Enforcement Boundaries: 7 Use Cases Beyond Ransomware
Enforcement Boundaries are the Swiss Army knife of risk reduction. Those famous red tools can do much more than slice some cheese and apple, and Enforcement Boundaries can do much more than just fight ransomware.
In a previous blog post, we explained how Enforcement Boundaries can help you fight ransomware — both proactively and reactively. Now, we’d like to show you other use cases for this innovative approach to Zero Trust.
Enforcement Boundaries work by creating a virtual firewall around every operating system or application instance. Essentially, they transform workloads into Zero Trust segments. That lets you place a protective perimeter around any port, workload, group of workloads or IP range. And you can do this far more quickly and easily than you could with a full-fledged Zero Trust setup.
Here’s our list of seven ways that, in addition to fighting ransomware, you can use Enforcement Boundaries:
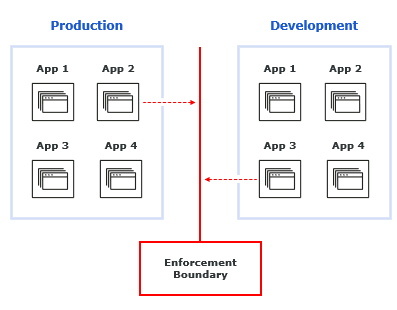
1. Separate environments
A two-way Enforcement Boundary can create a virtual wall between two environments. That’s especially helpful for separating production, which handles customer data, and development, which doesn’t.
These two environments generally should not talk. For example, in a hospital setting, you wouldn’t give developers access to patient information. The traditional approach has been to put different devices on different network segments. But this assumes that the device and its IP address are constant, an assumption that today is no longer safe to make.
Once an Enforcement Boundary is in place, data flows within each environment continues normally, and team members can work unimpeded. But no flows can cross the defined boundary — unless explicitly defined in the allow list.
2. Isolate new environments
When a business is acquired or merged, the acquiring organization may wish to limit the new unit’s data flows. An Enforcement Boundary can be used to ensure that only very specific traffic is permitted to cross over from the new subsidiary.
That could mean letting the newly acquired company’s legal team communicate with the acquiring company’s legal team. But it could also mean that all other intra-company traffic is blocked.
3. PCI-DSS segmentation
The Payment Card Industry Data Security Standard (PCI-DSS) dictates that controls be placed around the cardholder data environment (CDE) to ensure that payment card data is contained.
To quickly comply, an organization can define an Enforcement Boundary between its collection of PCI-DSS applications and other systems. This will block all traffic from passing from the CDE to outside the CDE — except for any specific flows the organizations adds to its allow list.
4. Lock admin access to jump hosts
A jump host is a system on a network used to manage devices in a separate security zone. Once an admin logs into a jump host, they can then log into other servers. For this reason, an organization wants to ensure that only known system administrators can gain use the admin access protocols.
An Enforcement Boundary can help by separating production, test, integration and development groups. This uses adaptive user segmentation to limit access to internal apps based on Active Directory memberships.
The Enforcement Boundary can also limit access to both Remote Desktop Protocol (RDP) and Secure Shell (SSH). Access can then be granted to specific groups only.
5. Inbound-only enforcement
An Enforcement Boundary can be used to set a one-way data flow. This can help during the start of a segmentation project, when the organization defines who and what can gain access to protected applications.
The complicating factor is that these applications may consume data from other applications that are not in scope. That can require organizations to set an outbound policy, creating extra work.
An Enforcement Boundary can eliminate that requirement by allowing only inbound flows to the protected application.
6. Control IT/OT connectivity
There are critical assets inside organizations that are urgent targets for protection. These could have virtual enforcement nodes (VENs) installed.
An Enforcement Boundary can be applied between unmanaged workloads and a defined set of VENs. For example, an organization with a mainframe system could use an Enforcement Boundary to block connections between that system and unauthorized apps.
7. Isolate east-west traffic inside a DMZ
Although most demilitarized zones (DMZs) are connected to firewalls, criminals can use compromised DMZ hosts to pivot to other hosts in the same zone.
An Enforcement Boundary can help by separating all workloads inside the DMZ. Then traffic can pass only if it meets two tests: One, it complies with the defined allow list. And two, it lets other application policies be reviewed and attested to in a more appropriate timescale.
Illumio's approach
Illumio’s "enforce and expand" approach with Enforcement Boundaries is fast and easy to deploy. Whereas an allow-list policy must be perfect before it can be enforced, by contrast, Enforcement Boundaries can be set, deployed and enforced in mere minutes to hours.
Illumio uses a declarative model that lets you define only the “what” – that is, what you want to block — leaving Illumio to take care of the “how.” It’s like asking an Alexa device, “Play music.” You don’t need to know how the system works, just what you want it to do.
You can also test and simulate Enforcement Boundaries before deploying — say goodbye to “deploy and pray” and hello to “this just works.”
To learn more about how Illumio Core accelerates workload security:
- Check out "Simplified Zero Trust Segmentation With Illumio."
- Watch the webinar, Automated Enforcement Advances: Protecting Against Ransomware and Cyberattacks.
.png)


