Illumio + Appgate: Securing Interior and Perimeter Network Traffic
If anyone claimed a few years ago that in the near future people would be accessing sensitive, classified, or legally risky information from home offices and coffee shops, they would have said it’s impossible.
Accessing sensitive information has always required doing so from within tightly controlled environments. But the pandemic has changed this, making it an essential requirement for many organizations to have access to this information from far outside of their traditional, tightly controlled environments.
This reality has exposed the need for layers of defense that protect both north-south and east-west traffic across interior and perimeter networks.
That’s why Illumio is excited to announce our partnership with Appgate. The combination of ZTNA from Appgate and the Illumio Zero Trust Segmentation Platform offers customers full-compass security to speed their Zero Trust journey and immediately improve their Zero Trust security posture.
Where to start with Zero Trust? The 5-pillar model
Zero Trust is complex and can be challenging to implement.
We recommend a five-pillar model when building your Zero Trust strategy: data, users, devices, workloads, and networks
In this security model, you can apply the principle of least privilege to each pillar and only authorize data sharing between them when it’s absolutely necessary.
To start building Zero Trust, choose which of the five pillars to address first. To make this decision, you must identify and rank your organization’s most critical assets — other than data — that you need to protect.
For most organizations, this includes critical workloads like database servers, application servers, and web servers.
3 Zero Trust must-haves to protect critical workloads
To protect your critical workloads – and build your organization’s Zero Trust security posture – use these three tactics.
1. Apply Enhanced Identity Governance (EIG): Many organizations began their Zero Trust journey by deploying EIG. This is a necessary and smart first step. But it only makes up one of the three controls needed for a strong Zero Trust architecture.
2. Build Zero Trust network access (ZTNA) to workloads via the perimeter network (north-south traffic): Most organizations have implemented security at their network’s perimeter. However, the pandemic — and the way it rapidly accelerated the trend towards a hybrid workforce — makes perimeter security an even bigger priority.
3. Apply Zero Trust Segmentation to workloads in the interior network (east-west traffic): While north-south security is as old as cybersecurity itself, east-west security is relatively new. Most organizations are less aware of it and don’t understand it very well. Yet many breaches over the last few years have made it clear that there’s more to interior security than authenticating users. East-west traffic is the main way ransomware and other cyberattacks spread on a network.
While many organizations have put EIG in place, there’s still more needed to complete a Zero Trust program – and adapt to the security needs of today’s hybrid IT environments.
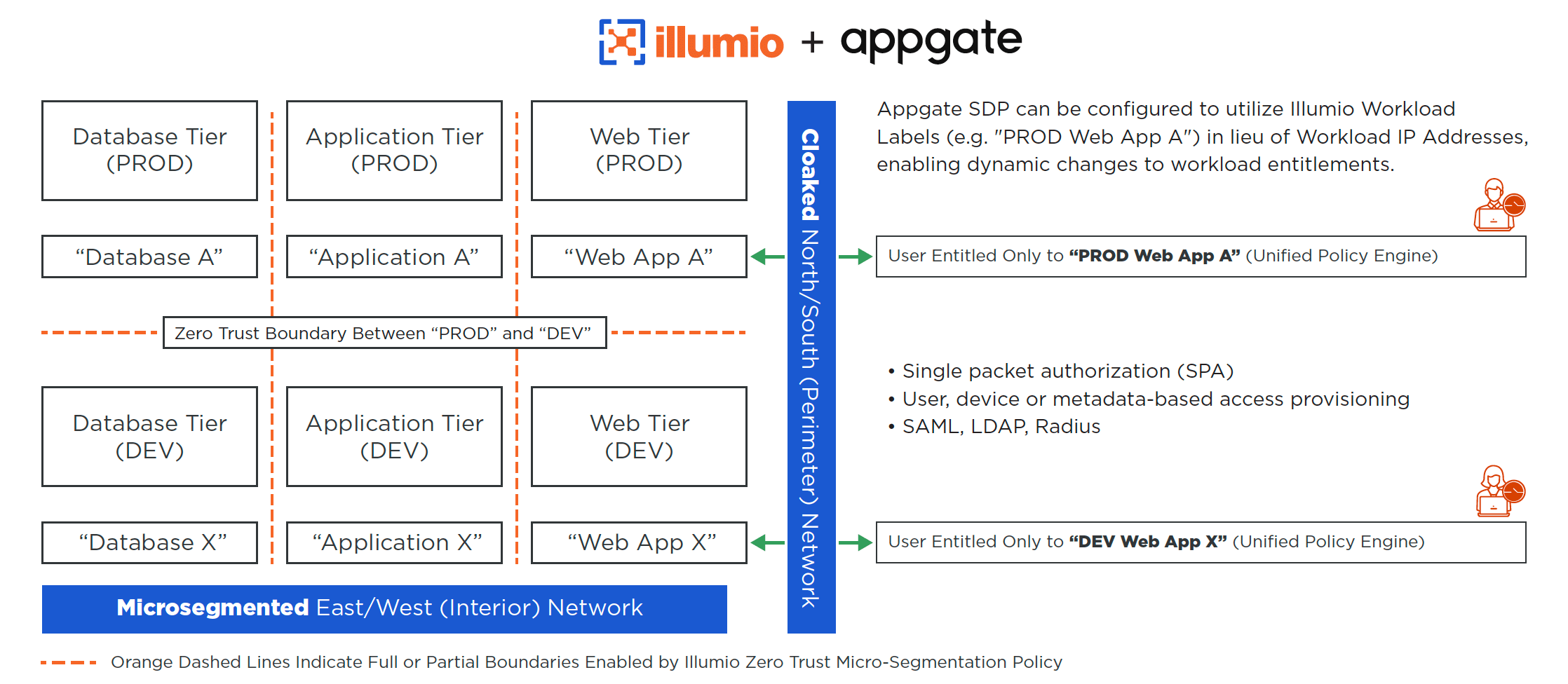
Illumio + Appgate: Zero Trust for Perimeter and Interior Network Traffic
On average, every 1 MB of north-south traffic entering a data center or cloud will generate 20 MB of associated traffic east-west, workload-to-workload.
This means that placing any kind of security solution only at the north-south perimeter, like firewalls, will make you blind to the vast majority of all network traffic.
Without a solution to secure east-west traffic in addition to north-south traffic, you will have an enormous blind spot in your security architecture. Blind spots are tempting targets for any bad actors to exploit.
With Illumio and Appgate, you can deploy a truly end-to-end Zero Trust architecture and protect your organization from threats to both the exterior and interior networks.
The two platforms uniquely offer mature, highly evolved APIs that let Illumio Core pass metadata to Appgate. This makes it possible for the two security platforms to adhere to a strict Zero Trust approach that creates dynamic, fine-grained, least-privileged access control for all traffic.
Illumio and Appgate are leading the way in helping organizations implement effective and efficient Zero Trust security protection. Illumio and Appgate were ranked as Leaders in the Forrester Wave™: Zero Trust eXtended Ecosystem Platform Providers.
If you’re struggling with what to do next after deploying EIG, remember that with just Illumio and Appgate, you can quickly build Zero Trust security to protect both perimeter and interior traffic across your hybrid computing environments.
That’s cybersecurity peace of mind.
Register for the joint webinar on November 16.
Get the three-step, best practice approach to implementing Zero Trust security with Illumio Core and Appgate SDP in our solution guide.
.png)


