10 Reasons Schools and Districts Should Choose Illumio Zero Trust Segmentation
Cybercriminals are looking for vulnerable targets, including those who are lacking in sufficient resources to defend against breaches — and, unfortunately, schools and districts are near the top of that list.
Schools and districts often have insufficient or outdated cybersecurity measures in place, meager budgets, and limited security personnel. This leaves them underprepared for breaches or ransomware attacks that could halt operations, expose students’ and employees’ sensitive data, and cost millions of dollars in remediation.
Schools need to take proactive action to stop the spread of inevitable breaches. Building a Zero Trust security strategy is the first step. Zero Trust Segmentation (ZTS), also called microsegmentation, is foundational to a Zero Trust architecture. Learn more about implementing ZTS in your school or district in this guide.
Here are 10 reasons why schools and districts need to implement Illumio ZTS.
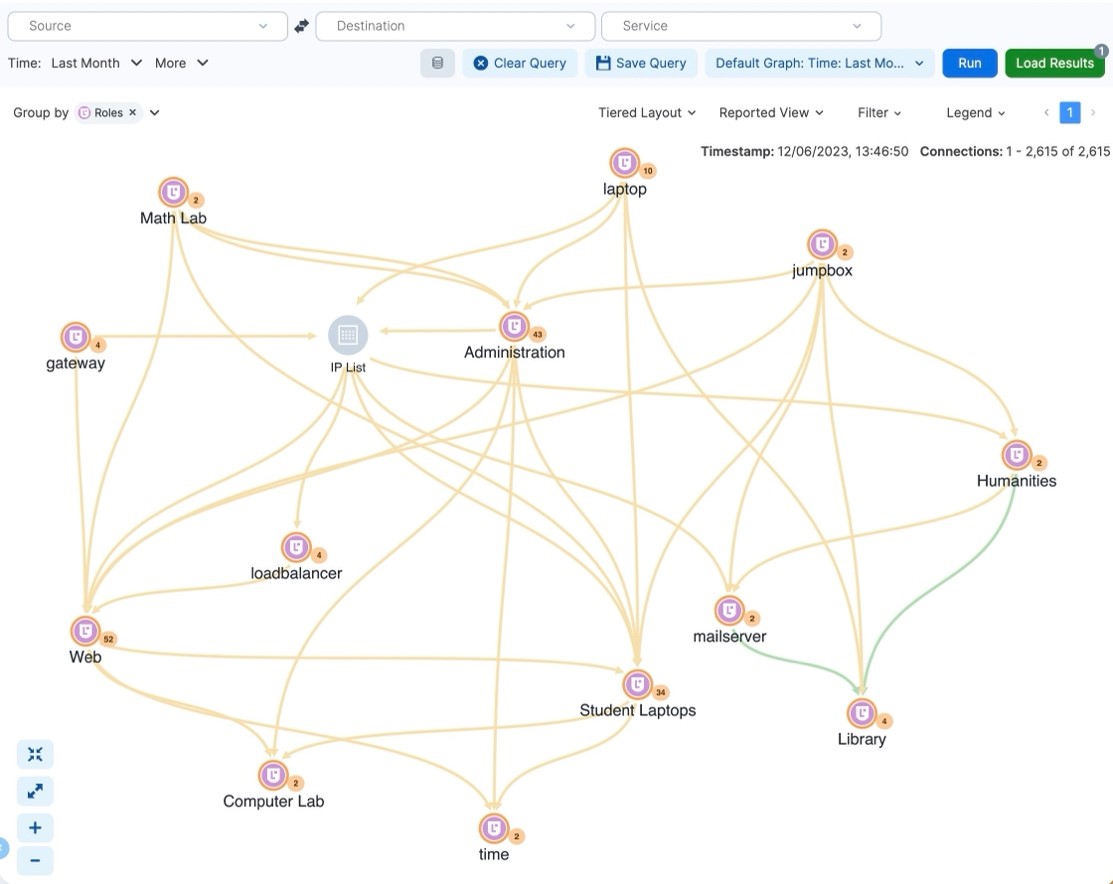
1. Complete visibility across all resources
You can’t enforce what you can’t see. The first step in securing your school compute resources is seeing all traffic across all resources. You need to be able to see all dependencies between all applications as well as between local resources and any deployed in the cloud.
Most schools have some basic division between academic and student resources, such as a switch or firewall deployed between them, or even an “air gap” between the two sets of resources. You need to be able to see what live traffic currently exists within each boundary and across them, if any.
Illumio delivers a comprehensive view of all traffic across all compute resources — across the entire school or district — revealing all dependencies between them. This end-to-end visibility can be an eye-opener: Students are often very creative at finding gaps in security solutions for “ethical hacking” or to engage in less than ethical intrusions. These are often the same security gaps used by external cybercriminals. Visibility is the first step in deciding what resources to segment from each other.
2. Protect critical data and resources
Once you get complete visibility into network connectivity, you can start securing your most important data, applications, systems, and resources with Illumio ZTS.
ZTS is foundational to any Zero Trust security architecture, allowing you to push the trust boundary directly to every workload without relying on any existing network boundaries or security appliances. You can segment anything from an entire school campus or district office all the way to a specific process on a specific workload in a school computer lab.
When breaches and ransomware attacks target your school or district offices – and they will – Illumio ZTS immediately contains the attack at its source, stopping lateral movement and limiting the attack’s impact across an entire school or district. During an active security breach, ZTS helps protect data and keep school operations up-and-running by helping school district IT teams understand access to systems, implement security policies to limit systems access, and report and analyze all traffic that doesn't match security rules.
3. Dramatically reduce ransomware risk
All attacks, including ransomware, share one thing in common: They like to move. Whether the breach is perpetrated by an international cybercrime gang or an aspiring student hacker, they all want to move between workloads as quickly as possible.
Nearly all ransomware attacks use a small set of known ports which are present in all modern operating systems, such as remote desktop protocol (RDP), server message block (SMD), and secure shell (SSH). Ransomware uses these open ports to establish connections laterally between resources and then quickly deliver their malicious payloads across as many resources as possible. This makes it easy for ransomware to spread quickly across a school or district — and can happen without the perimeter network firewall having any awareness or way to stop it.
And since most school networks are flat, with little if any network segments across a district, there are usually no barriers to this fast propagation. The lack of segmentation is equivalent to leaving all school doors unlocked during non-school hours, becoming easy targets for criminals. Segmentation is a basic requirement.
With Illumio ZTS, security teams can enable security policies that block all open ports on all resources across the entire school or district, and then only open ports selectively on specific compute resources to pre-approved destinations. This makes every compute workload, at any scale across the entire school or district, a segment, and each segment doesn’t trust any other segment by default. Any unknown compute resources that try to access the environment, such as a new student laptop, will be unable to connect to any resource by default since it will find itself surrounded by segments.
This default-deny policy dramatically reduces ransomware's ability to do damage. A school can actually experience a live security breach during school hours without risking a small problem quickly escalating into a disaster.
The goal is breach containment — schools and districts must assume that a breach will occur and at the worst possible time.
4. Test policies before deployment
With most schools and districts relying on limited budgets and personnel, it’s important that cybersecurity gets implemented right the first time — without the need for constant rollbacks and adjustments while remaining exposed to breaches.
Security teams can avoid this problem with Illumio’s simulation mode. Illumio will simulate the effects any new rules will have once deployed, prior to deploying them. This enables teams to modify and fine-tune policy while in simulation mode and not risk breaking anything during implementation.
This allows security teams to reduce the time spent on policy fixes, maintain positive relationships with application owners, and ensure security doesn’t impact school district operations.
5. Automate incident response to ransomware
In any security architecture, the slowest link in the workflow chain is between the keyboard and the chair. Most modern cyberattacks will spread faster than any human — and sometimes any detection tool — is able to respond to and contain the attack. Attack response requires an automated solution.
Illumio ZTS offers automated modification of policy changes from external sources through integration with SOAR solutions.
For example, if Splunk receives an alert about a new zero-day malware using a port which is currently allowed between workloads, Illumio’s SOAR plugin for Splunk will send API calls from Splunk to Illumio. Illumio will automatically deploy Enforcement Boundaries to close the port without requiring any manual intervention.
This enables the security solution to respond as quickly as malware tries to spread. The more complex the security solution, the more time is wasted trying to understand a breach before a policy decision is made. Breach containment needs to move as fast as the breach itself.
6. Get Zero Trust security for remote users

Most schools and districts enable students and staff to access resources remotely, usually with school-issued devices but sometimes with personal devices. This means that the security solution needs to assume that both legitimate — and illegitimate — traffic can come from anywhere and cannot assume that remote devices are secure by default.
Many schools are replacing legacy virtual private network (VPN) access with ZTNA (Zero Trust Network Access) solutions, but neither ZTNA nor VPNs alone can stop and contain the spread of breaches once they inevitably get past the perimeter. Security risks can reside inside the network just as easily as they do on the outside, and a school’s security strategy needs to be prepared for both possibilities.
By pairing ZTNA or VPN with Illumio ZTS, security teams can ensure that workloads have least-privilege access both at the network perimeter and inside the network. Illumio erects segments around every single school compute resource, and if the remote access boundary is breached and a resource is hijacked, Illumio will prevent that first resource from doing any damage to other resources. Illumio doesn’t replace remote access security, it completes it.
7. Secure legacy and end-of-life resources
Many schools and districts don’t have the luxury to continuously upgrade their compute resources every few years and need to rely on legacy and end-of-life resources that often don’t support third-party software security deployments. Or, even if deploying software is possible, there may be compliance regulations that prohibit it.
Illumio ZTS enables a Zero Trust security architecture with or without an agent, enabling a consistent Zero Trust security architecture across both modern and legacy resources.
Some schools, especially in higher education, will use legacy compute platforms such as mainframes for research purposes. Illumio can integrate directly with IBM hardware via security middleware such as Precisely. This enables Illumio to consume telemetry from the IBM server and then push policy directly to the server, enabling IBM hardware to be fully integrated into a complete Zero Trust security architecture along with laptops, VMs, bare metal machines, and cloud resources, all managed centrally.
Security management silos should be avoided, since management silos only increase the risk of a security breach spreading. Legacy hardware does not need to be managed as a silo, and Illumio enables centralized management operations across hybrid resources across an entire school or district.
8. Avoid legal consequences from paying ransom
When ransomware hijacks a school or district, the decision is often made to simply pay the ransom in order to resolve the problem as quickly as possible. This can easily seem like the lesser of two evils, but doing so runs the risk of violating government sanctions.
U.S. corporations, including schools and districts, risk federal legal consequences for “doing business” with terrorists if they transfer ransom money to any countries on the U.S. government’s Office of Foreign Assets Control Sanctions List. This means that if money moves from a school district into the hands of international crime rings, a school district’s good intentions can run the risk of violating government sanctions.
Illumio ZTS contains ransomware attacks, limiting their effectiveness and stopping attackers from accessing the data and resources schools and districts need to maintain services. This gives security personnel time to remediate after a breach rather than being pressured to pay a ransom quickly to get school resources back online.
9. Fulfill compliance requirements
.webp)
Nearly all schools and districts fall under some kind of regulations that require compliance to security requirements. For example, the US Department of Education publishes a summary of Data Security requirements for K-12 and Higher Education, including FERPA (Family Educational Rights and Privacy Act) and CIPA (Children’s Internet Protection Act).
These compliance requirements apply to securing student education records and reliably blocking internet access to material harmful to children. With Illumio ZTS, schools and districts can maintain a security barrier around every single school compute resource, with a default-deny policy ensuring that a security breach will encounter a significant barrier to overcome.
Illumio ZTS is a significant first step in a school or district guaranteeing compliance with US Department of Education security guidelines.
10. See efficient, measurable ROI
With limited funding and resources, it's more important than ever that schools and districts can ensure maximum return on their security investment. Budgets are real, and schools need to be able to deploy security solutions with realistic ROI.
The Illumio ZTS Platform provides reliable, scalable, and fast breach containment, giving you the peace of mind that security breaches won't become disasters. Research from Enterprise Security Group (ESG) shows that organizations, including education, who have adopted ZTS are able to avert five cyber disasters annually, can accelerate 14 more digital transformation projects, and are 2.7 times more likely to have a highly effective attack response process. Read how Illumio customers are seeing reliable security ROI.
Start implementing Illumio ZTS in your school or district today. Learn more in this guide.
Ready to learn more about Illumio ZTS? Contact us today for a free consultation and demo.
.png)



.webp)
.webp)
.webp)