Understanding EU Compliance Mandates: Operational Technology & Critical Systems
In my first post on understanding EU compliance mandates, I discussed the compliance landscape as a whole – and how different industry types and areas each have their own governing mandates or guidance on cybersecurity. Today, I will concentrate on regulations and security controls specific to a really interesting sector – Critical Systems and Operational Technology.
For clarity, let’s start by defining some commonly used acronyms:
- OT – Operational Technology (in contrast to IT, Information Technology)
- IT – Information Technology, the typical computer systems, and networks we are all familiar with
- ICS – Industrial Control Systems
- SCADA – Supervisory Control and Data Acquisition
It’s important to understand the core differences between OT and IT security before we dive into the compliance that exists in the industry, as the fundamental requirements are quite different. For those working in the field or with experience there, we have probably all seen variations on the below diagram:
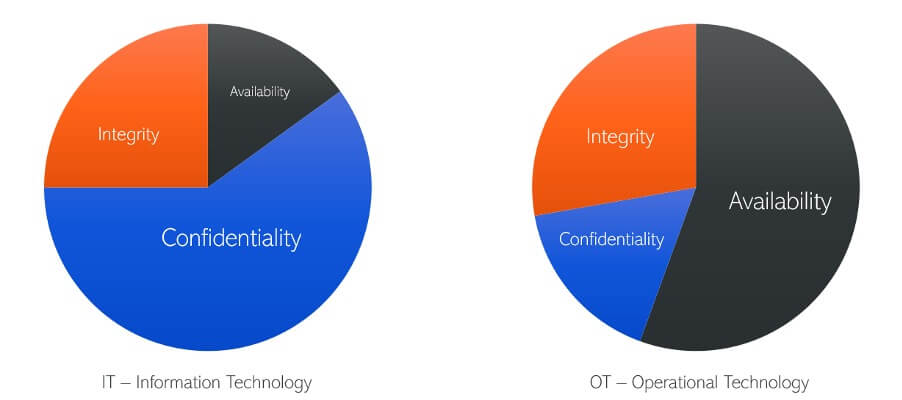
In an OT environment, the failure of a system, or inconsistency in data, can result in real, physical impact on the world. For example, the breakdown of a safety system or the halting of a production line can lead to more physically harmful results than similar failures in IT. This, of course, means that the systems themselves (including software) are built with resilience and redundancy in mind – and the relevant compliance mandates take this into account.
With that said, let’s look at some of the compliance types that might apply, and then discuss how microsegmentation and control play into them.
The primary mandates that we see in the EU are:
- The Network and Information Security Directive, or NIS-D. This is an EU-wide set of cyber controls, created centrally with input from all states, but with guidance and oversight provided locally on a country-by-country basis.
- LPM. Similar, but more locally focused, LPM is a French, OT-specific mandate or “Critical Information Infrastructure Protection law”. This was partly the basis for the NIS-D and contains similar concepts of an Operator of Essential service. The difference with LPM is that it is a mandate, and therefore systems deemed “in scope” for the mandate must adhere to the LPM security guidance. In France, this law is governed by ANSSI (Agence nationale de la sécurité des systèmes d'information – the National Cybersecurity Agency of France), which also oversees the NIS-D in region.
How microsegmentation applies to OT system compliance
Both the NIS-D and LPM explicitly mention some key areas.
For LPM, the 20 categories are:
- Information assurance policies
- Security accreditation
- Network mapping
- Security maintenance
- Logging
- Logs correlation and analysis
- Detection
- Security incidents handling
- Security alerts handling
- Crisis management
- Identification
- Authentication
- Access control and privileges management
- Administration access control
- Administration Systems
- Segregation in systems and networks
- Traffic monitoring and filtering
- Remote access
- Systems set up
- Indicators
For the NIS-D, local member-states publish specific guidance. In the UK, for example, this is handled by the NCSC (National Cyber Security Centre) – with their Cyber Assessment Framework (CAF). For more information on this, check out this webinar, and read this paper.
NIS-D has a similar number of specific areas pertaining to micro-segmentation, and network flow visibility:
- Risk Management Process: Your organizational process ensures that security risks to networks and information systems relevant to essential services are identified, analyzed, prioritized, and managed.
- Data Security: You maintain a current understanding of the data links used to transmit data that is important to your essential service
- Data in Transit: You have identified and suitably protected all the data links that carry data important to the delivery of the essential service.
- Secure By Design: Your networks and information systems are segregated into appropriate security zones, e.g. operational systems for the essential service are segregated in a highly trusted, more secure zone.
- Design for Resilience: Your essential service’s operational systems are segregated from other business and external systems by appropriate technical and physical means, e.g. separate network and system infrastructure with independent user administration. Internet services are not accessible from operational systems.
- Vulnerability Management: You maintain a current understanding of the exposure of your essential service to publicly-known vulnerabilities.
- Security Monitoring: As well as your network boundary, your monitoring coverage includes internal and host-based monitoring.
We can see that for both LPM and NIS-D, Illumio can help.
How to reach regulatory compliance with microsegmentation
Having understood the mandates, how can you use micro-segmentation in the field to meet these (and other) controls? Here are a few examples:
- Application Dependency Mapping of both the OT and IT environments, incorporating the IT/OT boundary critically. This can be accomplished through data collection at the workload level, or, more likely, flow collection from network infrastructure on the OT side to provide a rich, high-fidelity map.
- Environmental Segmentation of the OT and IT environments, while maintaining critical monitoring, logging, and control channels. Zero Trust as a network security concept has never been more applicable than in this scenario.
- Alerting against new flows/connections into the OT environment from IT, or from within the OT environment itself. The initiation of new connections is important to monitor for two reasons: first, OT tends to be more static an environment than the chattier and more dynamic IT side. Secondly, whether deliberate (targeted malicious activity to gain access to the ICS/SCADA systems), or accidental (a number of high-profile OT compromises have actually been closer to collateral damage by commodity malware managing to access the critical system side), unauthorized, successful access into the critical side of the network is fundamentally what micro-segmentation solutions prevents.
- Vulnerability assessment against the OT infrastructure. As we can see from the NIS-D, vulnerability management is key. While Illumio, for example, does not scan for vulnerabilities, it maps them to the grouping and application flows observed, showing critical pathways and helping prioritize microsegmentation policy and patching.
The ever-evolving landscape
As the agility and monitoring of critical systems shifts, they are increasingly connected to less-critical networks and applications, and sometimes even the internet. A quick OT-protocol search on shodan.io can be eye-opening! At the same time, scrutiny on the connectivity and security of these systems is increasing, as it should. This juxtaposition means that visibility becomes incredibly important, even before clearly defining and maintaining microsegmentation policies.
Mentioned in my first post, the various mandates provide a spectrum of enforcement – from strict, mandated laws (in the case of LPM), to more of a guiding position at present, in the case of the NIS-D. Some of the difference here comes down to maturity and length of existence.
It’s in the broader, less well-defined cases that interpretation of the guidance becomes important, and much like GDPR, the NIS-D takes into account intent as well as technical implementation and specific configuration.
In either case, I think it’s clear that the visibility and segmentation of these increasingly-connected critical systems is the fundamental control by which we can secure them.
Stay tuned for my next post, where I will explore financial industry mandates in the EU.
And for more on Illumio ASP, check our solution architecture page.
.png)


%20(4).png)