5 Use Cases for Deploying Microsegmentation in Public Cloud Environments
Public clouds have created on-demand, elastic environments that can be easily scaled to meet changing business needs. Applications have transitioned from static monolithic code blocks to microservices that can be deployed across different public cloud providers, in different regions and with different operating systems relying on automation at scale, challenging existing security practices to reduce risk exposure and prevent the lateral movement of bad actors.
As the scale and scope of cyberattacks are constantly evolving, more and more organizations are implementing microsegmentation as an essential part of a defense-in-depth strategy. According to a recent survey of over 300 IT professionals, 45 percent currently have a segmentation project or are planning one.
All of the major public cloud providers have their own cloud security solutions, enabling basic levels of policy enforcement as well. As your cloud compute scales, you may request your public cloud provider for an increase in security groups, adding to operational complexity and increasing the risk imposed by rule bloat. In addition, these cloud security tools are siloed in the overall architecture. Each security solution does not play well in the sandbox with others and correlating a security breach between all of them is a cumbersome task that introduces large delays in resolution. For more information on this challenge, check out this post from my colleague Christer.
Security controls have evolved and now provide the ability to see the cloud compute instance in the context of the application and business process, allowing users to better understand risk and build policy by leveraging the native, built-in stateful firewall available in each compute instance.
The first step in the life of a packet, at its birth, is attaching policy. By the time a packet reaches the network forwarding plane, security has already been applied. This approach brings cloud security very close to where the action is and the controls are – independent of the network. Network and security are decoupled to get the best of both worlds.
In this post, I will answer five public cloud security questions that commonly arise when organizations are considering microsegmentation.
1. Can cloud security be enforced during the full lifecycle of a workload?
Absolutely. Cloud security controls are automatically enforced on a workload during the entire lifecycle, from creation to termination.
By integrating orchestration tools (like Ansible, Chef, Puppet) with Illumio’s Application Program Interface (API), workloads are paired with Illumio’s Policy Compute Engine (PCE). During pairing, tags associated with a workload are mapped to labels on the PCE and workload inherits the right set of security policies created using labels on the PCE. If a workload is mislabeled, changing labels automatically trigger appropriate policy changes. If a workload IP address changes, the PCE picks up the new IP address automatically. Since security policies are decoupled from the network, no further changes are needed. When a workload is terminated, PCE automatically triggers appropriate policy changes.
By decoupling the network from segmentation, policy changes are automatically triggered, enforcing the right set of security controls on a workload during its full lifecycle. Security has always been important, but as organizations become more dependent upon software to drive their business, it’s becoming increasingly critical to get security right in order to minimize business risk.
2. Is real-time application visibility in the public cloud possible?
You bet. Applications don’t sit on an island. They talk to each other, and that’s how business processes work.
Real-time visibility into application dependencies helps us understand application behavior that drives accurate segmentation policies. Application-centered visibility is the vital foundation for good security as microservices are deployed across different public cloud providers and different regions.
Illumio Core (formerly known as Illumio ASP) provides a real-time application dependency map called Illumination that visualizes communications between workloads and applications. Lines on the map represent detected traffic flows between workloads whether in the cloud or on-prem. Illumio colors the lines red and green to indicate if the connection is allowed or blocked by the microsegmentation policy.
The screenshot below shows the application dependency map of the AssetManagement application in the Production environment. Here, lines on the map represent detected traffic flows between workloads. Illumio colors the lines red and green to indicate if the connection is allowed or blocked by microsegmentation policy. A green line means a policy has been written to allow the connection. A red line means no policy exists and the connection will be blocked when moving into enforcement mode. Red and green lines make it incredibly easy to visualize your segmentation policy and policy violations. Suffering from color blindness? Illumio ASP provides users with a color vision deficiency option.
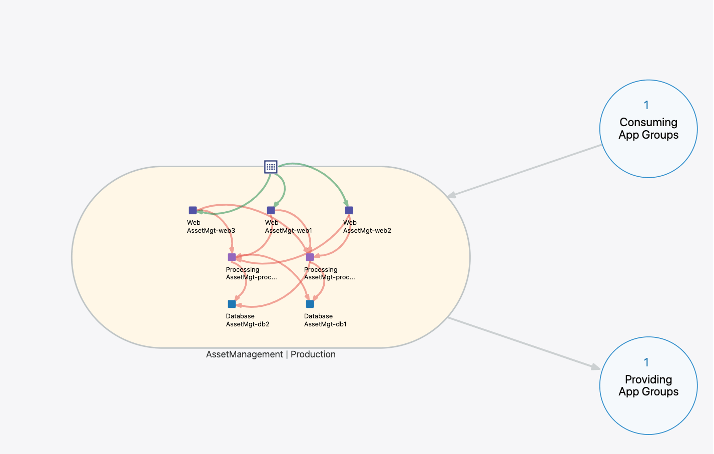
When Illumio’s agent, the Virtual Enforcement Node (VEN), is installed on a workload and paired to the PCE, visibility and enforcement is available. Pairing a VEN to a PCE is automated using tools like Ansible and Terraform.
When the VEN is not installed on a workload, using solutions shared by Illumio Labs, customers can visualize the application dependency of workloads running on Microsoft Azure and Amazon AWS on the PCE.
3. Can I validate my cloud security controls across multi-cloud?
You sure can, without breaking your application. One of the greatest challenges in a multi-cloud deployment is the lack of consistent security as each provider offers a set of controls that may be conceptually similar but differ significantly in implementation. Illumio abstracts the underlying cloud from the application without relying on the knowledge or control of the infrastructure to develop security policies.
Illumio offers two solutions to validate your security controls:
- Switch Illumination to Draft View to visualize draft policy to see what will happen when you provision changes.
- Switch workloads policy state to Test to apply all rules in your ruleset and visualize all the traffic that would be blocked when you placed the workloads in the enforced policy state. No traffic is blocked in Test state.
4. Is microsegmentation possible on Platform-as-a-Service (PaaS)?
Yes. Illumio Labs has shared solutions that offer visibility and enforcement for Microsoft Azure SQL database and Amazon AWS RDS.
Illumio Labs outlines three steps for visibility and enforcement. Here, the server-level firewall guarding the Azure SQL database server is programmed using the security policies defined on the PCE.
Illumio Labs also outlines six steps for visibility and enforcement. S3 buckets are used to store flow logs that trigger a Lambda function that reprograms the VPC security groups based on security policies defined on the PCE.
5. Can Illumio help with a major cloud security breach?
Without a doubt. Getting security wrong can mean data loss, data breach, sensitive data exposure, impact to revenue, lasting effect on brand, and even penalties tied to compliance. Security has not kept up with the evolution we have seen across infrastructure and applications. You need to approach security in a new way and think differently about application environments and how you protect them.
One of the biggest challenges with a security breach is lateral movement. Illumio has been designed to stop lateral movement and reduce the blast radius. By design, Illumio follows an “allowlist” model, so when a workload gets compromised, security policies on all other workloads are automatically updated to block traffic from the compromised workload.
Center for Internet Security (CIS) Security Controls initiatives are widely adopted and have been around for more than 10 years. The controls are derived from the most common attack patterns highlighted in the leading threat reports and vetted across a very broad community of government and industry practitioners. They reflect the combined knowledge of commercial and government forensic and incident response experts. Illumio’s capabilities help you directly meet or support CIS basic, foundational and organizational controls.
Quick recap
Microsegmentation is a very effective approach to prevent unauthorized lateral movement within your organization, and it no accident that it has become a key tenet if a Zero Trust framework.
As your organization scales to meet business needs, creating consistent security controls that work across public cloud providers becomes critical in reducing your risk exposure and reducing the complexity. Ready to take the first step on your microsegmentation journey? Sign up for a free 30-day trial.
.png)


