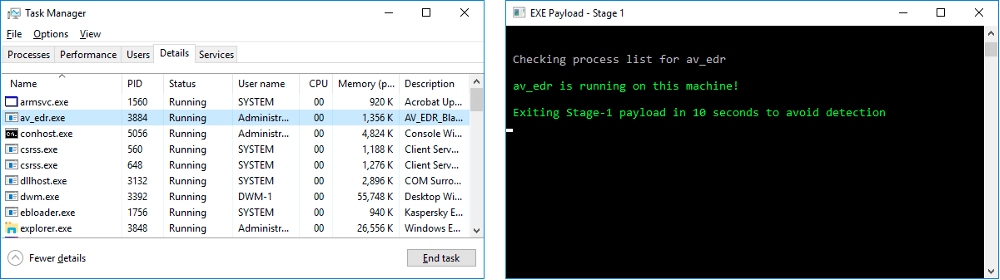
Alternatively, the threat actor can decide to employ additional evasion techniques to evade the EDR or even attempt to use other means to terminate the EDR process altogether.
Discovery also helps to determine how valuable the compromised system might be. For example, is it a production Database server or a payment system with valuable customer data? The more critical the system is to a business, the more likely a ransom will be paid for it.
Process manipulation: Living-off-the-Land (LotL) binaries
Another set of useful information is system-related information such as operating system, language locale, and hotfixes and updates installed or missing from the system. This type of information can help plan additional attacks such as vulnerability exploits.
Assuming the EDR process was not found, the payload will continue because the threat actor may be confident of dealing with other ones. So, after checking the process information, the stage-1 executable payload uses a Living-off-the-Land technique and launches a separate Windows command prompt as shown in the example below.
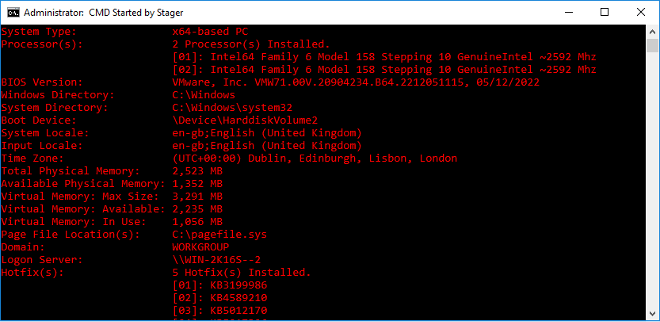
After the command prompt is launched, the payload passes some Windows commands to it to run. This command will generate system information such as system type, processor information, uptime, and hotfixes. A snapshot of the output is shown in red text in the example below.
Stage-2 dynamic link library (DLL)
As discussed in the previous articles, a DLL file contains computer code that cannot be executed by itself. So, in our example, the stage-1 EXE also uses code in the stage-2 DLL to finish off the rest of the attack cycle.
Stage-1 EXE loading stage-2 DLL payload
After the stage-1 EXE payload completes its actions, it proceeds to load the stage-2 DLL payload. The DLL payload contains the code that will be used for the final stages of the attack which is to check for the drives on the system and then encrypt selected files on those drives.
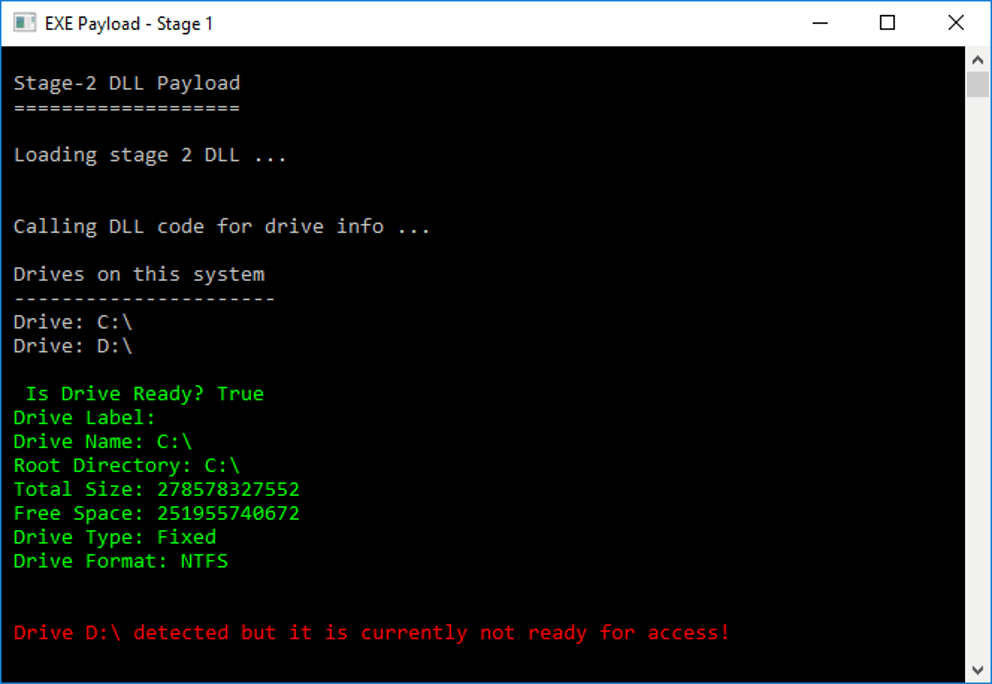
The DLL code first runs a drive check to find the drives on the infected system, listing useful information about each one. From the display above, of particular interest is information about the drives on the system which are ready for access versus the ones which are not. This helps target the files on the right drives for encryption and prevent errors by attempting to operate on drives that are read-only or cannot be accessed.
Encryption
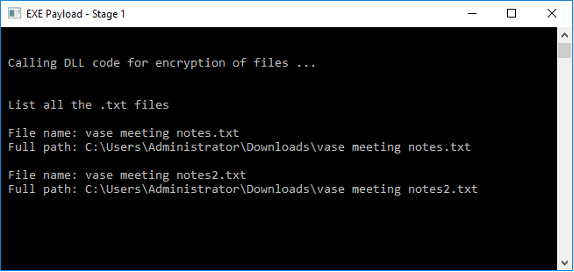
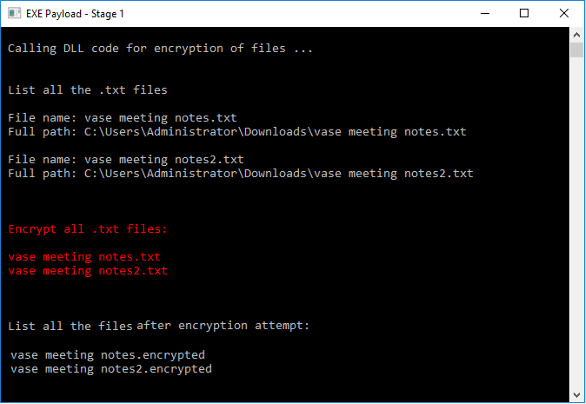
At this point, the encryption for ransom is now ready to go ahead. The encryption code in the stage-2 DLL first checks for a list of text files in the directory. This is because we will be encrypting only text files in this last demonstration. The payload then displays all the text files that were found.
The discovered files are then encrypted by the payload. The file extensions are also changed to “.encrypted” to show the encrypted text files.
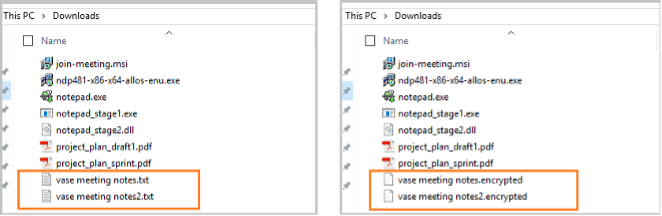
Below, we can also see the before and after images of the directory where the text files are located, showing the changes after encryption.
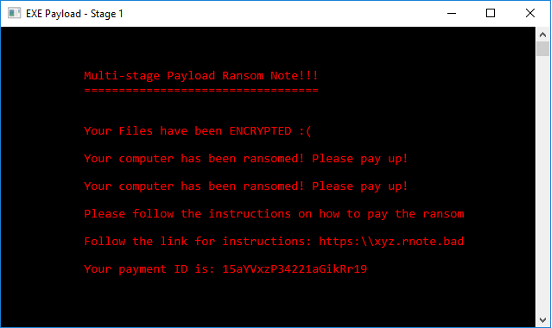
Finally comes the ransom note: This typically alerts the user to the fact that their files have been encrypted. It also instructs them on how to pay the ransom and get the decryption key to decrypt the files. In a lot of cases, paying the ransom does not automatically guarantee getting access to the decryption key.
Notice that in our example, we chose to put all the encryption code into a DLL file which became our stage-2 payload. This is primarily because, as discussed in the previous articles, a DLL is a library file which means it can be re-used. For instance, if as an attacker we chose to use a completely different stage-1 EXE payload, maybe because of new evasion enhancements in the future, we do not have to re-write the encryption part of our payload code to finalize that new attack campaign. We can simply pair our new payload with the existing stage-2 DLL file and have the new EXE load the DLL to encrypt files.
Mitigation against ransomware
Ultimately, ransomware will employ three main frontiers of infection, execution, and persistence.
These can be broadly categorized as:
- Filesystem
- Registry
- Memory
- Network (remote and local – lateral movement)
Defenders must therefore pursue building up the right toolsets and utilize them in the right ways for effective security mitigation. In part three of the previous series on malware payloads and beacons, there is a more detailed run through of defense-in-depth mitigation building on the philosophy of assume breach and cyber resilience.
This three-part series has demonstrated how the different tactics and techniques used by malware and specifically ransomware can come to be. By understanding these different tactics and techniques, defenders can be better placed to evaluate their existing cyber policies and defenses for effective countermeasures.
Want to learn more about protecting your organization from ransomware and breaches? Contact us today.
.png)



