Understanding EU Compliance Mandates Series: Financial Services
In part one of this blog series, I discussed the compliance landscape and how different industries each have their own governing mandates or guidance on cybersecurity. This was followed by a post on regulation and security controls in the Critical Systems and Operational Technology sector, an area I’ve had direct experience within, and one that fascinates me as cybersecurity develops there.
Moving to (in some ways) the polar opposite industry type, here, I will expand on some of the EU and European-specific mandates applying to financial institutions and banks. While we have global mandates regarding SWIFT CSP and PCI-DSS covered in depth elsewhere – following the theme of this series, I’ll be concentrating on the controls and guidance that applies to the EU specifically. For many, the influence of these mandates shapes some of the largest IT security projects in Europe.
As before, let’s first define some acronyms:
- FMIs – Financial Market Infrastructures. These are the systems that underpin the banking process itself.
- CPMI – The Committee on Payments and Market Infrastructures. The CPMI is an international body that makes recommendations promoting the safety of payment, clearing, and settlement systems, and providing oversight.
- IOSCO – International Organization of Securities Commissions. This is the body that regulates the global securities and futures markets.
- ECB – The European Central Bank. The central bank for the 19 EU countries that have adopted the Euro as a common currency.
- SIPS – Systemically Important Payment Systems. I’ll go into detail specifically on this below, but suffice to say that this includes a shortlist of international backbone payment systems used by most banks.
Before moving forward, let’s dig into SIPS for a moment. SIPS are major payment systems that typically have country-wide implications should they fail. In the case of those defined here, they have at least European-wide scope as opposed to individual countries, and in many cases are global in their reach and use.
The primary systems that the are under the relevant guidance are TARGET2, EURO1, and STEP2-T. Under the SIPS Regulation, the ECB is responsible for overseeing these three systems. In addition, the ECB and the Nationale Bank van België/Banque Nationale de Belgique are responsible for overseeing the Mastercard Clearing Management System SIPS, and the Banque de France is responsible for overseeing CORE(FR).
As a global example, the U.S. Federal Reserve System has accepted primary oversight responsibility for the CLS system, leading a cooperative oversight framework in which the ECB participates, together with the G10 national central banks. Within the Eurosystem, the ECB has primary responsibility for the settlement of euro-denominated payments by CLS, in close cooperation with other Eurosystem central banks.
Core principles for systemically important payment systems
To be classified as SIPS, a system must follow the below guidelines. These are sometimes referred to as the “10 Commandments” in banking circles:
- A well-founded legal basis.
- Rules and procedures which enable participants to have a clear understanding of the system’s impact on each of the financial risks they incur through participation in it.
- Clearly defined procedures for the management of credit risks and liquidity risks, which specify the respective responsibilities of the system operator and the participants and which provide appropriate incentives to manage and contain those risks.
- Prompt final settlement on the day of value, preferably during the day and at a minimum at the end of the day.
- Where multilateral netting takes place, it should, at a minimum be capable of ensuring the timely completion of daily settlements in the event of an inability to settle by the participant with the largest single settlement obligation.
- Assets used for settlement should preferably be a claim on the central bank; where other assets are used, they should carry little or no credit risk and little or no liquidity risk.
- A high degree of security and operational reliability, and contingency arrangements for timely completion of daily processing.
- Practical for its users and efficient for the economy.
- Objective and publicly disclosed criteria for participation, which permit fair and open access.
- Governance arrangements which are effective, accountable and transparent.
I’ve highlighted the seventh entry on the list, as this is the part that flows into the surrounding guidance on cybersecurity which we’ll be focusing on.
To help provide instruction on how to secure these SIPS, in 2016 the CPMI alongside IOSCO put together the Guidance on Cyber Resilience for financial market infrastructures (Guidance). This contains detailed guidance on securing systems of this magnitude and impact, and defines a number of key areas of focus, along with measurement strategies.
For example, some of the high-level security sections include:
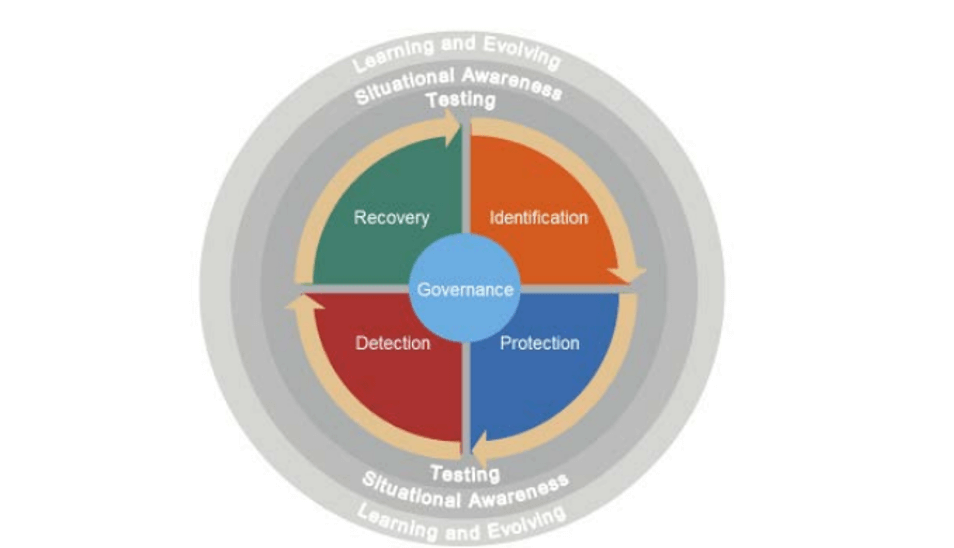
Identification: This concerns an organization’s ability to determine which systems need protecting in the first place. This includes business functions, process, assets and information. Correct identification allows for the prioritization of the next efforts.
Key to improvements in this area are the rapid identification of the high-value systems and the dependencies that they have established. In the vast majority of cases, these systems already exist as complex, brownfield environments where there is significant work needed to identify all critical dependencies and paths.
Protection: Once identified, how to implement effective controls with the aim of protecting critical systems from cyber attack and compromise.
For me, Zero Trust plays a key part here. By adopting as close to a default-deny architecture as possible, protection is inherent, and the scope for attack is reduced. In addition, the blast radius of any successful compromise is inherently smaller.
Detection: Being pragmatic, this outlines detection methods, containment, and mitigation tactics that should be used in the event of a successful attack against an in-scope system.
Connected directly to the identification and protection pieces, detecting an attack is much more straightforward if we have already established normal behavior, and put in place a default-deny configuration by means of the network, applications, and user access.
Testing: As an addendum, the testing section includes how best to prepare and test systems involved in the previous three sections and configure them in a resilient way through repeated attestation to withstand attack.
I’ve written previously on the mapping across of these sections using Illumio to help identify critical applications and flows, protect from attack by virtue of a Zero Trust policy architecture, detect changes in application behavior, and lastly help organizations in scope of the guidance attest to a secure configuration.
As an extremely helpful development on top of the original work, in 2018 the ECB itself published an addition titled Cyber Resilience oversight expectations for financial market infrastructures (CROE), which gives additional guidance on steps to implement the recommendations, mapping across the more abstract concepts to clear, real-world technological examples, and lastly – providing defined expectations in terms of how an FMI might be measured for success.
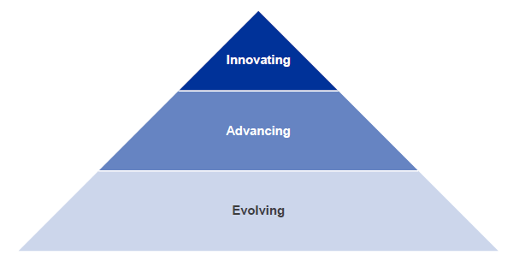
The CROE encourages inter-FMI communication to help improve security across all institutes, and still refers to the three measurement levels outlined in the original 2016 paper, namely:
Evolving: Essential capabilities are established, evolve, and are sustained across the FMI to identify, manage, and mitigate cyber risks, in alignment with the Cyber Resilience strategy and framework approved by the Board. Performance of practices is monitored and managed.
Advancing: In addition to meeting the evolving level’s requirements, practices at this level involve implementing more advanced tools (e.g., advanced technology and risk management tools) that are integrated across the FMI’s business lines and have been improved over time to proactively manage cyber risks posed to the FMI.
Innovating: In addition to meeting the evolving and advancing levels’ requirements, capabilities across the FMI are enhanced as needed within the rapidly evolving cyber threat landscape, in order to strengthen the FMI’s Cyber Resilience and its ecosystem and by proactively collaborating with its external stakeholders. This level involves driving innovation in people, processes, and technology for the FMI and the wider ecosystem to manage cyber risks and enhance Cyber Resilience. This may call for new controls and tools to be developed or new information-sharing groups to be created.
To sum it up
Both documents and my experience speaking to the responsible teams show that the understanding around the impact of these systems on every-day life (namely the potential for catastrophic country and even global effects if the system are compromised) is increasing significantly. I find it telling that these developments are still very recent, and implementation of the guidance is potentially just starting. That said, and as mentioned in the first part of this article, I have seen first-hand the way that these guidelines are shaping high-level, decade-long IT and IT security projects: determining the types of systems implemented, their mapping across to the key measurable areas of the documents, and the way that the systems themselves are designed and architected.
At Illumio, we focus on three key areas that map directly to both documents, namely Identification by means of our Application Dependency Mapping. This gives organizations the ability to work with real-time maps of their critical systems and applications, and establish the normal dependencies and application flows between them. It also allows the accurate scoping of the required boundaries for the next section – Protection.
The Illumio platform is inherently Zero Trust in its nature. Policy can be defined that allows only the necessary application flows, massively limiting potential compromise paths and lateral movement. The combination of the mapping and policy configuration allow for the easy Detection of threats, the third key pillar, through the surfacing of new attempted communication paths, a change in application workload behavior, and the ability to quickly and safely quarantine compromised workloads.
For more on how Illumio protects financial services organizations, check out this solutions page. And please join me next time for thoughts on some of the other mandates across the EU – such as GDPR and TSR!
.png)

_(2).webp)
.webp)