Little-Known Features of Illumio Core: Virtual Services
In this ongoing series, Illumio security experts highlight the lesser known (but no less powerful) features of Illumio Core.
With the value of exfiltrated data dropping on the black market, hijacking critical resources and holding their data ransom has dramatically increased in value — and has become a very successful criminal business model. Today, disrupting an organization’s infrastructure is a very tempting target for bad actors.
Infrastructure resources can be hijacked and disrupted at the host and application layers, and both types of resources must be visualized and enforced independent of each other and on a granular scale.
In this blog post, learn how to leverage Illumio Core’s virtual services to secure your hosts and their applications and processes with and without an agent. This delivers an end-to-end Zero Trust architecture with no blind spots.
Illumio Core’s agentless approach to workload security
Illumio Core manages workloads directly on the OS by deploying the Illumio VEN agent which then pairs with the Illumio PCE. This enables Illumio to visualize and enforce application-centric traffic using firewall capabilities which are native to each OS, independent of traditional security solutions. Workload-centric segmentation requires a solution that’s agnostic to the underlying hosting environment.
While this approach of pushing the workload security solution directly onto the workload is the most ideal, there are other kinds of workloads that need to be included in workload visibility and enforcement architectures but don’t allow third-party agents to be deployed, such as load balancers, IoT, and OT devices.
Agentless security solutions are often associated with public cloud platforms which Illumio enables with Illumio CloudSecure. In an on-premises environment, there are various private cloud solutions which have different security options, but most of these solutions are dependent on hypervisors or virtual, overlay-network architectures. Creating segments in a hypervisor or overlay-network environment is still a network-centric solution, whereas workload-centric segmentation requires a solution which is agnostic to the underlying hosting environment. How can Illumio enable this without the VEN agent?
3 ways Illumio Core secures environments without an agent
Illumio Core extends its visibility and enforcement solution beyond managed workloads with these agentless entities:
- Unmanaged workloads
- Virtual servers
- Virtual services
Unmanaged workloads
Illumio can identify unmanaged workloads without a VEN agent by using its hostname and IP address. Illumio then assigns labels to that workload which enables Illumio to visualize and enforce access to it from all other managed workloads.
Illumio is not receiving telemetry from that unmanaged workload since there is no VEN agent deployed on it. Instead, Illumio can see which managed workloads it is communicating with, allowing Illumio to fully include these unmanaged, agentless workloads in its Illumination Map and policy model.
Illumio manages both managed and unmanaged workloads the same:

Virtual servers
A virtual server is used to enforce traffic through a load balancer. Illumio defines each virtual server by the VIP being exposed on the F5 or AVI load balancer. Illumio also creates labels for pool members deployed behind the load balancer associated with that VIP.
Illumio’s Network Enforcement Node (NEN) module helps to read and write security policy directly onto the load balancer using an API-driven workflow. This enables Illumio to visualize and enforce traffic to and from virtual servers through a load balancer without relying on deploying a VEN agent.

Caption: Illumio enforces virtual services by configuring load balancer and managing pools.
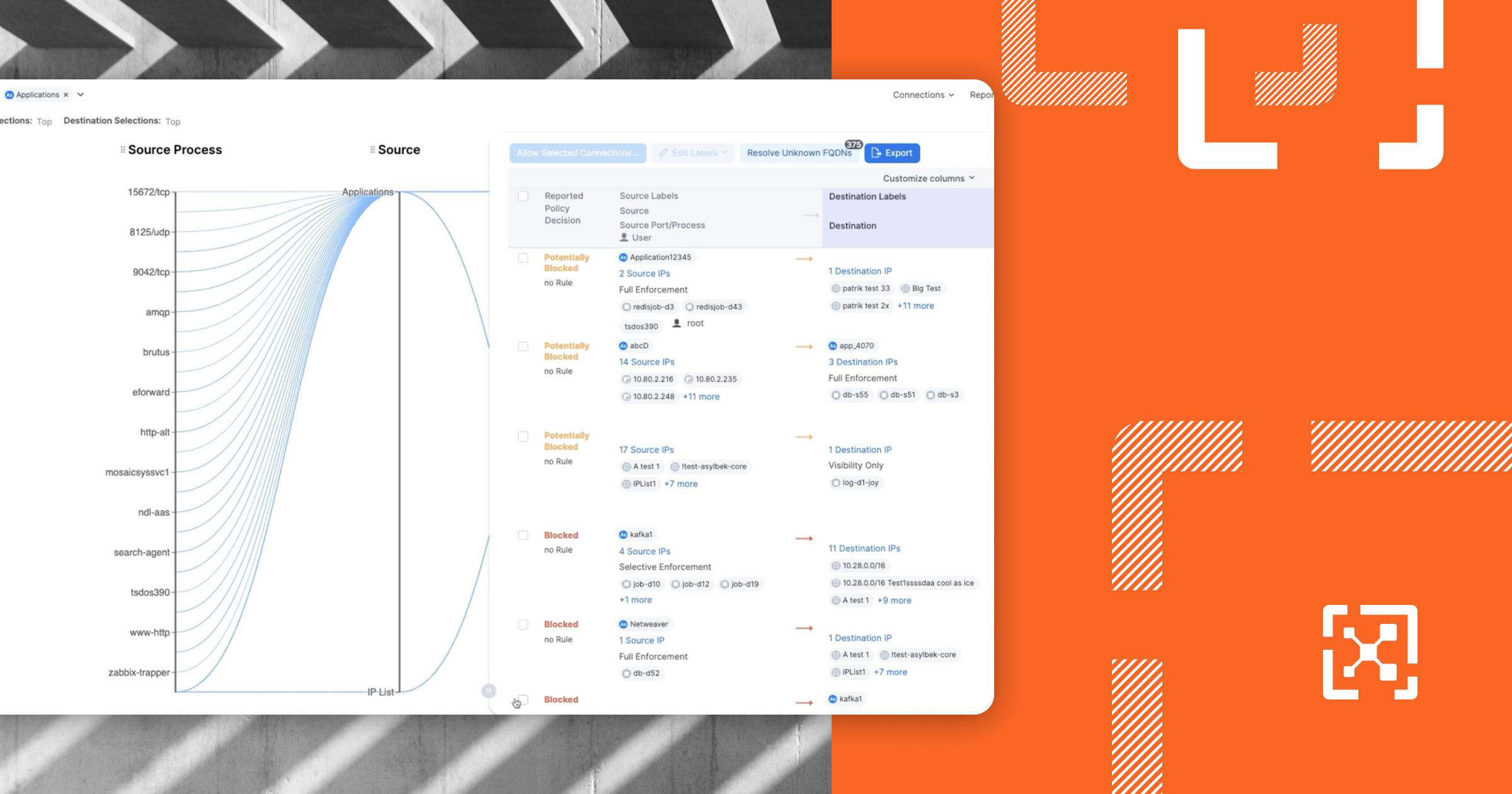
Virtual services
A virtual service is used to label and define policy to one or more specific processes or applications residing on the same host, with each virtual service being independent of the underlying host’s labels and policy. For example, if two applications are deployed on a single host, Illumio will create two different virtual services, each enforcing distinct policy from each other and the underlying host.
When Illumio uses a virtual service to define a specific process or application as a workload, independent of the host it is deployed on, it will “bind” that virtual service to the ports used by that process. A virtual service can map to either a single process or a collection of specific TCP ports on a host.
Illumio can assign different labels to different applications on one host. For example, if one host has deployed both a database process and a postgres instance on port 5678, Illumio can create two different virtual services and bind each one to the relevant ports used by each process. Then, Illumio will label them using the same multi-dimensional labeling as used with managed workloads.
Different policies can then be defined against each application label, distinct from the labels and policy defined to the underlying host:

If the service or application moves from one host to another, which can happen in private cloud platforms, the policy defined for that application in Illumio doesn’t need to change. Illumio will dynamically re-calculate the rules on the updated workload, such as the new IP address on the host the application has migrated to, in order to allow this virtual service to bring its application-centric policy with it during the migration.
This enables applications to dynamically migrate across different VMs, for example. Application policy will remain stable, not requiring security change-control processes to follow along with application migrations, regardless of how dynamically applications migrate between hosts.
Virtual services on managed and unmanaged workloads
Virtual services are commonly used on managed workloads, but they can also be used on unmanaged workloads. If an unmanaged workload has multiple processes or applications deployed on it, Illumio can associate each of them with a different virtual service and will label and enforce each one distinct from the other.
This allows security teams to define very granular policy specific to processes and applications across different types of workloads. As a result, visualization and policy aren't only limited to an OS/host workload model.
This is where Illumio’s high scale of supported workloads becomes important — following this model at scale can create an explosion of entities to visualize and enforce which Illumio can easily manage.
Secure against threats targeting hosts and applications
Illumio enables the enforcement of application and host network dependencies, delivering clear visibility of who is talking to what and the ability to lock down lateral movement between resources without complexity. Illumio secures your hosts and their applications and processes with and without an agent. This delivers an end-to-end Zero Trust architecture with no blind spots.
To learn more about Illumio ZTS, contact us today for a free consultation and demo.
.png)




.webp)