Comprendre les mandats de conformité de l'UE : RGPD, Cyber Essentials
In part one of this blog series, I discussed the compliance landscape and how different industries each have their own governing mandates or guidance on cybersecurity. This was followed by a post on regulation and security controls in the Critical Systems and Operational Technology sector, an area I’ve had direct experience in and one that fascinates me as cybersecurity develops there. From there, I moved to the financial services regulations present in the EU.
Here, we’ll be moving to a slightly tangential mandate, GDPR, and also looking at Cyber Essentials/Cyber Essentials Plus as a set of NCSC (UK National Cyber Security Centre) guidelines on cybersecurity.
The General Data Protection Regulation - GDPR
Many of you are familiar with the General Data Protection Regulation (GDPR) - whether it directly impacts your life and work in the EU, or as it applies to the data we work with and systems we interact with.
Without going into too much detail, GDPR primarily focuses on data protection, data handling, and privacy concerns for EU citizens’ Personally Identifiable Information (PII). The core tenets provide individuals control over their data, and mandate that the controllers and processors of data put in place “appropriate technical and organizational measures” to implement the data protection principles. Launching back in the Spring of 2018, and applicable across all organisations that handle the EU citizens’ data, GDPR is wide-ranging but aims to unify control of PII as a regulation (control) rather than a directive (guidance).
Fundamentally, GDPR means a few things for cybersecurity practitioners. Specifically, organisations need to:
- Manage security risk
- Protect personal data against cyber attack
- Detect security events
- Minimise the impact
These can be addressed in a number of ways, including the implementation of Cyber Essentials guidelines in the UK, which we’ll discuss later in this post.
For now, I’d like to dig into how we interpret and apply the requirements, specifically through the lens of micro-segmentation, breach-prevention, and the reduction of lateral movement.
Core GDPR principles and how Illumio helps
There are a number of guidelines you can use to help meet GDPR standards from a cybersecurity perspective, outlined in the NCSC GDPR Security Outcomes guide. Of these, a number of specific requirements very much come under the remit of micro-segmentation:
A) Manage security risk
You have appropriate organisational structures, policies, and processes in place to understand, assess and systematically manage security risks to personal data
Specifically:
A. 3 Asset management
This requirement deals typically with the data itself under GDPR, but the data-handling/data-hosting systems themselves can be visualised and mapped, and subsequently segmented appropriately to prevent untoward access or compromise.
A. 4 Data processors and the supply chain
You understand and manage security risks to your processing operations that may arise as a result of dependencies on third parties such as data processors. This includes ensuring that they employ appropriate security measures.
Application dependency mapping, via Illumination, is a primary function of Illumio Core and enables better understanding of your organization’s connectivity to external systems.
B) Protect personal data against cyber attack
You have proportionate security measures in place to protect against cyber attack which cover the personal data you process and the systems that process such data.
Similar to above, the core guideline here is around prevention of cyber-attack, ergo – the prevention of successful lateral movement into the systems that hold data governed under the GDPR. This is exactly what micro-segmentation protects against.
C) Detect security events
You can detect security events that affect the systems that process personal data and you monitor authorised user access to that data
C.1 Security monitoring
You appropriately monitor the status of systems processing personal data and monitor user access to that data, including anomalous user activity.
Again, application dependency mapping comes into its own here. Monitoring of the application flows into and out of critical applications or systems is extremely powerful when monitoring for compromise or a change in behaviour. Coupled with the ability to integrate with systems such as SIEMs and SOARs, it allows for rapid reaction to attacks, such as the quarantine of a device seen to be compromised.
For organizations adopting a Zero Trust posture, Illumio policies puts an organisation on the front-foot before an attack even has a chance to establish itself, and inherently protects critical systems from the lateral movement to compromise chain.
D) Minimise the impact
You can:
Minimise the impact of a personal data breach
Restore your systems and services
This deals with blast radius, specifically the understanding and minimisation of it. Again, referencing systems here specifically as opposed to data itself.
To help meet these requirements, there are a number of specific guideline sets that can be referenced, and even whole organisation dedicated to consulting on and providing direction on meeting GDPR compliance standards. One such set of guidelines that can be referenced as a starting point in the UK is Cyber Essentials, and it’s externally-audited version, Cyber Essentials Plus:
Cyber Essentials, Cyber Essentials Plus
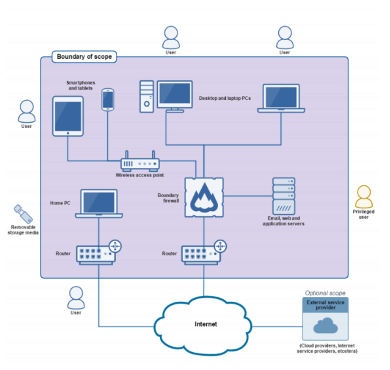
Cyber Essentials is an NCSC-published set of simple cybersecurity guidelines, that any organisation can use to help protect their organisation, and can help when trying to meet GDPR, or otherwise. Cyber Essentials itself is a self-assessment option, with Cyber Essentials Plus available as an externally-validated version. Requirements are the same for both, only the method of attestation changes.
Scope can include the entire IT infrastructure – or a sub-set. Web applications are in-scope by default.
As of Version 2.1 – August 2020, the specific requirements revolve around a few key areas:
- Firewalls
- Secure Configuration
- User Access Control
- Malware Protection
- Patch Management
Of these, there are three primary sections that Illumio can help with: firewalling, secure configuration, and malware protection. Some aspects of user access control can also be addressed with the Illumio Adaptive User Segmentation functionality.
Firewalls
All devices run network services, which create some form of communication with other devices and services. By restricting access to these services, you reduce your exposure to attacks. This can be achieved using firewalls and equivalent network devices.
A boundary firewall is a network device which can restrict the inbound and outbound network traffic to services on its network of computers and mobile devices. It can help protect against cyber attacks Cyber Essentials: Requirements for IT infrastructure by implementing restrictions, known as ‘firewall rules’, which can allow or block traffic according to its source, destination and type of communication protocol.
Alternatively, a host-based firewall may be configured on a device. This works in the same way as a boundary firewall but only protects the single device on which it is configured. This approach can provide for more tailored rules and means that the rules apply to the device wherever it is used. However, this increases the administrative overhead of managing firewall rules.
Illumio primarily makes use of the host-based incumbent OS firewall, and programs it in such a way to easily achieve a dynamic, Zero Trust security posture. Making use of existing, individual firewalls allows for a very granular policy, close to the device and data that needs to be protected.
Secure configuration
Computers and network devices are not always secure in their default configurations. Standard, out-of-the-box configurations often include one or more weak points such as:
- an administrative account with a predetermined, publicly known default password
- pre-enabled but unnecessary user accounts (sometimes with special access privileges)
- pre-installed but unnecessary applications or services
Default installations of computers and network devices can provide cyber attackers with a variety of opportunities to gain unauthorised access to an organisation’s sensitive information — often with ease.
Again, here Zero Trust as a policy model massively increases the security of a given workload – and minimises the access to “unnecessary applications or services” mentioned.
Malware protection
The execution of software downloaded from the Internet can expose a device to malware infection.
Malware, such as computer viruses, worms and spyware, is software that has been written and distributed deliberately to perform malicious actions. Potential sources of malware infection include malicious email attachments, downloads (including those from application stores), and direct installation of unauthorised software.
With this guidance, both Illumio Core et Illumio Edge aident à empêcher le mouvement latéral d'une infection par un logiciel malveillant, en minimisant le rayon d'explosion et en empêchant la compromission ultérieure des applications métier critiques.
En conclusion
Dans les cas de contrôle et de guidage, l'interprétation est souvent cruciale. Le RGPD est connu pour être difficile à interpréter et à mettre en œuvre, avec une orientation relativement ouverte en ce qui concerne les moyens spécifiques d'atteindre les objectifs requis. Les amendes liées au RGPD tiennent compte de l'intention et des efforts requis pour répondre aux exigences, en plus des détails techniques des contrôles mis en œuvre.
De même, Cyber Essentials fournit un aperçu de base de la manière de renforcer la sécurité, mais propose plusieurs moyens d'y parvenir. La visibilité granulaire offerte par le mappage des dépendances des applications et la posture de sécurité Zero Trust (refus par défaut) rendue possible grâce à Illumio aident les entreprises à atteindre un niveau très élevé pour respecter ces deux ensembles de directives de sécurité.
Pour en savoir plus sur l'approche Zero Trust d'Illumio, rendez-vous sur https://www.illumio.com/solutions/zero-trust.
.png)


