Connected Medical Devices: Healthcare’s Top Cybersecurity Vulnerability

For the healthcare industry, the integration of connected Internet of Things (IoT) medical devices has revolutionized patient care, diagnostics, and treatment methodologies. But this fast-paced adoption of IoT devices has brought its own set of challenges, particularly around cybersecurity.
As the healthcare sector becomes increasingly reliant on these devices, the vulnerability of medical systems to cyber threats grows, posing risks to critical patient care, sensitive data, and overall healthcare operations.
In this blog post, we will delve into the cyber threats targeting medical devices, explore why they're a cybersecurity concern, and why it’s essential for healthcare organizations to adopt Zero Trust Segmentation as they build cyber resilience.
Unprotected connected medical devices are a boon for bad actors
In 2023 alone, there were 541 breaches against healthcare organizations — and that only includes the organizations will 500 employees or more who are required by the U.S. Department of Health and Human Services (DHHS). These breaches accounted for over 100 million individuals’ private health information being leaked, and many hospitals were forced to halt operations as a result of attacks.
As a result of the ever-increasing risks associated with healthcare security, a recent report from the U.S. Government Accountability Office (GAO) highlights a growing concern for the extensive security vulnerabilities in today’s IoT medical devices.
According to the GAO’s report, “Cyber threats that target medical devices could delay critical patient care, reveal sensitive patient data, shut down health care operations, and necessitate costly recovery efforts.”
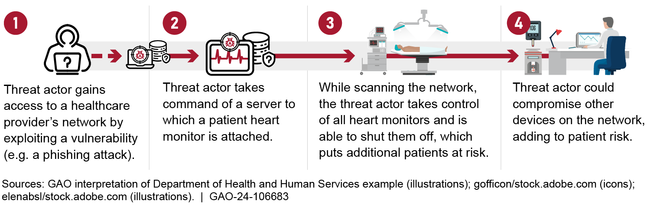
Global governments are starting to take the severity of cyber threats targeting medical devices within healthcare organizations seriously. In fact, starting just last March, a new law requires U.S. medical device manufacturers to submit plans to address cybersecurity vulnerabilities for any new medical devices to the U.S. Food and Drug Administration (FDA) in the hopes of targeting cybersecurity risks at the source. But this doesn’t address the millions of legacy medical devices that are currently in use at healthcare organizations worldwide.
If healthcare organizations don’t start to proactively secure against these threats, the number of cybersecurity incidents linked back to connected medical devices will only continue to grow.
4 reasons why connected medical devices are a cybersecurity threat
The increasing integration of connected medical devices in healthcare systems presents a significant cybersecurity threat, stemming from their susceptibility to exploitation by malicious actors. Medical IoT devices pose such a significant threat because of these four reasons:
- Proliferation and complexity: The widespread adoption of connected medical devices has increased the attack surface for cybercriminals. Each device connected to a hospital’s network represents a potential entry point for malicious actors. The complexity of these devices, often running on various operating systems, firmware versions, and some no longer receiving software updates, further complicates security measures.
- Inadequate security measures: Many IoT medical devices are designed with a primary focus on functionality and patient care, often overlooking robust cybersecurity features. Outdated software, weak or default passwords, and lack of regular security updates make these devices vulnerable to exploitation.
- Interconnected ecosystems: The interconnected nature of healthcare systems causes a ripple effect when cyberattacks happen. A breach in one device can potentially compromise the entire network, leading to a domino effect that affects critical infrastructure and patient care delivery. This allows bad actors to move laterally throughout a network, gaining access to more data, systems, and resources as they spread.
- Data sensitivity: Medical devices store and transmit sensitive patient data. In the wrong hands, this information can be exploited for identity theft, financial fraud, or other malicious activities — making them an enticing target for threat actors. Because protecting patient privacy is a paramount concern in the healthcare sector, the security of IoT devices is a critical imperative.
Securing connected medical devices with Zero Trust Segmentation
To fortify healthcare organizations against the rising tide of IoT vulnerabilities, it's time to adopt comprehensive cybersecurity measures is imperative. Cyber resilience is business-critical and ensures organizations can maintain operations during an attack, whether it’s from a medical device or elsewhere.
The best way to achieve cyber resilience is through Zero Trust, a globally validated strategy based on the mantra of "never trust, always verify." Zero Trust preaches that breaches are inevitable. Instead of going in circles (and likely failing) to prevent or detect the next breach, Zero Trust encourages organizations to accept that breaches are unavoidable, put proactive measures in place, and have a plan ready to react when a breach happens.
Traditional prevention and detection methods are important, but they shouldn’t be your last line of defense in today’s threat landscape.
Zero Trust Segmentation (ZTS) is a key pillar of Zero Trust. You cannot achieve Zero Trust without it. ZTS enables a consistent approach to microsegmention across the hybrid attack surface, enabling organizations to see and reduce risk across the cloud, endpoints, and data centers. ZTS is easy and simple in comparison to attempting segmentation with static, legacy firewalls.
Learn the nine reasons why healthcare providers should implement ZTS.
Why Illumio ZTS is essential to healthcare cybersecurity
The Illumio ZTS Platform helps healthcare organizations build a Zero Trust architecture that protects connected medical devices from allowing breaches to spread throughout the network.
Here's how Illumio supports healthcare organizations in building cyber resilience:
- See and understand security risks: Illumio ZTS provides a clear perspective on security risks across all assets in all environments. See how systems and applications are connecting and discover where open ports are creating unnecessary risk.
- Test and implement granular segmentation policies: By providing insight into dependencies, Illumio ZTS allows teams to pinpoint what policies need to be implemented and where. Policies can be tested before implementation, ensuring that policies don’t impact operations. And as your IT, OT, and IoT environments evolve, scale visibility and security policy dynamically to ensure continuous security.
- Stop breaches and ransomware: Illumio ZTS helps your organizations become attack-tolerant by proactively isolating high-value assets or reactively containing breaches and ransomware in compromised systems during an active attack. Even if a breach does occur, Illumio ZTS stops and contains the breach, lessening its impact. Read more about why healthcare must take a breach containment approach to cybersecurity.
- Build Zero Trust: Illumio ZTS helps extend Zero Trust principles to medical devices, ensuring that each device is subject to Zero Trust security policies and reducing the risk of exploitation.
Contact us today to learn more about implementing Zero Trust Segmentation at your healthcare organization.
.png)





