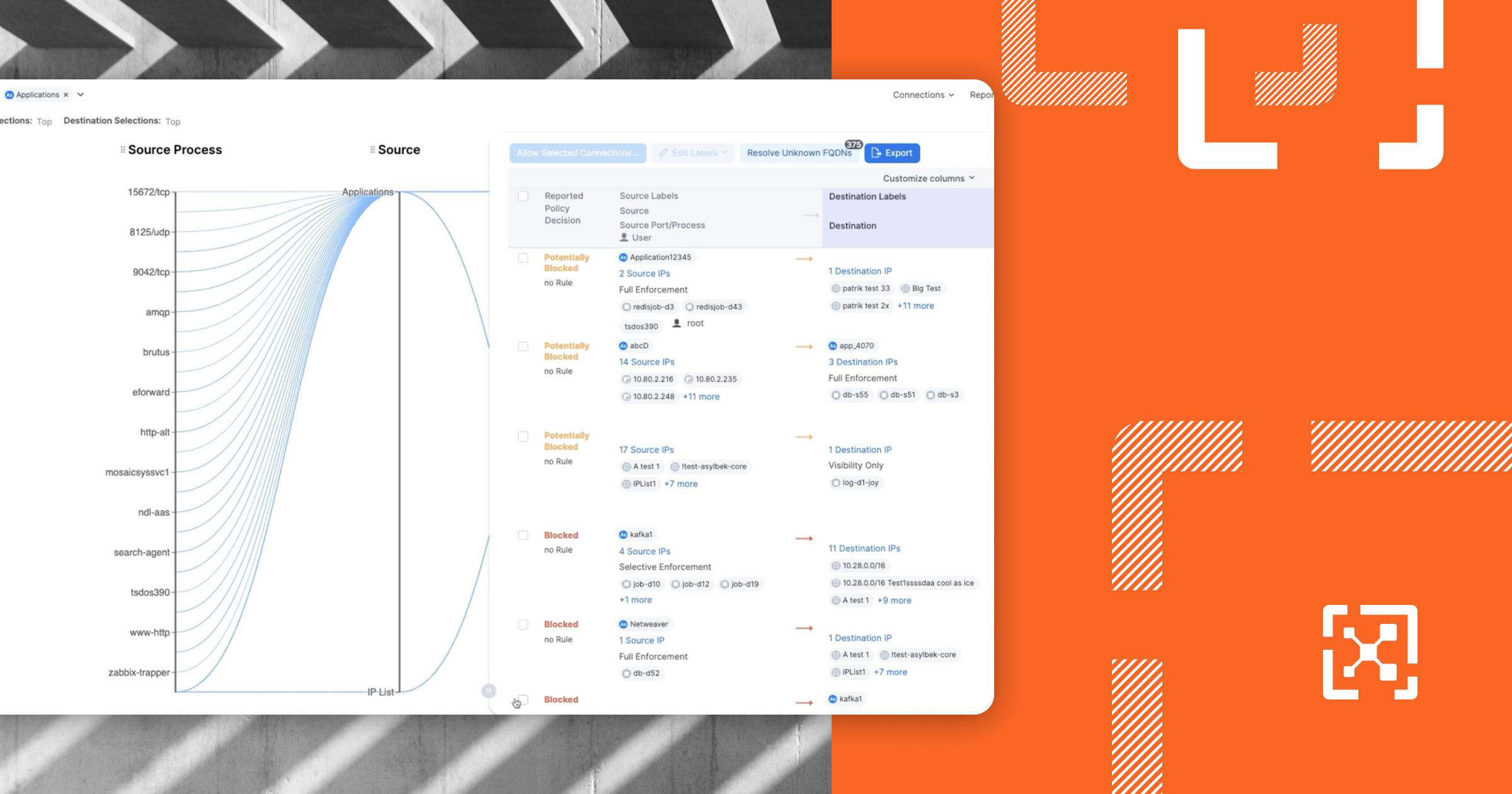
Little-Known Features of Illumio Core: The Illumio Map
You can't protect what you can't see. In the complexity of today’s network security, this principle emphasizes the indispensable need for comprehensive visibility into the intricacies of network architectures and data flows, addressing a challenge that has consistently troubled both network administrators and security experts.
At Illumio, we're all about finding novel and innovative solutions to understand how network communications flow. We constantly explore new methodologies to peel back the layers of network communication, aiming to uncover the finer details of connections, patterns, and relationships that often remain hidden.
That's the thought behind developing the Illumio Map visualization which goes hand-in-hand with our Mesh visualization. In this article, we'll take a closer look at what the Illumio Map visualization offers and how it can help your team see, segment, and secure your network better.
Key benefits of the Illumio Map
The Illumio Map visualization brings a transformative approach to understanding network architectures and flows, offering a suite of benefits that enhance the clarity and depth of network security analysis.
Here are some of the key advantages that the Illumio Map offers:
- Holistic network overview: The Map provides a comprehensive view of the entire network architecture, combining both macroscopic insights and microscopic details. This holistic perspective lets you see how different parts of the network interact and depend on each other, facilitating a deeper understanding of the network's structure and flows.
- Intuitive hierarchical layout: Leveraging a unique circular treemap layout, the Map simplifies the representation of hierarchical relationships within the network formed by labels assigned to workloads. You can drill down from high-level label groupings (e.g., by environment or application) to specific IP addresses. This intuitive structure makes it easier for teams to identify and analyze the pathways of data flow and pinpoint critical nodes in the network.
- Dynamic interaction and exploration: With the Map, you can interact dynamically with the visualization, drilling down into specific areas for a closer look or zooming out for a broader perspective. Additionally, with time-specific data filtering and alternate map views, you get an enriching and adaptable visualization of traffic flows. Recognizing that different tasks require different views and filters, the tool incorporates advanced interactive features that allow users to tailor their analysis according to specific needs.
- Rich detail in a single glance: The Map's strength lies in its ability to show extensive network information compactly. Color-coded links indicate traffic types (allowed or blocked), and label-based group statuses (full, selective enforcement, or visibility-only) are clearly displayed. This enables you to quickly grasp the network's overall state and make informed decisions on policy settings with just a glance.
- Policy drafting efficiency: Enhance policy management with the ability to draft and adjust network policies directly within the visualization interface, streamlining the transition from analysis to action.
- Selective traffic highlighting and exploration: When a label-based group or workload is selected, the Map emphasizes its inbound and outbound connections by highlighting them and connected elements while subtly fading the rest. This allows for focused analysis, and by opening the side panel, you can delve into a summary and examine each connection in detail, ensuring a thorough understanding of network interactions so that can take appropriate containment actions.
4 Illumio Map capabilities to deep dive into your network communication
1. Groups and nodes: Get tailored insights for effective network management
Labels-driven communication insights: Choose one or multiple labels to clearly see the connections based on these groupings, offering tailored network insights.
- Unified view of flexible label hierarchy and connections: Displays both the hierarchical structure of labels and their interconnections within a single, cohesive visualization, enhancing overall comprehension and ease of analysis of your network.
- Label schema in action: See how your labels add order to the network. With this view, you can easily refine your labeling strategy for even greater clarity.
- Enhanced network customization: Allows for flexible analysis by enabling selection of specific label combinations, tailoring the network view to your needs.
- Insightful connection mapping: Reveals intricate communication patterns between chosen labels, providing a clear picture of network interactions and dependencies
Adaptive label-based group scaling by workload volume: Node sizes expand or contract to mirror the number of workloads within a label group, offering a visual shorthand for network capacity and importance.
- Prioritization of network exploration: Larger nodes indicate higher workload concentrations, guiding you to focus on the largest label-based workload grouping first.
- Effortless identification of critical groups: Identifies network hubs or critical nodes based on workload distribution, assisting in targeted network management strategies.
Enforcement status mapping: Use donut charts and rings to depict the enforcement states of label-based groups and individual workloads, employing a grayscale color scheme for clear differentiation.


- Immediate state recognition: Quickly identifies the security posture of label groups and workloads, from idle to full enforcement, enhancing situational awareness.
- Visual security overview: Provides a comprehensive visual summary of the network's security measures, symbolizing a protective shell that indicates the degree of protection surrounding the assets for an intuitive risk assessment.
Vulnerability score and exposure mapping: In this mode, the rings around the label groups or workloads change colors to represent the vulnerability score categories, from critical to none, using a distinct color-coded system.


- Risk-level assessment: Quickly ascertain the security risk of each node with color-coded rings indicating the severity of vulnerabilities, allowing for prioritized responses.
- Enhanced visual prioritization: Facilitates the allocation of resources by visually distinguishing between nodes, focusing attention on those with critical vulnerabilities for immediate action.
2. Interactive engagement with label-based groups and workloads
Get quick access to detailed node information and control options with intuitive click and hover actions.
- Hover for tooltips: Simply hover over a label group or workload to receive a tooltip with at-a-glance information, streamlining information retrieval without the need for clicks.
- Click for focus and clarity: Clicking on a label group or workload delivers a focused view on that point of interest, dimming unrelated elements and highlighting inbound and outbound traffic to and from the selected label group or workload for a focused view of relevant connections.
- Double click for depth: A double-click on any label group expands it to reveal the hierarchical structure or nested details within, offering insights into the organization and composition of the network elements.
- Post-selection details: After selecting a label group or workload, click to open a side panel to get extensive details about the point of interest and quick drafting of traffic control policies directly from the panel.
- Right-click for streamlining of querying and policy creation: Right-clicking on a label group or workload brings up a menu that allows you to instantly apply specific rules or add the label to source or destination filters.
3. Links: Understand the paths of communication
- Links categorization: Easily identify connections as allowed, blocked, or potentially blocked to streamline network traffic analysis and simplify policy evaluation.
- Instant data insights: By hovering over any link, access detailed contextual information that breaks down the nature and status of each connection, including the specific ports or services involved, enhancing your understanding and oversight of network interactions.
4. Using controls to navigate and customize your network view
Perspective-shifting layout options: Experiment with various layout options for adaptive visualization, gaining fresh perspectives on your network's structure. This flexibility allows for a better grasp of spatial and hierarchical relationships and can unveil previously unnoticed patterns, enhancing your network analysis and insight discovery.
Zoom functions to dive deep or get the big picture: Zoom in on specific label-based groups or connections with focused detail, or zoom out to see a broad overview that unveils overarching patterns. With a single click, use zoom to fit to tidily wrangle the entire network picture into your view.
A legend to help you keep track: Gain immediate clarity with a legend that categorizes node types by shapes and link types by colors, along with visual encodings for enforcement types and label group sizes. This ensures effortless navigation of your network map, allowing for swift decoding of visual cues for accurate and consistent analysis.


Network exploration: Enhance your network analysis with integrated "Collapse All Groups," "Undo," and "Redo" functionalities designed to streamline navigation and visualization in the Map. This cohesive feature set allows for quick decluttering of the visual space, along with flexible control over your exploration steps.
- Instant simplification with collapse all: Effortlessly tidy your view by collapsing all open label-based groups at once, decluttering your space and honing in on key network insights.
- Streamlined exploration with step forward and step backward: Easily navigate your analysis steps, moving back with "Step Backward" to undo changes or forward with "Step Forward" to redo actions, maintaining a smooth exploration of network layers.
Complete network view: Traffic and no-traffic members
See all network elements, regardless of traffic activity, with a single click to show every label group or workload.
- Unveil the entire network landscape: Get a complete overview by showing label-based groups or workloads with and without traffic, ensuring no part of the network is overlooked.
- Get simplified focus on active connections: Streamlines analysis by allowing users to filter out label-based groups or workloads without traffic, concentrating on areas with traffic for targeted insights and actions.
Filter your view for precision and focus: Tailor your visualization to isolate the most relevant data by applying filters based on node, connection type, transmission type, or traffic status. This targeted approach removes distractions from your view, allowing for deeper insights into specific network elements and a streamlined analysis to boost efficiency.
Policy and vulnerability mode: Toggle between policy and vulnerability modes to assess compliance and identify weaknesses, aligning your network management strategies with real-world requirements.
- Policy compliance: View your network through the lens of policy enforcement, ensuring that your setup meets all regulatory and internal standards.
- Vulnerability detection: Highlight potential security risks within your network, allowing for preemptive action to reduce risk exposure.
Illumio Map: See, segment, and secure your network better
Elevate your network insight with Illumio Map’s intuitive visualization. Move beyond the limitations of complex spreadsheets and allow the Map to enhance your network management by helping you:
- Comprehensively understand the enforcement status across your network
- Prioritize areas for security improvements with immediate visual cues
- Strategically plan your network security by easily identifying underutilized resources or potential compliance issues
Reach out to us now to discover how the Illumio Map can provide you with a full-scale, actionable view of your network's landscape.
.png)