The Evolution of Adaptive Segmentation
I believe that innovation comes from people who have an unstoppable drive to improve the world and are placed in an environment with constrained resources. This is why top sports players have their best games when playing against the most challenging opponents. And “threading the needle” wouldn't mean much if the eye of the needle wasn’t so tiny. It is exactly these challenging and constrained environments that innovators who have it in their veins look for, and are the cauldron from where innovations are conceived.
The Illumio journey started in such an environment (as many successful startups do).
For us, it began in a world where choke-point firewalls were not able to keep up and deliver security segmentation that was sufficiently dynamic to keep up with today’s modern data center and distributed application needs. Dev ops, microservice architectures, public cloud, and containers are all parts that fueled the evolution of the dynamic and distributed data center, but were causing strain and tension on those traditional security segmentation solutions.

Illumio’s initial innovation around the Adaptive Security Platform (ASP) came to address those challenges directly. Some key foundational elements were identified that would allow us to build our solution:
- First, rich telemetry from the endpoint servers was critical to providing our policy engine enough context to help end users drive decisions and data visualizations.
- Second, a metadata-driven policy model that allowed people to describe policy in a rich and abstract way, and to build simple models of how applications should be segmented and secured.
- Third, a fully distributed policy enforcement point fabric that could be bound to the workload, and allow it to work seamlessly across multiple infrastructure types, bare-metal, virtualized, and cloud environments.
It was with those key insights and components on which we built the ASP and brought it to customers.
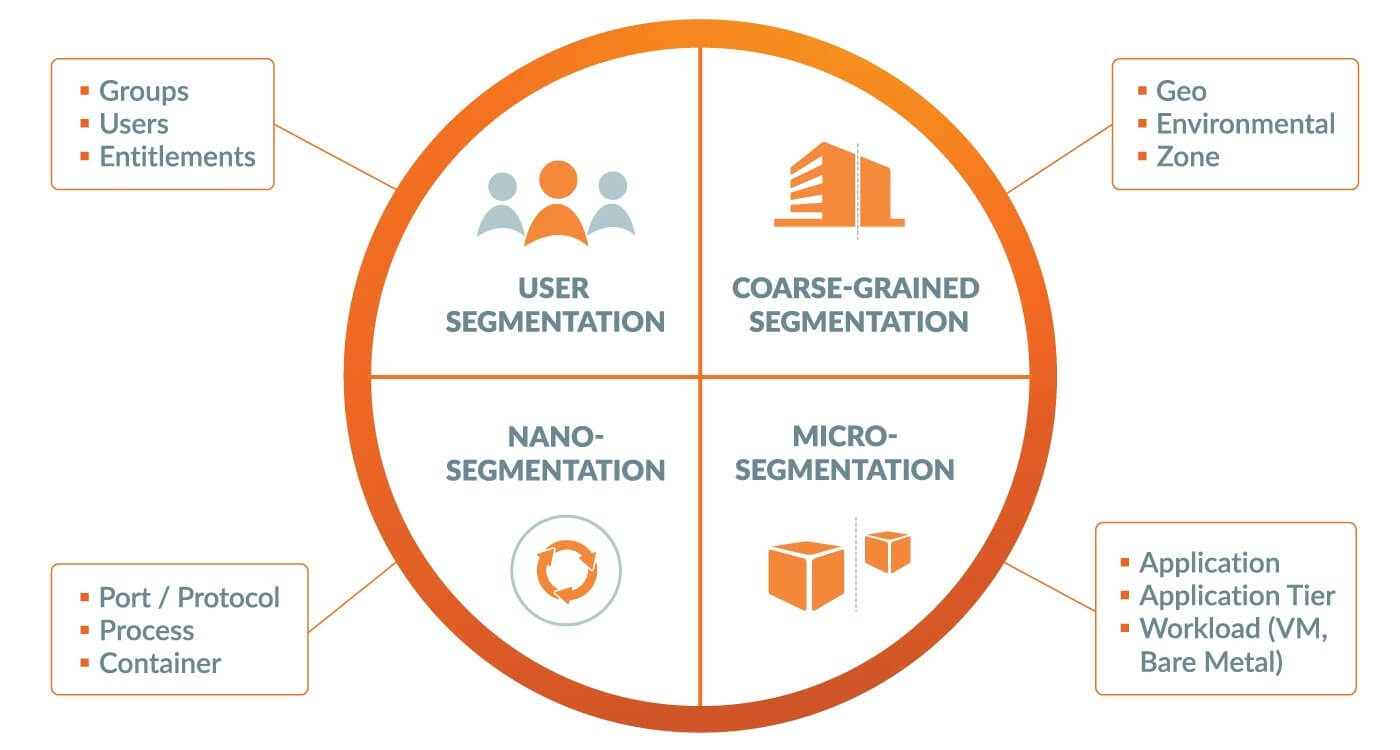
The next phase of the journey was to understand that adaptive segmentation itself was more than just being dynamic and flexible, adjusting to the different ways applications were being deployed. It was understanding that adaptive segmentation is many tools, and ensuring that each tool is the right one for a different type of job. Customers needed:
- Coarse-grained segmentation: The ability to logically separate environments or zones that were mixed in large, flat networks.
- Micro-segmentation: This ranges from the classic definition of application-level segmentation, down to even finer grain app tier segmentation, or individual workload segmentation.
- Sub-workload segmentation (a.k.a. nano-segmentation): This provides the ability to control and segment down to actual processes inside an OS. This also extends to segment Kubernetes Pods or Docker Containers.
- User segmentation: Which we introduced last year, where a user can be logically segmented with all of their entitled applications, while cloaking the other (unauthorized) applications and minimizing risk to the enterprise.
Range of Adaptive Segmentation by Illumio
What has become obvious to us is that the flexibility and simplicity of the metadata-driven policy model coupled with the distributed and dynamic architecture of the Policy Compute Engine (PCE), the "brain" of the Illumio platform, is powerful. The PCE's declarative policy models and the intelligence to adapt to change – allowing applications to scale or new instances to be deployed without any additional work – is driving people to ask us for the next phase of the journey: coordinated controls across multiple policy enforcement points.
The future for the platform is to embrace network and cloud-based enforcement controls. To bring the simplicity and intelligence that the PCE brought to host-based controls to network infrastructure from Cisco and Arista, as well as Amazon and Microsoft Azure Security Groups, in a coordinated and unified way.
This is the power of a good abstraction.
Learn more about how Illumio is extending the Adaptive Security Platform: Visit Booth N2900 at RSA Conference 2017.
.png)

.webp)
