Join Illumio for HIMSS 2023 in Chicago
Illumio is excited to be at HIMSS 2023 in Chicago on April 17-21. Find us in booth 2678.
- Register for the conference today
- Book a 1:1 meeting with Illumio experts by emailing [email protected]
- Learn more about Illumio at HIMSS, and
Looking for opportunities to network, socialize, and meet healthcare security experts while at the conference? Join us:
Illumio + Cylera Happy Hour
Moody Tongue Brewery Company
April 18th, 5-7:30 PM CT
2515 S Wabash Ave, Chicago, IL 60616
Register for the Happy Hour today, and read more about our integration with Cylera.
Healthcare cybersecurity is in critical condition
Ransomware attacks in healthcare increased by 328% in the first half of 2022, according to the HIPAA journal.
And the average cost of a breach in healthcare is $10.1m compared to an average of $4.35 million, according to the IBM Cost of a Breach Report 2022.
While the total number of attacks on critical infrastructure in general has increased, the growth in healthcare attacks is significantly higher. Even though many of the criminal gangs claimed that they would not attack healthcare targets the revenue potential combined with the more open nature of healthcare compared to other sectors proved too tempting.
Healthcare is a top cyberattack target
The very critical life or death environment of healthcare means that the long ransom negotiations that are possible in other sectors are not available to hospital owners. Paying up as soon as possible becomes the only option.
Additionally, a hospital's very open environment with significant public access creates attack vectors that potentially would not exist in other sectors.
All these things combine to make healthcare a very tempting target for bad actors.
Around the world, governments are working to boost the security of critical infrastructure. We see new legislation putting more focus on building plans to survive an attack and how to react. These include the new NIS2 directive in Europe, updates to SOCI in Australia, and new security legislation in Dubai and Japan.
While many see these government security directives as increasing the burden on already overstretched budgets and resources, in reality they’re an opportunity to simplify security approaches and reduce costs.
What to expect at HIMSS 2023
One of the most significant security threats to healthcare is the increased interconnectivity of medical devices with various IT systems. This potentially introduces another layer of cybersecurity complexity. However, by converging the functions of medical device management and IT security, a single Zero Trust approach can be applied across the entire system.
At this year’s HIMSS conference, expect to see an increased number of interconnected and smart systems to optimize the care delivered to patients. Many of these systems will connect to patient records systems that could be in the cloud. And access to systems and data could be by physicians located remotely.
These intricacies – and increased attack vectors – highlight the fact that it’s no longer sufficient to protect the network. Instead, the focus needs to shift to protecting resources.
Make sure to register for HIMSS 2023 to meet Illumio Zero Trust Segmentation experts. Learn how to contain the spread of breaches and ransomware and build cyber resilience. Feel confident that you can maintain patient care even in the event of a cyberattack.
Modern healthcare security: Get visibility and control access
All of the new security directives for critical infrastructure promote building a security approach based on risk. By understanding risk and vulnerabilities, it is easier to control the access any application, system, or device has to any other. Controlling this access allows security teams to control the impact of a cyberattack and maintain services.
There are 2 aspects to controlling access:
The first is who can talk to what. There are obvious steps like preventing anyone taking part in a spot of online shopping from the imaging system.
And with the modern way we work, there will be many more remote users, both physicians and patients, who will need access to information and resources. By making sure that these users only have access to the applications they need, the system will have some layer of protection. This role is performed by Zero Trust Network Access (ZTNA), but that is only part of the solution.
Once the connection is made, two new issues arise:
- Controlling the onward flow of any traffic
- Controlling how things communicate
If malware is innocently introduced into the system by a user, then we need to stop that attack from moving through the system.
Achieving this visibility is key. If we understand these three key aspects, we can make an informed decision on security policy:
- Which asset is connected to which other asset?
- What protocols do they need to communicate?
- What is the vulnerability of each asset?
With this information, it is possible to apply rules to stop the protocols used by ransomware from being allowed on assets where they are not needed. In the past, we would have used network-based technologies to try and achieve this, but with the modern environment, these techniques don’t scale and become complex to manage.
By being able to generate a map of all the connections of not just applications but also medical devices, we can see any potential risks caused by unauthorized connectivity.
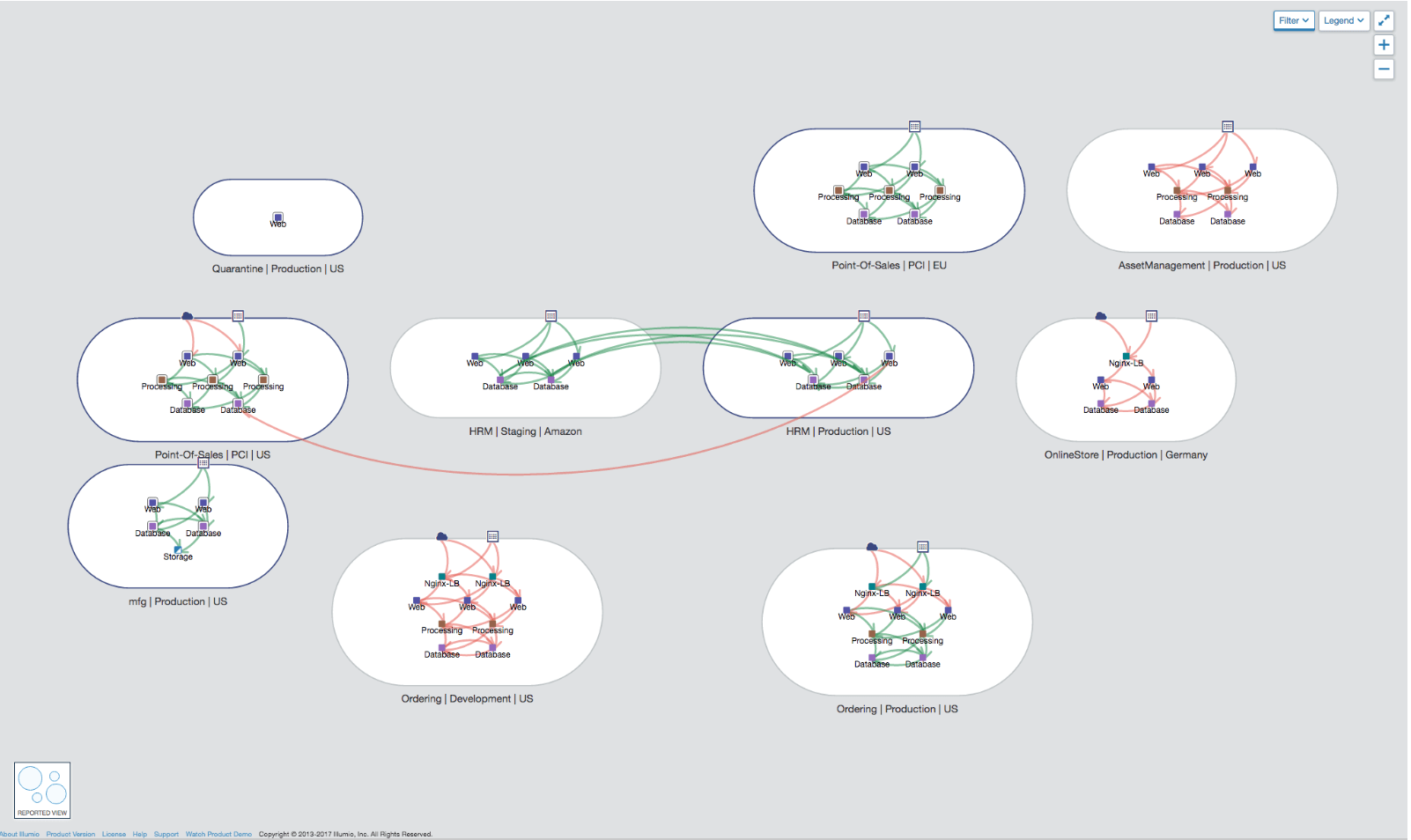
This map shows not just the interdependencies and protocols used but also integrations details on medical devices and the vulnerabilities of each device. This allows us to see the potential exposure of unpatched systems. Working on the “Now, Next, Never” approach to patching, we can apply rules to mitigate the threat posed to unpatched or unpatchable devices.
The thing we need to avoid when it comes to a cyberattack is stopping the delivery of services or moving patients to other facilities. By containing an attack at the source, we can make our hospitals resilient to attack and carry on saving lives.
Register for HIMSS 2023 today.
.png)


.webp)


