A Deeper Look at Illumio’s Integration with Palo Alto Networks
Microsegmentation and firewalls help enterprises to reduce their attack surface and limit exposure to ransomware, malware and other threats that move laterally or quickly propagate across East-West traffic flows inside data center and cloud environments. But as we know, today’s enterprises are highly distributed in nature, with users, devices, and workloads increasingly everywhere. To address this, enterprises should look to implement security at both the network as well as the workload.
Workloads are ephemeral and most workloads are assigned a variety of different IP addresses as they are spun up and spun down between network fabrics or have their IP addresses changed for a variety of reasons by a controller that dynamically allocates compute resources. This is especially true of modern microservices architectures hosted in public cloud fabrics, where workloads are constantly dying, resurrecting, and moving around the network dynamically. Using an IP address to statically identify a workload, in any form, is a relic of the past. Therefore, it’s important to map real-time context in order to enforce effective workload security throughout its lifecycle.
Due to their dynamic nature, it’s often difficult for organizations to map and enforce microsegmentation policies to workloads everywhere they run. While application workloads communicate with each other primarily through East-West traffic flows, traffic in and out of the data center or cloud environments are secured across North-South traffic at the perimeter. To accomplish effective microsegmentation, you need to implement real-time policy updates to workloads wherever they move: across the network fabric to Next-Generation Firewalls (NGFWs), as well as across the host infrastructure where they can be enforced by agent-based solutions that operate at the workload level. Mapping security policies for dynamic workloads across East-West and North-South is complex and difficult to manage at scale. Inconsistencies can occur if security policy changes are managed in silos across the NGFW and agent-based microsegmentation tools.
Automate dynamic security using metadata
Illumio Core uses metadata in the form of labels to identify workloads, instead of relying on network addressing. The administrator can assign different labels to different workloads, and these labels can then be used to define policy. Using Virtual Enforcement Node (VEN) agents deployed on each workload, Illumio Core keeps track of the changing IP addresses of that workload behind the scenes. Even if a workload changes its IP address ten times across its lifecycle, the label remains consistent. The result is that policy is defined independently of how the underlying network is designed. Packet forwarding is still performed via IP lookups, but this happens behind the scenes. Labels become the construct used to identify different workloads, and since policy is written using these labels, the result is labels that read more like a human sentence, rather than a list of IP’s and ports.
Palo Alto Networks has a similar philosophy around using metadata in the form of tags to identify workloads inside of Dynamic Address Groups (DAG)s in Panorama or Palo Alto Networks NGFWs such as PA-7000 Series, PA-5200 Series, PA-3200 Series, and VM-Series virtual Next-Generation Firewall. The firewall can create an Address Group, and define it as either Static or Dynamic, and these can then be used to define policy. The result is a firewall rule that also reads more like a human sentence, defining who can do what to whom, using the DAG names rather than specific IP addresses. A DAG is sort of like an “empty bucket” with no IP addresses assigned to it. If it is a Dynamic Address Group, this empty bucket is populated with IP addresses from some external entity.
By bringing Illumio Core for agent-based microsegmentation, users can get real-time context of their workloads pushed directly into DAGs inside Panorama or in Palo Alto Networks NGFWs. This solution helps Palo Alto Networks users to ensure that their DAG-based policies are fully up to date with the latest workload policy changes. As Illumio tracks the changing IP addresses for all workloads, it can push these labeled workload mappings out to Palo Alto Networks. So, if Illumio Core maps ten workloads as “App” workloads, and the Palo Alto Networks firewall has created a DAG also called “App” and uses that DAG in a policy set, the firewall will have that DAG populated by Illumio. As a labeled workload is assigned an IP address, or if it is released or changed, all of these changes can be pushed out to the Palo Alto Networks firewall.
The real benefit here is that administrators can configure the firewall once, and then won’t have to touch it every time there is an IP address change. The firewall remains quiet, even if the scale of workloads increases. If a DAG for “App” workloads contains 10 IP addresses, or 100 IP addresses, no change control process is required to modify the firewall as the deployment scale increases. Illumio simply updates the firewall as needed.
As part of the integration, labels and IPs for workloads in Illumio Core are dynamically mapped into Palo Alto Networks DAGs. The result? Users can eliminate the manual effort to manage static security policy changes for dynamic workloads. You can benefit from automation and eliminate the human element, which can lead to misconfigurations and human error when maintaining real-time workload security updates.
Together with Illumio and Palo Alto Networks, you don’t need to sacrifice security as your network scales or evolves. You benefit by automatically updating the DAGs in Panorama and your NGFWs with real-time workload context that can help to save you time, effort, and the headache associated with orchestrating effective microsegmentation policy for your changing application workloads.
The API workflow between Illumio and Palo Alto Networks
In Illumio Core, workloads are assigned the metadata labels Role, Application, Environment, and Location to provide additional context. For example, web-tier workloads part of an ordering application deployed for development in a New York data center would be assigned the Role label Web, Application label Ordering, Environment label Development, and Location label NY_DC.
In Palo Alto Networks Panorama, policy can be created using Dynamic Address Groups (DAG) defined by matching criteria using label(s). Membership change(s) to DAG are automatic, eliminating the need for change management and approvals!
The API-driven integration tool “Illumio-Palo Alto Networks DAG Updater” registers and unregisters workloads dynamically during the entire lifecycle, including IP address changes (example, VM migrations in a Data Center, or ENI changes on a host in Cloud) and metadata changes (example, a workload re-labeled as Quarantine). As workloads are dynamically registered and unregistered, membership to the DAG changes and the right set of policies are automatically applied to workloads.
The ability to update DAG membership automatically during the entire lifecycle of a workload allows for application-centered policies that can span across multiple data centers and easily scale across multi-tiered architectures.
Here is a simple example of environmental segmentation between workloads in Development and Production.
Setup
Workloads are paired to Illumio PCE and assigned metadata Role, Application, Environment and Location using labels:
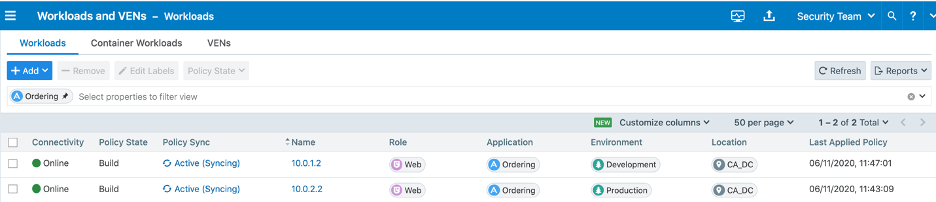
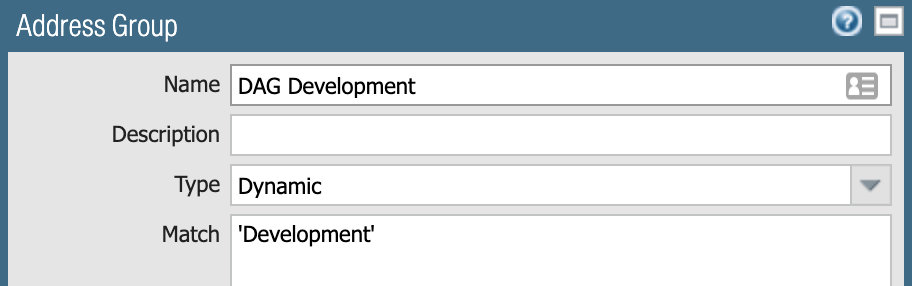
DAG is created using matching criteria Development – all development workloads:
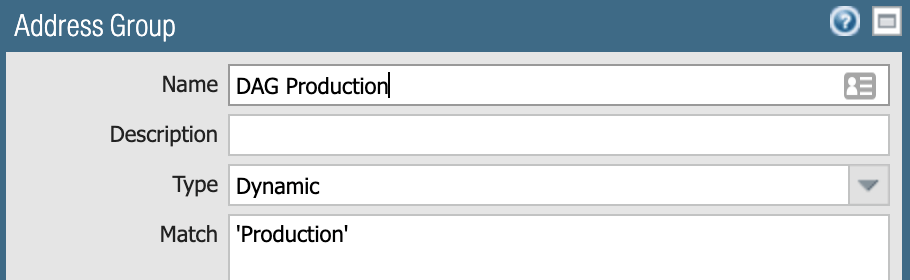
A DAG is created using matching criteria Production – all production workloads:
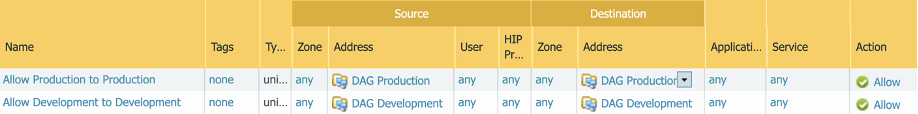
Policy created using the DAG to allow traffic between Development workloads and traffic between Production workloads:
API integration
The integration tool is part of Illumio’s Workloader tool, which can be downloaded from the Illumio Support Portal:

Workloader pushes labels and IP addresses paired with each managed workload to the Palo Alto Networks firewall, when issuing the dag-sync command:

The result is shown in the DAG membership on the Palo Alto Networks firewall, showing the IP addresses received from Illumio for the associated labels:
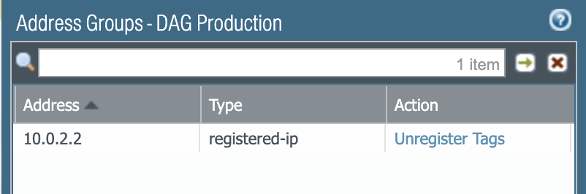
Updated DAG Development membership:
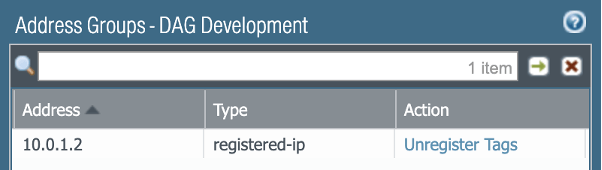
And that's it! The best part of the integration is that as the environment scales-up and scales-down, workloads are dynamically registered and unregistered, automatically changing membership to the DAG, triggering environmental segmentation policies automatically!
Amazing, isn’t it? Visit Illumio Support Portal to download the integration tool.
- Read our guide on Illumio + Palo Alto Networks
- Learn more about Palo Alto Networks NextWave Technology
.png)




.webp)
.webp)